Low Pay Household Estimates in Rural India
Analysis of data from the Periodic Labour Force Survey reveals estimates of households with monthly per capita earnings below a threshold in Rural India. The study, presented by Vasavi Bhatt, focuses on the characteristics of low earnings households and highlights the importance of decent work and i
1 views • 8 slides
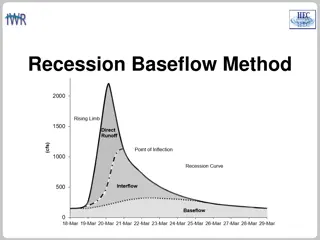
Understanding the Recession Baseflow Method in Hydrology
Recession Baseflow Method is a technique used in hydrology to model hydrographs' recession curve. This method involves parameters like Initial Discharge, Recession Constant, and Threshold for baseflow. By analyzing different recession constants and threshold types such as Ratio to Peak, one can effe
0 views • 8 slides
Clear Channel Assessment (CCA) Behavior of Commercial Wi-Fi Equipment
This document, dated July 2022, delves into the Clear Channel Assessment (CCA) behavior of commercial Wi-Fi equipment in response to Narrowband Frequency Hopping (NB FH) signals. It explores the regulatory framework around license-exempt frequency bands in the USA and Europe, highlighting the specif
0 views • 22 slides
Understanding Complex Computing Problem (CCP) and Complex Computing Activity (CCA)
Dr. Saman Hina, along with Dr. Farrukh Arif and Dr. Maria Waqas, presents information on Complex Computing Problem (CCP) - a problem involving technical, computing, and other issues with no obvious solution, requiring deep knowledge and analytical thinking. CCP is evaluated through predefined rubric
4 views • 19 slides
Solve Questions to Grab the Linux Foundation CCA Certification
Click Here--- \/\/bit.ly\/4ddu2cK ---Get complete detail on CCA exam guide to crack Cilium Associate. You can collect all information on CCA tutorial, practice test, books, study material, exam questions, and syllabus. Firm your knowledge on Cilium A
0 views • 9 slides
Study Guide for Linux Foundation CCA Certification Exam
Click Here--- \/\/bit.ly\/4ddu2cK ---Get complete detail on CCA exam guide to crack Cilium Associate. You can collect all information on CCA tutorial, practice test, books, study material, exam questions, and syllabus. Firm your knowledge on Cilium A
0 views • 8 slides
Understanding Central Place Theory: Key Concepts and Determinants
Central Place Theory (CPT) attempts to explain the spatial arrangement, size, and number of settlements based on central places, zones of influence, and hinterlands. This theory, introduced by Walter Christaller in 1933, outlines the importance of central functions, threshold populations, and factor
0 views • 12 slides
Implications of Large-size RU Aggregation on RTS/CTS in IEEE 802.11-17
Addressing implications of large-size RU aggregation on RTS/CTS in IEEE 802.11-17, focusing on the signaling of Enhanced High Throughput Format PPDU Bandwidth and puncturing in RTS/CTS frames. Proposing the use of HE MU-RTS Trigger frame to elicit CTS response from STAs, along with different CTS for
4 views • 17 slides
Understanding ROC Curves and Operating Points in Model Evaluation
In this informative content, Geoff Hulten discusses the significance of ROC curves and operating points in model evaluation. It emphasizes the importance of choosing the right model based on the costs of mistakes like in disease screening and spam filtering. The content explains how logistical regre
7 views • 11 slides
Understanding Human Contrast Threshold and Astronomical Visibility
Delve into the practical implications of human contrast threshold and astronomical visibility to explore the faintest stars visible to the naked eye or through telescopes under various lighting conditions. This study aids in comprehending the essence of dark skies, the historical evolution of light
0 views • 28 slides
Exploring English Threshold Concepts in Year 6: Building Blocks for Spiritual Learning
Delve into the comprehensive English threshold concepts for Year 6 students focusing on writing, reading, and speaking skills. Explore the magic of poetry and Greek myths as tools for spiritual growth and understanding. Develop a deeper connection with language through structured learning objectives
0 views • 13 slides
Security with Functional Re-Encryption in Cryptography
Exploring the concept of functional re-encryption from the perspective of security in encryption schemes lies between CPA and CCA security levels. The work done by Yevgeniy Dodis, Shai Halevi, and Daniel Wichs delves into how functional re-encryption can enhance the security and privacy of encrypted
0 views • 12 slides
Evolution of Proofs in Cryptography
Cryptography has evolved from classical proofs to interactive and probabilistically checkable proofs, enabling the development of applications like Non-Malleable and Chosen-Ciphertext Secure Encryption Schemes. Non-Malleability protects against active attacks like malleability and chosen-ciphertext
0 views • 29 slides
Hardness of Proving CCA-Security in Signed ElGamal
Bogdan Warinschi from the University of Bristol, along with David Bernhard and Marc Fischlin, discusses the challenges in proving the chosen-ciphertext security of signed ElGamal encryption schemes. The potential solution involves adding a proof of knowledge to ciphertexts to prevent adversaries fro
