Understanding AES Encryption in Computer Engineering
Advanced Encryption Standard (AES) is a powerful symmetric block cipher used in computer engineering for data encryption. Developed by NIST, AES supports key lengths of 128, 192, and 256 bits. The algorithm operates on a state array and consists of encryption phases like initial round, main rounds,
2 views • 8 slides
Columnar Transposition Cipher: Data Encryption Techniques at Mustansiriyah University Engineering College
Transposition ciphers, particularly the columnar transposition technique, are explored in the course "Data Encryption" at Mustansiriyah University Engineering College. The cipher involves rearranging message elements without changing their identities, making it crucial in modern block cipher designs
0 views • 4 slides
The Complex Relationship of Cleopatra and Mark Antony
Cleopatra, known for her political savvy and relationship with Julius Caesar and later Mark Antony, was a key figure in the power struggles of ancient Egypt and Rome. Contrary to historical stereotypes, Cleopatra was not depicted as withdrawn but as a strong, charismatic leader. Her alliance with Ma
0 views • 7 slides
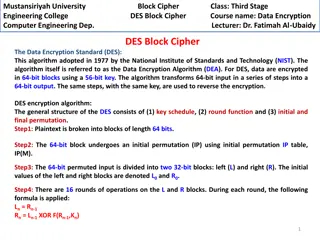
Understanding DES Block Cipher in Computer Engineering at Mustansiriyah University
Data Encryption Standard (DES) is a widely used algorithm for encrypting data in 64-bit blocks with a 56-bit key. This course at Mustansiriyah University covers the key components of DES, including the key schedule, round function, and initial/final permutation. Students learn about the encryption p
1 views • 8 slides
Evolution of Cryptography: From Ancient Techniques to Modern Security Mechanisms
Explore the evolution of cryptography from ancient techniques like the Caesar Cipher to modern security mechanisms like SSL, SSH, and IPSec. Learn how cryptography plays a crucial role in ensuring confidentiality, integrity, authentication, non-repudiation, and availability in network security. Disc
1 views • 62 slides
Notable Emperors and Structures of Ancient Rome
Julius Caesar, Augustus Caesar, Hadrian, Marcus Aurelius, Diocletian, and Caligula were significant figures in ancient Rome, each with their own contributions and characteristics. From Julius Caesar's military prowess to Augustus Caesar's establishment of the Roman Empire, and Hadrian's emphasis on
0 views • 11 slides
ADFGVX Cipher: Encryption and Decryption Techniques
Discover the ADFGVX cipher, a historical encryption method used to secure messages during World War I. Learn about Fritz Nebel and Gino Painvin, who played significant roles in its development. Explore the Polybius Square invented by Polybius in the 2nd century BC for converting letters to numbers.
0 views • 14 slides
Transposition Cipher Techniques in Modern Block Ciphers
Transposition ciphers, specifically columnar and double columnar transpositions, are explored in the context of data encryption and computer engineering at Mustansiriyah University Engineering College. These techniques involve rearranging message elements without changing their identities, providing
0 views • 4 slides
Understanding the Saints' Dilemma in Revelations
The dilemma faced by the Saints in the book of Revelations is whether they can bow down to the beast (Caesar) to receive a certificate of worship, seek forgiveness, worship God, and still attain salvation. The passages in Revelations 14 and 20 highlight the consequences of worshipping the beast, emp
0 views • 14 slides
Optimizing MIH SA Establishment for Single Radio Handover
This presentation discusses the optimization of MIH (Media Independent Handover) Security Association (SA) establishment for single radio handover. It covers the key points and methods proposed for enhancing the communication between Mobile Node (MN) and Top Point of Service (TPoS) using cipher suit
3 views • 6 slides
Understanding Small-State Noncryptographic Pseudorandom Number Generators
Explore the design and testing of small-state noncryptographic pseudorandom number generators, including definitions, rules of thumb, chisquare tests, existing and new generators, and more. Learn about block cipher encryption, hash functions, pseudorandom number generation, reversible mixing, and re
0 views • 46 slides
Understanding Block Ciphers in Cryptography
Explore the principles of block ciphers in modern cryptography, focusing on the Data Encryption Standard (DES) and its design principles. Learn about block cipher encryption, Feistel block cipher structure, n-bit block ciphers, ideal block ciphers, key length considerations, and challenges with idea
0 views • 44 slides
Understanding Encryption Techniques: From Transposition Ciphers to Rail Fence Ciphers
Explore the world of encryption techniques, diving into transposition ciphers and rail fence ciphers. Learn about encryption, decryption, plaintext, ciphertext, keys, and the art of secret writing. Discover how transposition ciphers reorder letters without changing their values and how rail fence ci
0 views • 26 slides
The Enigmatic Persona of Cassius in Shakespeare's Julius Caesar
Discover the complex character of Cassius in Shakespeare's Julius Caesar, a noble Roman warrior and ambitious politician who plays a key role in the conspiracy to overthrow Caesar. Known for his intelligence, arrogance, and strategic mindset, Cassius's beliefs in fate and free will add depth to his
0 views • 20 slides
Understanding Encryption: Keys, Algorithms, and Applications
Encryption plays a crucial role in securing data transmission and storage. It involves using keys and algorithms to convert plaintext information into a cipher that can only be deciphered with the correct key. This article explores different encryption methods, such as private and public key encrypt
0 views • 62 slides
Emperors and Structures of Ancient Rome
Julius Caesar expanded the Roman Republic through conquests, Augustus Caesar transformed Rome into an empire, Hadrian was known for good governance and building, Diocletian split the empire, Caligula's reign turned cruel, and Nero's rule was marked by cruelty and the infamous burning of Rome.
