Workshop Report on Implementation of UN Regulations R155 & R156
The report presents key discussions from the 16th workshop on UN Regulations R155 & R156, covering topics such as GNSS spoofing, reporting provisions, software updates, and recertification processes for CSMS/SUMS. It highlights the need for risk assessment, annual reporting, software obligations, an
0 views • 11 slides
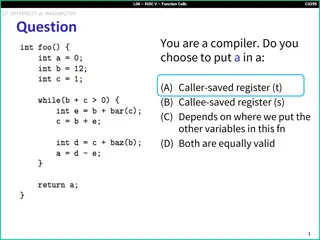
Understanding RISC-V Function Calls
In RISC-V function calls, the decision to place variables in caller-saved or callee-saved registers depends on various factors such as recursion and variable usage within the function. Additionally, understanding how function arguments are passed and stored is crucial for efficient program execution
0 views • 5 slides
Types of Suspicious Messages by Cyber Sprinters and Urgent Call for Assistance
Cyber Sprinters are warning about three types of suspicious messages: Evil Emailers using phishing tactics, Malicious Messenger engaging in smishing, and Phoney Phone Caller utilizing vishing. The South West Constabulary urgently seeks the Cyber Crime Response Unit's help to investigate a group of c
1 views • 7 slides
Mastering Telephone Skills in Healthcare
Develop your telephone skills in healthcare by following guidelines for answering calls, identifying purposes, handling various types of calls, addressing clinical issues, and implementing effective telephone tips. Proper documentation of calls is essential for legal protection and may be a part of
1 views • 12 slides
Enhancing Secure Telephone Identity and Caller Authentication
The STIR Working Group aims to address the issues surrounding the reliability of caller identities in telecommunication networks. By specifying internet-based mechanisms for verifying the authorization of calling parties, STIR seeks to combat threats like caller ID spoofing and unauthorized use of t
0 views • 11 slides
Understanding x86-64 Procedures and Data Structures
This content provides insights into x86-64 programming, covering topics such as procedures, integer registers, stack frames, locals in the red zone, interesting features of stack frames, arrays, multi-dimensional structures, and more. It dives into the usage conventions of integer registers, the all
0 views • 44 slides
Understanding Procedures and Functions in Programming
Explore the fundamentals of procedures and functions in programming, including the control flow changes, function calls, and stack operations. Dive into concepts such as stack management, pushing and popping values, and control flow terminology with practical examples. Enhance your understanding of
1 views • 119 slides
Understanding Enterprise Email Spam Prevention Techniques
Learn about the key strategies used by enterprises to combat email spam, including spam filters, SPF records, DMARC, DKIM, whitelisting, and SCL ratings. Discover how these tools work together to protect against spam, spoofing, and phishing attempts.
0 views • 8 slides
SHAKEN and STIRed: Current State of Anti-Spoofing and Robocall Mitigation
Exploring the challenges and efforts in combatting robocalls and caller spoofing in the telecommunications industry, focusing on restoring trust in voice networks through initiatives like SHAKEN (Secure Handling of Asserted information using toKENs) and STIR (Secure Telephone Identity Revisited). Th
0 views • 22 slides
Evaluating a Behavioural Science Approach for Increasing Advice Service Uptake
Derbyshire County Council is evaluating a behavioural science approach to enhance the uptake of advice services for residents in economic hardship. The project focuses on increasing caller referrals to support agencies, using Randomised Controlled Trials (RCTs) to evaluate interventions' impact and
2 views • 13 slides
Understanding Security Threats and Vulnerabilities in Computer Systems
In computer security, threats exploit vulnerabilities to breach security and cause harm. Vulnerabilities arise from system weaknesses, attacker access, and capability. Threats include spoofing, data tampering, repudiation, information disclosure, denial of service, and elevation of privilege. Catego
0 views • 13 slides
Understanding TCP Round-Trip Time Measurement
This presentation delves into the importance of measuring TCP round-trip time in the data plane, highlighting key reasons such as security against BGP hijacks and IP spoofing, performance enhancements, and improving user Quality of Experience. It explores monitoring at a vantage point, TCP sequence
0 views • 12 slides
Opioid Crisis Helpline Advisory Council Meeting Overview
The Opioid Crisis Helpline in Illinois offers confidential and free assistance to individuals and families affected by opioid use disorders. The helpline provides access to treatment, rehabilitation, and recovery support services, as well as referrals to comprehensive resources. Demographic data on