0 views • 26 slides
Understanding Low Threshold Rank Graphs and Their Structural Properties
Explore the intriguing world of low threshold rank graphs and their structural properties, including spectral graph theory, Cheeger's inequality, and generalizations to higher eigenvalues. Learn about the concept of threshold rank, partitioning of graphs, diameter limits, and eigenvectors approximat
0 views • 22 slides
Insights into Two-Share Threshold Implementation in Lightweight Cryptography
Tailored for constrained applications, two-share threshold implementation offers efficient and secure solutions, analyzed against side-channel attacks. Exploring the motivation, background, results, and comparison with three-share schemes, this study provides valuable insights into the viability of
0 views • 32 slides
Citizen Complaint Authority (CCA) Overview in City of Cincinnati Neighborhoods
Citizen Complaint Authority (CCA) in City of Cincinnati focuses on investigating serious police interventions, resolving citizen complaints fairly, and improving police services. With a clear mission statement, organizational structure, and detailed investigation process, CCA aims to address citizen
0 views • 32 slides
Understanding Cultural Consensus Analysis in Psychological Anthropology
Explore the essence of Cultural Consensus Analysis (CCA) as a significant aspect of psychological anthropology. Through ethnographic work and structured techniques, CCA helps verify shared knowledge within cultural domains and enhance the comprehension of cultural models. The model and steps involve
0 views • 64 slides
Understanding BQ76952 Overcurrent Detection and Analog Data Reset
The BQ76952 device features a protective mechanism where reaching the OCD1 threshold triggers a reset of OTPB and analog data. This was observed during an OCD test, where cell voltages exceeded specified thresholds. While it's not explicitly stated in the specs, exceeding the voltage threshold may b
0 views • 16 slides
Strengthening the CCA Program Through Targeted Marketing Strategies
Utilizing well-designed email campaigns and personalized marketing materials, the CCA Program aims to re-engage lapsed CCAs and attract new candidates. By showcasing testimonials and collaborating with local boards, the program seeks to enhance its reach, credibility, and impact globally.
0 views • 11 slides
Symposium on Positron Emission Tomography and Boron Neutron Capture Therapy Time-Over-Threshold Calibration in J-PET
The 3rd Symposium on Positron Emission Tomography and 1st Symposium on Boron Neutron Capture Therapy focused on Time-Over-Threshold calibration within the framework of J-PET. The event outlined experimental details, event selection, results, and key features of the Jagiellonian Positron Emission Tom
0 views • 35 slides
Enhancing Power Save Mechanisms in IEEE 802.11 for Non-AP STAs
The document discusses improving power save mechanisms for non-AP STAs in IEEE 802.11 by focusing on reducing power consumption during listen mode, enhancing flexibility in transitions between power states, and proposing solutions to enable reception on smaller bandwidths. It emphasizes the importan
0 views • 11 slides
Proposing Dynamic CCA Control for Performance Optimization in WLAN
This presentation discusses the variability in dynamic CCA performance in WLANs and proposes a protocol control mechanism to maximize benefits and minimize drawbacks. It emphasizes the need for an effective control to navigate differing configurations and achieve system throughput improvements witho
0 views • 21 slides
Further Discussion on Non-primary Channel Access in IEEE 802.11
This contribution delves into the utilization of non-primary channels for access in IEEE 802.11 networks, focusing on enhancing frequency reuse, adhering to ETSI standards, evaluating CCA capability types, and analyzing non-ideal deployment scenarios. It discusses the complexity and benefits of non-
0 views • 26 slides
Role of Anomalous Triangle Singularity in Threshold Phenomena Understanding
Anomalous Triangle Singularity (ATS) is explored in the context of threshold phenomena understanding, focusing on its occurrence when all three internal particles are simultaneously on shell. The study delves into kinematic effects, genuine states recognition, and specific cases such as heavy pentaq
0 views • 36 slides
Exploring Idiot Schoolmasters and Threshold Concepts in EAP Education
Explore the concept of "Idiot Schoolmasters" and "Threshold Concepts" in the realm of English for Academic Purposes (EAP) education. Delve into the idea that everyone has the potential to teach and learn from one another, challenging traditional views of knowledge transmission. Discover how threshol
0 views • 14 slides
Financial Reporting Updates - Capitalization Threshold Policy Changes
The financial reporting updates highlight changes to the capitalization threshold policy effective 07/01/2024. The new threshold for purchases for the UR will increase from $1,000 to $5,000 per unit cost. Active fabrications under the current threshold will be grandfathered, while new fabrications r
