Enhance Your Fitness Journey: Core Strength and Speed Workouts
Explore the importance of core strength in maintaining posture and physical performance, engage in a virtual group challenge to test your endurance with wall planks, and boost your core strength with a practical 7-minute workout. Transition into focusing on speed with insights into sprinting, cyclin
0 views • 38 slides
Understanding Pharmaceutical Calculations: Altering Product Strength and Solutions
Pharmaceutical calculations involve altering the strength of pharmaceutical preparations by adjusting the proportion of active ingredients, using stock solutions, and problem-solving techniques. This process includes dilution, fortification, and concentration changes to achieve desired product stren
7 views • 23 slides
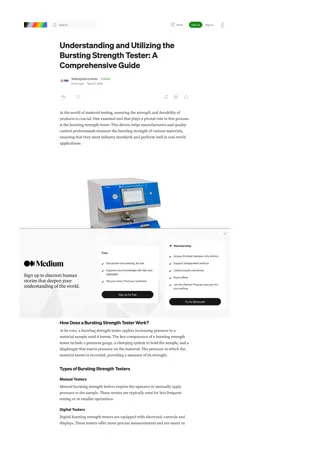
Understanding and Utilizing the Bursting Strength Tester: A Comprehensive Guide
In the world of material testing, ensuring the strength and durability of products is crucial. One essential tool that plays a pivotal role in this process is the bursting strength tester. This device helps manufacturers and quality control professionals measure the bursting strength of various mate
6 views • 5 slides
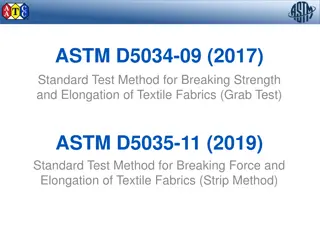
Testing Methods for Textile Fabrics Breaking Strength and Elongation
Standard testing methods, ASTM D5034 and D5035, are used to determine the breaking strength and elongation of textile fabrics through grab and strip tests. The grab test measures the effective strength of fabric using adjacent yarns, while the strip test compares the strength of unwoven yarns. Appar
0 views • 29 slides
Pharmacy Practice: Percentage and Ratio Strength Calculations
Understanding percentage and ratio strength calculations is crucial in pharmacy practice. Percentages can be expressed as fractions or decimals, and various concentrations like weight-in-volume and volume-in-volume are used in pharmaceutical preparations. Learn how to calculate the correct strength
0 views • 24 slides
Understanding AES Encryption in Computer Engineering
Advanced Encryption Standard (AES) is a powerful symmetric block cipher used in computer engineering for data encryption. Developed by NIST, AES supports key lengths of 128, 192, and 256 bits. The algorithm operates on a state array and consists of encryption phases like initial round, main rounds,
2 views • 8 slides
Columnar Transposition Cipher: Data Encryption Techniques at Mustansiriyah University Engineering College
Transposition ciphers, particularly the columnar transposition technique, are explored in the course "Data Encryption" at Mustansiriyah University Engineering College. The cipher involves rearranging message elements without changing their identities, making it crucial in modern block cipher designs
0 views • 4 slides
Understanding Strength-Duration (SD) Curve: A Neuromuscular Diagnostic Test
Strength-Duration (SD) curve is a diagnostic test assessing neuromuscular integrity by measuring the relationship between stimulus strength and duration. It helps in electro-diagnosis of peripheral nervous system disorders and evaluates nerve degeneration and regeneration. The curve is obtained by p
1 views • 17 slides
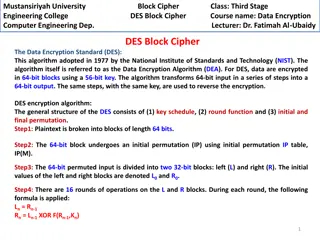
Understanding DES Block Cipher in Computer Engineering at Mustansiriyah University
Data Encryption Standard (DES) is a widely used algorithm for encrypting data in 64-bit blocks with a 56-bit key. This course at Mustansiriyah University covers the key components of DES, including the key schedule, round function, and initial/final permutation. Students learn about the encryption p
1 views • 8 slides
ASTM D3786/D3786M-18 Standard Test Method for Bursting Strength of Textile Fabrics
This standard test method, ASTM D3786/D3786M-18, specifies the procedure for determining the bursting strength of textile fabrics using a diaphragm bursting strength tester. The test involves clamping the specimen over an expandable diaphragm and applying pressure until the fabric ruptures. The burs
0 views • 16 slides
Evolution of Cryptography: From Ancient Techniques to Modern Security Mechanisms
Explore the evolution of cryptography from ancient techniques like the Caesar Cipher to modern security mechanisms like SSL, SSH, and IPSec. Learn how cryptography plays a crucial role in ensuring confidentiality, integrity, authentication, non-repudiation, and availability in network security. Disc
1 views • 62 slides
Understanding Pharmaceutical Product Strength Alteration
Exploring methods to adjust the strength of pharmaceutical preparations by manipulating the proportion of active ingredients, dilution, concentration, and the relationship between strength and total quantity. Learn about solving problems related to altering product strength using inverse proportion,
0 views • 17 slides
ADFGVX Cipher: Encryption and Decryption Techniques
Discover the ADFGVX cipher, a historical encryption method used to secure messages during World War I. Learn about Fritz Nebel and Gino Painvin, who played significant roles in its development. Explore the Polybius Square invented by Polybius in the 2nd century BC for converting letters to numbers.
