System Models in Software Engineering: A Comprehensive Overview
System models play a crucial role in software engineering, aiding in understanding system functionality and communicating with customers. They include context models, behavioural models, data models, object models, and more, each offering unique perspectives on the system. Different types of system
3 views • 33 slides
Computability: Exploring Theoretical Limits of Computation
Delve into computability theory, focusing on what is computable and the limits of computation. Explore concepts like Rice's Theorem, the Halting Problem, and classes of expressiveness in computability theory, such as combinational logic, finite-state machines, pushdown automata, and Turing machines.
5 views • 43 slides
Overview of Distributed Systems: Characteristics, Classification, Computation, Communication, and Fault Models
Characterizing Distributed Systems: Multiple autonomous computers with CPUs, memory, storage, and I/O paths, interconnected geographically, shared state, global invariants. Classifying Distributed Systems: Based on synchrony, communication medium, fault models like crash and Byzantine failures. Comp
9 views • 126 slides
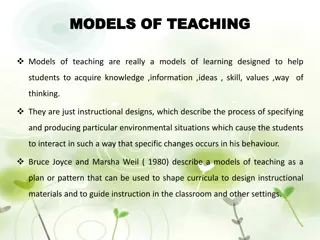
Understanding Models of Teaching for Effective Learning
Models of teaching serve as instructional designs to facilitate students in acquiring knowledge, skills, and values by creating specific learning environments. Bruce Joyce and Marsha Weil classified teaching models into four families: Information Processing Models, Personal Models, Social Interactio
1 views • 28 slides
Computation of Machine Hour Rate: Understanding MHR and Overhead Rates
Computation of Machine Hour Rate (MHR) involves determining the overhead cost of running a machine for one hour. The process includes dividing overheads into fixed and variable categories, calculating fixed overhead hourly rates, computing variable overhead rates, and summing up both for the final M
4 views • 18 slides
Enhanced Security in Multiparty Computation
Explore the improved black-box constructions of composable secure computation, focusing on definitions, objectives, and the formalization basics of multiparty computation (MPC). Learn about the motivating security aspects in MPC and the real/ideal paradigm. Discover how MPC security involves compari
1 views • 68 slides
Significance of Models in Agricultural Geography
Models play a crucial role in various disciplines, including agricultural geography, by offering a simplified and hypothetical representation of complex phenomena. When used correctly, models help in understanding reality and empirical investigations, but misuse can lead to dangerous outcomes. Longm
0 views • 8 slides
Enhancing Information Retrieval with Augmented Generation Models
Augmented generation models, such as REALM and RAG, integrate retrieval and generation tasks to improve information retrieval processes. These models leverage background knowledge and language models to enhance recall and candidate generation. REALM focuses on concatenation and retrieval operations,
1 views • 9 slides
Understanding Numerical Methods and Errors in Computation
Delve into the world of numerical methods through the guidance of Dr. M. Mohamed Surputheen. Explore topics such as solving algebraic and transcendental equations, simultaneous linear algebraic equations, interpolation, numerical integration, and solving ordinary differential equations. Learn about
0 views • 130 slides
Trust Income Computation and Application Guidelines
Learn about income computation of trusts using ITR-5 vs. ITR-7, types of institutions, components of income, application of income, and important guidelines including amendments by FA2022 for charitable and religious trusts.