0 views • 10 slides
Key Principles in Cryptography: Kerckhoff's and Key Space
Understanding fundamental principles in cryptography, including Kerckhoff's principle, key space requirements, and the importance of secure private-key encryption. Exploring the Shift Cipher's security, key space size considerations, and the need for heuristic constructions for proving scheme securi
0 views • 51 slides
Overview of Modern Cryptography and Data Encryption Standard (DES)
Exploring modern cryptography including symmetric key block ciphers, public key ciphers, stream ciphers, and post-quantum ciphers. Focus on Data Encryption Standard (DES), Simplified DES, Feistel cipher, key schedule, expansion function, S-Box, DES encryption, and decryption processes.
0 views • 37 slides
Julius Caesar Study Agenda and Quiz Preparation
Explore the study agenda for a Julius Caesar quiz on Act III, Scene 1, covering key roles and moments from the play. Get ready by revising act summaries, specific questions, and important scenes to excel in the quiz.
0 views • 19 slides
Roman Political History: From Rise of Pompey to Reign of Augustus
In the tumultuous period of Roman history from the rise of Pompey to the reign of Augustus, we witness pivotal events such as the Alliance of the First Triumvirate, the civil war between Pompey and Julius Caesar, Caesar's assassination, the rise of Octavian, and the establishment of the Second Trium
0 views • 20 slides
Understanding Cryptography Basics and Toolbox
Cryptography serves the goals of managing who can view data, ensuring data integrity, and verifying the origin of data. It involves dramatis personae like Alice, Bob, Eve, and Oscar. The toolbox includes hash functions, symmetric encryption, and asymmetric encryption. Hash functions play a crucial r
0 views • 32 slides
English 10 - Contemplation on Freedom and Tyranny in "Julius Caesar
Explore the concepts of freedom and tyranny through contemplation questions and a debate on whether Brutus should have stabbed Julius Caesar in Act IV of William Shakespeare's "Julius Caesar." Engage in participatory budget voting and delve into root word analysis in English 10.
0 views • 19 slides
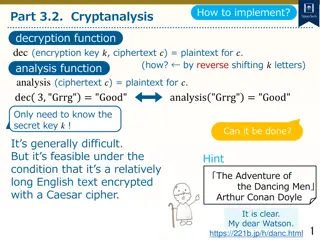
Understanding Cryptanalysis: Key Concepts and Techniques
Cryptanalysis is a fundamental aspect of cryptography that involves decoding encrypted communications and messages. This topic delves into the basic cryptographic tools, such as the Caesar cipher, and explores how encryption and decryption functions work. By understanding cryptanalysis, you can anal
0 views • 12 slides
Cryptanalysis and Decryption Techniques for Caesar Cipher
Learn how to decrypt Caesar cipher text using cryptanalysis techniques by analyzing letter frequencies and determining the secret key through character analysis. Explore methods to count character frequencies and find the most common letter to decipher encrypted messages.