0 views • 6 slides
CCA 2020 Annual Report Analysis - Key Findings and Trends
The CCA 2020 Annual Report highlights key findings and trends related to citizen complaints, allegations, and demographics. It presents data on complaint trends, allegation types, complaint resolutions, and complainant demographics over a five-year period. The report offers insights into the perform
0 views • 19 slides
Citizen Complaint Authority (CCA) Overview and Mission Statement
The Citizen Complaint Authority (CCA) is committed to investigating serious interventions by police officers and resolving citizen complaints in a fair and efficient manner. Their ultimate goals include addressing citizen concerns and improving perceptions of police service in Cincinnati. The organi
0 views • 31 slides
Understanding UCC2813-X VCC Abs. Max Rating and UVLO
In the UCC2813-X datasheet, the VCC pin has an absolute maximum rating of 12V with a UVLO turn-on threshold of 12.5V for UCC2813-2 and UCC2813-4. The UVLO turn-on threshold can be higher than the maximum rating to protect the Zener diode. To power up the UCC2813-2/4 safely, the external voltage sour
0 views • 5 slides
Proposed Changes to CCA Schemes in IEEE 802.11 Standards
The submission discusses proposals to enhance the Clear Channel Assessment (CCA) schemes for IEEE 802.11 standards, particularly focusing on Clauses 16, 17, and 19. It addresses the current limitations in CCA schemes for different devices and suggests modifications to ensure compliance and efficient
0 views • 13 slides
Determining Minimum Salt Concentration for Human Taste Perception
Freshwater is generally believed to have no taste of salt. This experiment aims to find the minimum concentration of sodium chloride in a water solution that can be detected by humans. Using a double-blind tasting method, the study explores the saltiness threshold and its significance for living org
0 views • 13 slides
Climate Change Adaptation Technical Working Group Session Summary
The Climate Change Adaptation (CCA) Technical Working Group session, led by Mr. Noel Antonio Gaerlan, provided updates on focal points, partners, status of the 2019 workplan, decisions endorsed by SOM, proposed workplan for 2020, and recommendations for SOM consideration. Key activities included wor
0 views • 9 slides
Historical Foundations of the Linear Non-Threshold Dose Response Model
The journey of the Linear Non-Threshold (LNT) dose response model for cancer risk assessment unfolds through the work of scientists like Muller, Timofeeff-Ressovsky, Zimmer, and Delbruck. Muller's initial gene mutation research led to the acceptance of LNT, which was further integrated with the sing
0 views • 45 slides
Urgent Action Needed to Address Non-Threshold Contaminates in Rhode Island
Rhode Island was once leading in protecting its citizens by creating a category for Extremely Hazardous Wastes, including chemotherapy drugs. However, a new issue has emerged with Non-threshold Contaminates, posing a grave risk as any amount is harmful. These dangerous substances are currently being
0 views • 8 slides
Understanding Legacy CCA and OBSS-PD Rules in IEEE 802.11-17 Standard
The document discusses the Legacy Clear Channel Assessment (CCA) rule and OBSS Packet Detection (PD) rule in the IEEE 802.11-17 standard. It highlights the shortcomings of the existing CCA mechanism and proposes exceptions for response frames to prevent interference issues in wireless communications
0 views • 16 slides
Threshold for Platelets Study: Prospective Trial on Platelet Transfusion
This study aims to determine the platelet count threshold for critically ill patients prior to invasive procedures. The trial update includes information on open sites, current recruitment status, and eligibility criteria. The agenda for the meeting covers trial updates, eligibility queries, screeni
0 views • 20 slides
New Assumptions for Achieving Chosen Ciphertext Security in Cryptography
This research work focuses on presenting new assumptions for achieving chosen ciphertext security in public key encryption. The study aims to clarify the necessary and sufficient assumptions to realize general cryptographic primitives, particularly focusing on CCA secure PKE and KEM. The ultimate go
0 views • 27 slides
Understanding TEN Testing in Cochlear Implant Candidacy
Discover the significance of Threshold Equalizing Noise (TEN) testing in evaluating cochlear implant candidacy for patients with potential dead regions in the auditory system. Learn about dead regions, absolute threshold levels, diagnosis using TEN test, interpretation of results, and step-by-step g
0 views • 17 slides
IEEE 802.11-15/1104r4: Optimizing CCA Threshold for Spatial Reuse in WLANs
The document discusses considerations for optimizing the Clear Channel Assessment (CCA) threshold in wireless local area networks (WLANs) to enhance spatial reuse efficiency. It emphasizes minimizing over-protection caused by the current CCA rule while addressing factors like frequency reuse, BSS/OB
0 views • 18 slides