0 views • 47 slides
Secure Computation Techniques in RAM Models with Efficient Automation
Explore the automation of efficient RAM-model secure computation techniques, including examples such as secure binary search. Discover how traditional solutions using circuit abstractions can be improved for sub-linear time computation through methods like Oblivious RAM. Learn about techniques such
0 views • 37 slides
Secure Multiparty Computation for Department of Education Data Sharing
This report discusses the use of Secure Multiparty Computation (SMC) to enable sharing of sensitive Department of Education data across organizational boundaries. The application of SMC allows for joint computation while keeping individual data encrypted, ensuring privacy and security within the Nat
0 views • 15 slides
Advancements in Active Secure Multiparty Computation (MPC)
Delve into the realm of secure multiparty computation under 1-bit leakage, exploring the intersection of DP algorithms, MPC, and the utilization of leakage for enhanced performance. Discover the overhead implications of achieving active security, as well as the evolution of secure computation protoc
0 views • 43 slides
Understanding Energy Distribution System Line Models
This presentation delves into the various line models used in energy distribution systems, including exact line segment models and their derivation from Kirchhoff's voltage and current laws. The discussion covers three line segment models, the computation of phase impedance and admittance matrices,
0 views • 44 slides
COMET: Code Offload by Migrating Execution - OSDI'12 Summary
The research paper discusses COMET, a system for transparently offloading computation from mobile devices to network resources to improve performance. It outlines the goals of COMET, its design, and evaluation, focusing on distributed shared memory and bridging computation disparity through offloadi
0 views • 31 slides
Exploring Challenges and Opportunities in Processing-in-Memory Architecture
PIM technology aims to enhance performance by moving computation closer to memory, improving bandwidth, latency, and energy efficiency. Despite initial setbacks, new strategies focus on cost-effectiveness, programming models, and overcoming implementation challenges. A new direction proposes intuiti
0 views • 43 slides
Actively Secure Arithmetic Computation and VOLE Study
Exploring actively secure arithmetic computation and VOLE with constant computational overhead at Tel Aviv University. Understanding how functions are represented in secure computation using arithmetic circuits over boolean circuits. Efficiently evaluating arithmetic circuits over large finite field
0 views • 36 slides
Enhancing Multi-Party Computation Efficiency Through ORAM Techniques
Explore the realm of efficient random access in multi-party computation through the reevaluation of classic schemes and the introduction of new approaches. Discover the potential of ORAM in improving performance and reducing costs in various computational tasks, such as secure multi-party computatio
0 views • 22 slides
Understanding Information Retrieval Models and Processes
Delve into the world of information retrieval models with a focus on traditional approaches, main processes like indexing and retrieval, cases of one-term and multi-term queries, and the evolution of IR models from boolean to probabilistic and vector space models. Explore the concept of IR models, r
0 views • 65 slides
Exploring Garbled RAM and Secure Computation
Garbled RAM, a concept based on garbled circuits, allows for secure two-party computation with implications for communication and computational complexities. The progression from basic to more ambitious scenarios in Garbled RAM models and the landscape of utilizing OWFs in a black-box manner for imp
0 views • 26 slides
Exploring Secure Computation in the Age of Information
Welcome to Secure Computation Lecture 1 by Arpita Patra. The course covers evaluation policies, projects, and references in the realm of secure computation. The content delves into the significance of information security across various sectors, emphasizing the importance of safeguarding sensitive d
0 views • 36 slides
Understanding Cross-Classified Models in Multilevel Modelling
Cross-classified models in multilevel modelling involve non-hierarchical data structures where entities are classified within multiple categories. These models extend traditional nested multilevel models by accounting for complex relationships among data levels. Professor William Browne from the Uni
0 views • 13 slides
Secure Two-Party Computation and Basic Secret-Sharing Concepts
In today's lecture of "Foundations of Cryptography," the focus is on secure two-party and multi-party computation, emphasizing semi-honest security where Alice and Bob must compute without revealing more than necessary. Concepts such as real-world vs. ideal-world scenarios, the existence of PPT simu
0 views • 27 slides
Linear Communication in Secure Multiparty Computation for Efficient and Fast Processing
The research focuses on achieving perfectly secure multiparty computation (MPC) with linear communication and constant expected time. It explores efficient approaches using a broadcast-hybrid model and P2P communication, aiming to balance speed and efficiency in MPC. The study highlights the importa
0 views • 23 slides
Secure Computation Challenges and Solutions in Data Mining
Exploring the intersection of secure computation and data mining, this content uncovers key challenges such as improving algorithms, converting programs for secure computation, and addressing parallelizability issues. It highlights the importance of cryptography in ensuring data privacy and presents