0 views • 14 slides
Understanding Pharmaceutical Preparations: Strength and Concentration
Pharmaceutical preparations can have their strength and concentration adjusted by changing the proportion of active ingredients. This process involves increasing or decreasing the active ingredient, adding diluents, admixing with other preparations, or evaporating the vehicle. Dilution of liquid, so
0 views • 34 slides
Transposition Cipher Techniques in Modern Block Ciphers
Transposition ciphers, specifically columnar and double columnar transpositions, are explored in the context of data encryption and computer engineering at Mustansiriyah University Engineering College. These techniques involve rearranging message elements without changing their identities, providing
0 views • 4 slides
Spiritual Warfare and Divine Strength in the Book of Daniel
Delve into the spiritual battles depicted in the book of Daniel, where unseen forces clash, and divine strength empowers the faithful to stand strong. Explore the glorious visions, the reality of spiritual warfare, and the strength available for the overwhelmed in a world where we wrestle not with f
0 views • 6 slides
Importance of Non-Destructive Testing in Concrete Structures
Non-destructive testing (NDT) of concrete plays a crucial role in assessing the strength, durability, and quality control of structures. This method involves assessing properties such as density, strength, crack depth, and reinforcement location without damaging the concrete. NDT is essential for ve
0 views • 5 slides
Best Strength Gym in Elanora
Are you looking for the Best Strength Gym in Elanora? Then contact Nexus Performance Gym. Your space to find strength, join a community, and get educated!! Located on the southern end of the Gold Coast. Whether you're an elite athlete or new to stren
0 views • 6 slides
Optimizing MIH SA Establishment for Single Radio Handover
This presentation discusses the optimization of MIH (Media Independent Handover) Security Association (SA) establishment for single radio handover. It covers the key points and methods proposed for enhancing the communication between Mobile Node (MN) and Top Point of Service (TPoS) using cipher suit
3 views • 6 slides
Understanding Small-State Noncryptographic Pseudorandom Number Generators
Explore the design and testing of small-state noncryptographic pseudorandom number generators, including definitions, rules of thumb, chisquare tests, existing and new generators, and more. Learn about block cipher encryption, hash functions, pseudorandom number generation, reversible mixing, and re
0 views • 46 slides
Understanding Block Ciphers in Cryptography
Explore the principles of block ciphers in modern cryptography, focusing on the Data Encryption Standard (DES) and its design principles. Learn about block cipher encryption, Feistel block cipher structure, n-bit block ciphers, ideal block ciphers, key length considerations, and challenges with idea
0 views • 44 slides
The Power of Courage in Faith: Strength Through God's Presence
Drawing strength from faith in God, courage empowers us to face challenges with perseverance and bravery. With a reminder from Joshua 1:9, we are encouraged to be strong and courageous, knowing that God is always with us. This definition of courage, both from Webster's and the Bible, highlights the
3 views • 4 slides
Understanding Encryption Techniques: From Transposition Ciphers to Rail Fence Ciphers
Explore the world of encryption techniques, diving into transposition ciphers and rail fence ciphers. Learn about encryption, decryption, plaintext, ciphertext, keys, and the art of secret writing. Discover how transposition ciphers reorder letters without changing their values and how rail fence ci
0 views • 26 slides
Contribution of Quadriceps, Hamstrings, and Latissimus Dorsi Muscle Strength to Rowing Performance in West Java
Rowing is a demanding sport that requires strong leg muscle strength for optimal performance, particularly in West Java where rowing athletes train. This study aims to investigate the contribution of quadriceps, hamstrings, and latissimus dorsi muscle strength to the performance of rowing athletes i
0 views • 16 slides
Personalized Fitness Plan: Achieve Your Goals with Structured Workouts and Fun Activities
Design your own fitness plan incorporating 60 minutes of daily physical activity and exercises to improve strength, endurance, and flexibility. Create a balanced schedule with structured workouts including strength training, endurance exercises, and flexibility routines. Fill your plan with everyday
0 views • 10 slides
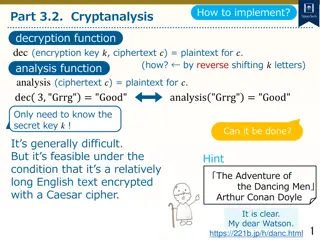
Cryptanalysis and Decryption Techniques for Caesar Cipher
Learn how to decrypt Caesar cipher text using cryptanalysis techniques by analyzing letter frequencies and determining the secret key through character analysis. Explore methods to count character frequencies and find the most common letter to decipher encrypted messages.