0 views • 16 slides
Financial Management and Cybersecurity: Essential Tips for Treasurers
A comprehensive guide covering topics such as budget development, treasurer's role responsibilities, and cybersecurity basics for treasurers. Learn about financial sustainability, board commitments, and protecting against cybersecurity threats like ransomware and spoofing scams. These insights aim t
0 views • 13 slides
Understanding Network Security Vulnerabilities and Attacks
Explore the world of network security vulnerabilities and attacks, including Denial-of-Service (DoS) and Distributed-Denial-of-Service (D-DoS), security flaws in the TCP/IP protocol suite, ICMP attacks, routing attacks, and TCP attacks. Learn about common security vulnerabilities such as address spo
0 views • 36 slides
Understanding x86-64 Stack and Register Usage at Carnegie Mellon
Explore the concepts of stack management, function invocation, and register usage in x86-64 architecture as taught in Carnegie Mellon's 15-213 recitation on Attack Lab. Learn about stack operations, caller vs. callee functions, and the conventions for using registers effectively. Gain insights into
0 views • 26 slides
Understanding Cybercrime: Types, Signs, and Prevention
Cybercrime involves various criminal activities targeting computers and networks, aiming to generate profit or cause harm. Types include website spoofing, ransomware, malware, IoT hacking, identity theft, and online scams. Signs of identity theft can manifest in credit, tax, child, medical, and crim
0 views • 6 slides
Understanding Cyber Threats in Today's Digital Landscape
Cyberspace is a vast realm encompassing the Internet, where we engage in various activities ranging from communication to entertainment. With the majority of children exposed to the online world, cybersecurity awareness is crucial to tackle the rising cyber threats. These threats include job frauds,
0 views • 33 slides
Evolved Addressing and Forwarding in Information-Centric Networks
The content discusses Evolved Addressing and Forwarding in Information-Centric Networks, focusing on an accountable Internet protocol (AIP) that addresses vulnerabilities at the IP level, such as source spoofing, DoS attacks, and route hijacking. AIP utilizes a hierarchy of self-certifying addresses
0 views • 16 slides
Developing Attack Defense Ideas in Ad Hoc Wireless Networks
This research delves into the challenges and security threats faced by ad hoc wireless networks, particularly in the context of connected vehicles. It explores various attacks such as distributed denial-of-service, spoofing, replay, and more, and aims to measure the impact of implementing security m
0 views • 30 slides
Regulatory Aspects of CPND, CLI, and OI in ITU Workshop on Caller ID Spoofing
The ITU Workshop on Caller ID Spoofing in Geneva addressed the regulatory aspects of Calling Party Number Delivery (CPND), Calling Line Identification (CLI), and Origin Identification (OI) in the context of the International Telecommunications Regulations (ITRs). Divergent views were discussed regar
0 views • 12 slides
Advanced AI Facial Recognition System with Turnstile Features
A comprehensive overview of the advanced AI facial recognition system - AIFACE-MARS, showcasing its unique features such as visible light facial recognition, anti-spoofing algorithms, multiple verification methods, hardware specifications, and integrated one-way bridge tripod turnstile features. The
0 views • 9 slides
Enhancing Wi-Fi Authentication Using Channel State Information
This research discusses enhancing Wi-Fi authentication by actively eliciting channel state information (CSI) to detect spoofing attacks. The challenge lies in obtaining the legitimate user's CSI and comparing it in real-time due to changing CSI and user traffic variations. The proposed approach invo
0 views • 27 slides
Enhancing Your Caller Skills: A Guide to Professional Development by Joe Uebelacker
Discover how to elevate your calling skills from local to international level through showmanship, stage presence, and strategic positioning. Joe Uebelacker offers valuable insights on self-assessment, workshops, and learning from successful callers. Find out where you fit in the calling hierarchy a
0 views • 19 slides
Understanding Exception Handling in Object-Oriented Programming
Exception handling in object-oriented programming enables a program to manage and recover from exceptional situations during runtime errors. Java uses exceptions to represent errors, allowing methods to throw exceptions that can be caught and handled by the caller, thus separating error detection an
0 views • 21 slides