0 views • 30 slides
Covert Computation: Ensuring Undetectable Engagement
Covert computation aims to conceal the fact that computation is occurring and hide engagement in certain tasks like secure computation, authenticated key exchange, and more. By making messages indistinguishable and utilizing steganographic channels, it becomes possible to keep the activities covert
0 views • 16 slides
Overview of Turing Machines: Introduction, Tape, and Computation
Turing Machines are fundamental in the theory of computation, capable of recognizing all computable languages. They consist of a Finite State Machine combined with an infinite tape. The tape is initialized with input on the left end, and a TM's computation can either halt by entering special accept
0 views • 29 slides
Computation for Real Estate Sector in Bangalore Branch of ICAI
Practical overview of GST computation for real estate transactions in Bangalore, with details on old rates with ITC and new rate regime effective from April 1, 2019. The content discusses different transactions, conditions for new rates without ITC, and provides insights on the 80:20 computation met
0 views • 39 slides
Fides: A System for Verifiable Computation Using Smart Contracts
Fides presents a system for verifiable computation using smart contracts, focusing on blockchain basics, Ethereum, smart contracts, and outsourcing computation. It explores key components of blockchain, Ethereum's decentralized computing platform, properties of smart contracts, and the concept of ve
0 views • 25 slides
Insights into Secure Computation with Minimal Interaction
This paper revisits the concept of secure computation with minimal interaction, focusing on the challenges and possibilities of achieving secure multiparty computation in 2 rounds. Specifically exploring scenarios with 3 and 4 parties, the study delves into the reasons for choosing n=3, n=4, and t=1
0 views • 23 slides
Overview of Income Computation and Disclosure Standards (ICDS)
The Income-tax Act, 1961 introduced Income Computation and Disclosure Standards (ICDS) to be followed by certain assesses for computation of income. ICDS applies to taxpayers using the mercantile system of accounting from the Assessment Year 2016-17 onwards. Non-compliance with ICDS can lead to Best
0 views • 49 slides
Understanding Composite Models in Building Complex Systems
Composite models are essential in representing complex entities by combining different types of models, such as resource allocation, transport, and assembly models. Gluing these models together allows for a comprehensive representation of systems like the milk industry, where raw materials are trans
0 views • 27 slides
Blackbox Verifiable Computation Scheme Overview
This summarized content discusses the concept of blackbox verifiable computation, focusing on the challenges faced by clients and servers, the role of helper oracles, positive results utilizing homomorphic encryption, and background information on Random Self Reducible (RSR) functions. The protocol
0 views • 20 slides
Parallel Computation for Matrix Multiplication
Matrix multiplication is a fundamental operation with diverse applications across scientific research. Parallel computation for matrix multiplication involves distributing the computational workload over multiple processors, improving efficiency. Different algorithms have been developed for multiply
0 views • 36 slides
Communication Steps for Parallel Query Processing: Insights from MPC Model
Revealing the intricacies of parallel query processing on big data, this content explores various computation models such as MapReduce, MUD, and MRC. It delves into the MPC model in detail, showcasing the tradeoffs between space exponent and computation rounds. The study uncovers lower bounds on spa
0 views • 25 slides
Theory of Computation Introduction: Dr. Abdulhussein M. Abdullah
Delve into the theory of computation with Dr. Abdulhussein M. Abdullah in the 2nd semester of 2017-2018. Explore the fundamental questions regarding what can be computed, computational problems, and the representation of information. Gain insights into computational models and computability, complex
0 views • 27 slides
Secure Computation Laboratory: Modeling Attacks on PUF Systems
Explore the research on physically unclonable function (PUF) modeling attacks using Logistic Regression and CMA-ES algorithms. Learn to simulate and analyze reliable and noisy PUF instances, implement attacks, and assess modeling accuracy. The laboratory goals include simulating APUF and XOR PUF sys
0 views • 10 slides
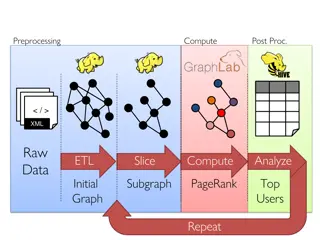
Data Processing and Analysis for Graph-Based Algorithms
This content delves into the preprocessing, computing, post-processing, and analysis of raw XML data for graph-based algorithms. It covers topics such as data ETL, graph analytics, PageRank computation, and identifying top users. Various tools and frameworks like GraphX, Spark, Giraph, and GraphLab
0 views • 8 slides
Understanding Branching Programs and Decision Trees in Computation
Branching Programs and Decision Trees serve as simple models for computation, exploring space and time complexity trade-offs. The dual terminology, encompassing Switching Networks to Binary Decision Diagrams, reveals the evolution of these models in complexity theory and formal verification.
0 views • 31 slides
Advanced Techniques in Multi-Party Computation
Explore cutting-edge methods in Multi-Party Computation (MPC), including leveraging Fully Homomorphic Encryption (FHE) for minimal round complexity, constructing MPC directly via FHE techniques, and simplifying multi-key FHE constructions for efficient decryption. Learn about key concepts such as di
0 views • 17 slides