0 views • 11 slides
Total Body Push Pull Rotate Training for Strength and Endurance
Total Body Push Pull Rotate Training helps improve muscular endurance and strength by alternating exercises from different strength training categories. The workout consists of choosing exercises from push/pull categories and incorporating rotational movements for a comprehensive full-body workout.
0 views • 5 slides
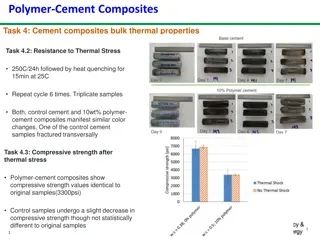
Study on the Thermal and Chemical Properties of Polymer-Cement Composites
The study investigates the resistance of polymer-cement composites to thermal stress and chemical attacks such as acidic and high CO2 environments. Results show similar color changes in control cement and polymer-cement composites after thermal stress, with the latter maintaining compressive strengt
0 views • 5 slides
When I Am Weak, Then I Am Strong: Understanding Strength in Weakness
In 2 Corinthians 12:6-10, the apostle Paul reflects on how a thorn in the flesh humbled him, leading to a greater understanding of God's grace and strength in weakness. This passage emphasizes that true strength is found in acknowledging our dependence on Christ, allowing His power to be perfected i
0 views • 7 slides
Understanding Ratio Strength and Milligrams Percent in Pharmacy Practice
In the field of pharmacy practice, understanding ratio strength and milligrams percent is essential for preparing solutions accurately. Ratio strength involves expressing concentrations in parts per hundred, while milligrams percent denotes the amount of substance in 100 mL of liquid. This article e
0 views • 10 slides
Understanding Plain & Reinforced Concrete Structures in Design Engineering
In the design of Plain & Reinforced Concrete structures, various strength design methods such as Ultimate Strength Design (USD) and Allowable Strength Design (ASD) are utilized. These methods involve factors of safety, material strength, load factors, and analysis in the elastic range. Additionally,
0 views • 11 slides
Factors Affecting Acid Strength: Atoms, Size, Hybridization, and Electronegativity
The strength of acids is influenced by various factors such as the atom on which the negative charge of the acid's conjugate base rests, atom size, hybridization, and electronegativity. The stability of negative charges on atoms, atom size allowing charge delocalization, preferred orbital types for
0 views • 23 slides
GripTrack: Innovative Device for Monitoring Elderly Health
GripTrack is a portable grip strength monitoring device designed to track cardiovascular and musculoskeletal health in the elderly population. It aims to provide an accurate early warning system by assessing grip strength, which can indicate cognitive decline, cardiovascular health, and frailty synd
0 views • 14 slides
Understanding Specification Strength and Substitutability
Specifications in software development play a crucial role in determining the strength of requirements and the ability to substitute implementations. This content discusses how stronger specifications imply weaker ones, the importance of satisfaction in specifications, and the application of the Lis
0 views • 42 slides
Understanding Mechanical Properties of Nanostructured Materials
Nanostructured materials exhibit unique mechanical properties due to factors like grain boundary structure and dislocation movement. Reduction in grain size can enhance strength and hardness while reducing ductility. Nanomaterials may reach theoretical strength levels, significantly higher than sing
0 views • 23 slides
Types of Conductors in Transmission Lines
Aluminum conductors, such as AAC, AAAC, ACSR, and ACAR, are commonly used in transmission lines due to their high conductivity, tensile strength, light weight, and resistance to corrosion. AAC is known for its good conductivity but limited strength, while AAAC offers better mechanical strength and c
0 views • 17 slides
Fun Spy Challenges for Beavers - Crack the Codes!
Dive into exciting spy missions with a group of clever beavers! Decode secret messages using various encryption techniques such as switching codes, letter grouping, Pig Pen cipher, Morse code, and Caesar cipher. Test your spy skills as you unravel each challenge to reveal hidden messages. Unleash yo
0 views • 6 slides
Fundamentals of Cryptography and Network Security
Explore the basics of cryptography, including classical encryption techniques, terminology definitions, types of encryption operations, cryptanalysis objectives and attacks, and the concept of cipher strength. Uncover the principles and methods behind encryption and decryption, key distinctions betw
0 views • 52 slides
Unlock the Challenges in Cipher Cove: A STEM Adventure
Explore Cipher Cove and tackle five cryptographic challenges involving different ciphers such as Caesar Shift, Pigpen, Transposition, Substitution, and Periodic Table. Put your problem-solving skills to the test by deciphering hidden clues and codes to progress through each challenge and ultimately
0 views • 6 slides
Understanding Shear Strength in Engineering Materials
Shear strength is a crucial mechanical property that defines a material's ability to resist forces causing internal structure to slide. This property plays a significant role in various engineering fields, impacting design, construction, and material selection. Shear strength is essential in prevent
0 views • 31 slides