Proposal for Random Access Efficiency Enhancement in IEEE 802.11be Networks
This document presents a proposal for enhancing random access efficiency in IEEE 802.11be networks through a Random-Access NFRP (RA-NFRP) principle. The proposal addresses the challenges of low efficiency in the current UORA procedure and introduces modifications based on the 802.11ax standard to im
5 views • 16 slides
Understanding Bluetooth Low Energy Addresses in IEEE 802.11-21/1535r0
The document explores the features of resolvable addresses in Bluetooth Low Energy (BLE) within the IEEE 802.11-21/1535r0 standard. It discusses the two types of addresses in BLE, Public and Random, and their usage. The emphasis is on Random addresses due to their popularity and privacy features. Th
2 views • 11 slides
Understanding Random Forests: A Comprehensive Overview
Random Forests, a popular ensemble learning technique, utilize the wisdom of the crowd and diversification to improve prediction accuracy. This method involves building multiple decision trees in randomly selected subspaces of the feature space. By combining the predictions of these trees through a
1 views • 21 slides
Simplifying Random Assignment with The Cambridge Randomizer
The Cambridge Randomizer offers a cost-effective and efficient solution for random assignment in research studies, enabling treatment providers to conduct the process securely. This innovative online portal streamlines the assessment of participant eligibility, provides instant baseline data, and en
0 views • 8 slides
Importance of Timely Verification in Care After Death
Understanding the verification process and importance of timely verification in care after death is crucial for improving the experience of death and dying for families. This session covers the definitions, process, and care after death, emphasizing the significance of timely verification in end-of-
1 views • 15 slides
High-Throughput True Random Number Generation Using QUAC-TRNG
DRAM-based QUAC-TRNG provides high-throughput and low-latency true random number generation by utilizing commodity DRAM devices. By employing Quadruple Row Activation (QUAC), this method outperforms existing TRNGs, achieving a 15.08x improvement in throughput and passing all 15 NIST randomness tests
0 views • 10 slides
Electors Verification Programme Overview
The Electors Verification Programme (EVP) is a campaign initiative encouraging citizens to verify and authenticate electoral details, including family members. Various methods such as NVSP, Mobile App, and 1950 helpline are utilized for verification. Citizens can also submit details through BLOs to
1 views • 25 slides
Understanding Random Variables and Their Applications in Various Fields
Random variables play a crucial role in statistics, engineering, and business applications. They can be discrete or continuous, depending on the nature of the outcomes. Discrete random variables have countable values, while continuous random variables can take on any real number. This article explor
0 views • 6 slides
Criticisms and Defenses of Verification and Falsification Principles
Explore the criticisms and defenses of the Verification and Falsification Principles in religious language. Understand how believers defend the use of religious language and analyze challenges posed to the Verification Principle by notable thinkers like Swinburne, Hare, and Mitchell. Delve into resp
2 views • 15 slides
Understanding Random Variables and Probability Distributions
Random variables are variables whose values are unknown and can be discrete or continuous. Probability distributions provide the likelihood of outcomes in a random experiment. Learn how random variables are used in quantifying outcomes and differentiating from algebraic variables. Explore types of r
0 views • 13 slides
Integrated Verification and Repair in Control Plane
Modern networks face challenges from incorrect configurations affecting millions of users. This presentation discusses the integration of verification and repair processes into the control plane, aiming for consistent and policy-compliant network operations. It explores the complexities of network c
0 views • 16 slides
Formal Verification and Automata Abstraction in Esterel
This content delves into the applications of formal verification and automata abstraction in Esterel, focusing on techniques such as verification by abstraction of automata, boolean verification using BDDs, bounded model checking in SAT/SMT, and more. The work of Gérard Berry at the Collège de Fra
0 views • 38 slides
Program Verification via an Intermediate Verification Language
Dive into the world of program verification through an intermediate verification language with a focus on static program verification, reasoning about programs, and separation of concerns. Explore tools like Dafny and verification architectures like Boogie and Why3, along with key concepts including
0 views • 36 slides
Advanced Imputation Methods for Missing Prices in PPI Survey
Explore the innovative techniques for handling missing prices in the Producer Price Index (PPI) survey conducted by the U.S. Bureau of Labor Statistics. The article delves into different imputation methods such as Cell Mean Imputation, Random Forest, Amelia, MICE Predictive Mean Matching, MI Predict
0 views • 22 slides
Efficient Billion-Scale Label-Constrained Reachability Queries
Graph data sets are prevalent in various domains like social networks and biological networks. Label-Constrained Reachability (LCR) queries aim to determine if a vertex can reach another vertex through specific labeled edges. Existing works utilize exhaustive search or graph indexing techniques, but
0 views • 13 slides
Understanding Electron-Phonon Interactions in Iron-Based Superconductors
This discussion explores the effects of electron-phonon interactions on orbital fluctuations in iron-based superconductors. Topics covered include ab initio downfolding for electron-phonon coupled systems, evaluation methods such as Constrained Random Phase Approximation (cRPA), Constrained Density-
0 views • 12 slides
Understanding Random Class in Java Programming
The Random class in Java is used to generate pseudo-random numbers. By utilizing methods such as nextInt and nextDouble, you can generate random integers and real numbers within specified ranges. This chapter explores common usage scenarios, such as generating random numbers between specific ranges
2 views • 10 slides
Software Bugs and Formal Verification in Critical Systems
Software bugs have caused catastrophic events like radiation overdoses and rocket explosions, emphasizing the importance of formal verification in ensuring software correctness. Formal verification uses mathematical models to prove software correctness, offering higher assurance, especially in safet
0 views • 26 slides
Understanding Random Sampling in Probabilistic System Analysis
In the field of statistical inference, random sampling plays a crucial role in drawing conclusions about populations based on representative samples. This lecture by Dr. Erwin Sitompul at President University delves into the concepts of sampling distributions, unbiased sampling procedures, and impor
0 views • 23 slides
Quantum Key Agreements and Random Oracles
This academic paper explores the impossibility of achieving key agreements using quantum random oracles, discussing the challenges and limitations in quantum communication, cryptographic protocols, quantum computation, and classical communication. The study delves into the implications of quantum ra
0 views • 29 slides
Approximate Inference in Bayes Nets: Random vs. Rejection Sampling
Approximate inference methods in Bayes nets, such as random and rejection sampling, utilize Monte Carlo algorithms for stochastic sampling to estimate complex probabilities. Random sampling involves sampling in topological order, while rejection sampling generates samples from hard-to-sample distrib
0 views • 9 slides
Formal Verification of Cyberphysical Systems and Future Certification Methods
Explore the formal verification techniques and tools used in cyberphysical systems, including KeYMaera verification tool, applications in distributed car control and adaptive cruise control, and the formal verification of ACC algorithms. The future work section highlights considerations for sensor d
0 views • 17 slides
Comprehensive Solution for EU Digital COVID Certificate Verification
This solution offers face recognition, temperature monitoring, and verification of EU Digital COVID Certificates for personnel. It includes products like DHI-ASI7213X-V1-T1 and ASF172X-T1, with various unlocking modes and support for certificate verification. The system allows for accurate and fast
0 views • 7 slides
Automated Static Verification of Higher-order Functional Programs
Explore the automated static verification of higher-order functional programs, focusing on Haskell code. Learn about denotational semantics, program assertions, and tools like GHC for verification. Discover the emphasis on simplicity and structural properties for easy proofs. Consider utilizing exis
0 views • 22 slides
Gradual Program Verification and its Techniques
Gradual Program Verification introduces a method where static verification is combined with dynamic verification to ensure program correctness gradually. This approach allows for partial specifications and runtime checks to be gradually applied, reducing the risk of errors and overhead in software d
0 views • 18 slides
Understanding Random Numbers in Computers
Explore the concept of true random numbers versus pseudorandom numbers in computers. Learn how pseudorandom numbers are generated algorithmically but predictable, while true random numbers are derived from physical phenomena like radioactive decay. Discover the relevance of high-entropy pseudorandom
0 views • 57 slides
Accelerated Evolutionary Planning for Constrained Robotic Missions: A Dynamic Programming Approach
This research paper by Rahul Kala presented at the IEEE Conference on Simulation, Modelling, and Programming for Autonomous Robots introduces a novel method combining dynamic programming and accelerated evolutionary planning for efficient robotic mission planning. The paper discusses various example
0 views • 19 slides
IEEE 802.11-21/1585r10: Identifiable Random MAC Address Presentation Summary
This presentation discusses the concept of Identifiable Random MAC (IRM) addresses in the IEEE 802.11-21/1585r10 standard. It covers the purpose of IRM addresses in preventing third-party tracking while allowing trusted parties to identify specific devices. The presentation outlines the use of Ident
0 views • 24 slides
Understanding Laplace Transforms for Continuous Random Variables
The Laplace transform is introduced as a generating function for common continuous random variables, complementing the z-transform for discrete ones. By using the Laplace transform, complex evaluations become simplified, making it easy to analyze different types of transforms. The transform of a con
0 views • 17 slides
Adapting Linear Hashing for Flash Memory Constrained Embedded Devices
This research explores the adaptation of linear hashing for improved data handling on flash memory-constrained embedded devices. Motivated by the increasing data collection by IoT devices, the study focuses on implementing database structures like a linear hash table for efficient data processing. T
0 views • 67 slides
Warning Verification and Scoring Guidelines in Weather Forecasting Workshop
Learn about the verification of warnings, classical contingency scoring, false alarm ratio, hits, false alarms, missed alarms balance, threshold-based warning verification, and impact-based warning verification discussed in the IMS Warning workshop at KNMI Block III. Understand the importance of mai
0 views • 13 slides
Verification Modulo Versions: Towards Usable Verification
Explore the challenges and solutions in compile-time verification with CodeContracts in Visual Studio. Delve into addressing warnings, improving analysis precision, and managing syntactic baselines for a more reliable verification process.
0 views • 33 slides
SKA1 Low Assembly Integration & Verification Plan
The SKA1 Low Assembly, Integration, and Verification (AIV) Plan outlines the responsibilities of the AIV Consortium, consortium partners, and the roll-out plan for the SKA1 Low telescope. The plan encompasses user requirements validation, system verification, operational concepts, and more. It detai
0 views • 12 slides
Understanding Discrete Random Variables and Variance Relationships
Explore the concepts of independence in random variables, shifting variances, and facts about variance in the context of discrete random variables. Learn about key relationships such as Var(X + Y) = Var(X) + Var(Y) and discover common patterns in the Discrete Random Variable Zoo. Embrace the goal of
0 views • 27 slides
ICAO Strategic Objective: Economic Development of Air Transport Verification and Validation Overview
This content provides an in-depth analysis of the ICAO Strategic Objective focusing on the economic development of air transport through verification and validation processes for air carriers. It includes details on forms verification, economic analysis, and policy considerations discussed at the IC
0 views • 22 slides
Overview of Program Verification Tools and Techniques
Explore the pillars of program verification, early mechanical verification systems, software quality assurance, and a spectrum of verification tools used for ensuring functional correctness, safety-critical systems, and more. Discover the role of proof assistants and automatic decision procedures in
0 views • 21 slides
Analysis of Time Use Surveys: Insights from France and Sweden
Monitoring time use survey methods and results from a local time policy perspective reveals key trends in France over 25 years, including the evolution of constrained and non-constrained times, daily activities of employed women and men, and comparisons for evaluating welfare state performances. Dat
0 views • 15 slides
GUC-Secure Commitments via Random Oracles: New Findings
Exploring the feasibility of GUC-secure commitments using global random oracles, this research delves into the differences between local and global random oracles, outlining motivations and future work. It discusses UC frameworks, zero-knowledge proofs, oblivious transfers, and the GUC framework for
0 views • 18 slides
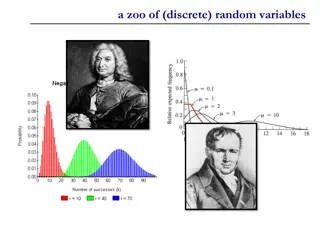
Understanding a Zoo of Discrete Random Variables
Discrete random variables play a crucial role in probability theory and statistics. This content explores three key types: Bernoulli random variable, binomial random variable, and error-correcting codes. From understanding the basics of Bernoulli trials to exploring the application of error correcti
0 views • 27 slides
Introduction to UVM: Verification Methodologies Overview
Explore the Universal Verification Methodology (UVM) for writing modular, scalable, and reusable testbenches. Learn about UVM's key technical highlights, its support for migration towards Coverage Driven Verification (CDV), and the advantages of Constrained Random Verification (CRV) in functional ha
0 views • 20 slides