0 views • 11 slides
The Fall of the Roman Republic: Turmoil, Reforms, and Caesar's Ascendancy
The Roman Republic faced internal strife due to the rich-poor divide, loss of small farms, and political corruption. Failed reforms by the Gracchus brothers led to military involvement in politics, culminating in Julius Caesar's rise to power as dictator for life, ushering in significant changes to
0 views • 21 slides
Cleopatra and Julius Caesar: Assessment Follow-Up
Strategic approach to analyzing Cleopatra and Julius Caesar's involvement in securing her throne, assessing different arguments, sources, and reasoning levels. Includes an example answer and discussion on the extent of Caesar's influence on Cleopatra's success.
0 views • 7 slides
Historical Figures and Literary Works of Shakespeare
William Shakespeare, the renowned English poet, playwright, and actor, is celebrated for his contributions to literature. Alongside his famous works like "Julius Caesar," he is considered the greatest writer in the English language. The play, set in ancient Rome, delves into themes of honor, patriot
0 views • 52 slides
Cryptographic Center in Novosibirsk: Advancements in Cryptography and Research
The Cryptographic Center in Novosibirsk, established in 2011, focuses on advancing cryptography through research, education, and international collaborations. With a team of researchers and students, the center explores various aspects of cryptography, including cryptographic Boolean functions, ciph
0 views • 33 slides
Exploration of Cryptography and Secure Communication Methods
Delve into the concepts of cryptography, data hiding, and secure communication methods such as Diffie-Hellman key exchange. Discover how Bob safely sends a ring to Alice, the use of Caesar cipher method, and the importance of mathematical principles in ensuring secure communication protocols. Learn
0 views • 22 slides
Introduction to Cryptology in Algebra 2 Classroom
Engage students in a high school Algebra 2 class by exploring cryptology concepts such as coding, hexadecimal systems, substitution ciphers, and the Vigenere cipher. The lesson plan includes activities like solving puzzles, introducing binary systems, converting to hexadecimal, and writing messages
0 views • 16 slides
Fun Spy Challenges for Beavers - Crack the Codes!
Dive into exciting spy missions with a group of clever beavers! Decode secret messages using various encryption techniques such as switching codes, letter grouping, Pig Pen cipher, Morse code, and Caesar cipher. Test your spy skills as you unravel each challenge to reveal hidden messages. Unleash yo
0 views • 6 slides
Gaius Julius Caesar: Rise to Power and Triumphs
Born in 100 BC to a struggling family, Gaius Julius Caesar defied the odds, rising through the political ranks with unmatched ambition and military prowess. From conquering Gaul to forming alliances like the First Triumvirate, his journey was marked by triumphs and risky decisions, culminating in th
0 views • 18 slides
Understanding Encryption and its Importance in Everyday Life
Encryption is a crucial process that transforms messages into secret codes, ensuring only intended recipients can decipher them. This review delves into the significance of encryption for online activities, cracking different cipher methods, and recognizing security flaws. Discover how computational
0 views • 9 slides
The Events of the Ides of March in Ancient Rome
Explore the betrayal and assassination of Julius Caesar on the Ides of March, including the motivations of the conspirators, the murder plot, and the aftermath with Mark Antony and Octavian seeking revenge. Witness the internal struggles of Brutus, Cassius, and Decimus as they conspire against Caesa
0 views • 13 slides
Crack the Code: The Fascinating World of Cryptography
Discover the intriguing world of cryptography through a journey into the history and methods of code-making and code-breaking. Uncover the importance of codes in everyday life, from book ISBNs to encrypted internet data, and learn about classic techniques like Caesar shifts. Test your skills by deco
0 views • 4 slides
The Impact of Cleopatra and Caesar's Relationship on Egypt and Rome
The relationship between Cleopatra and Caesar had significant political implications, leading to Cleopatra ruling Egypt with stability and autonomy. While beneficial for both Cleopatra and Caesar personally, the relationship faced opposition and challenges from Rome and Alexandria. This historical a
0 views • 6 slides
Fundamentals of Cryptography and Network Security
Explore the basics of cryptography, including classical encryption techniques, terminology definitions, types of encryption operations, cryptanalysis objectives and attacks, and the concept of cipher strength. Uncover the principles and methods behind encryption and decryption, key distinctions betw
0 views • 52 slides
Unlock the Challenges in Cipher Cove: A STEM Adventure
Explore Cipher Cove and tackle five cryptographic challenges involving different ciphers such as Caesar Shift, Pigpen, Transposition, Substitution, and Periodic Table. Put your problem-solving skills to the test by deciphering hidden clues and codes to progress through each challenge and ultimately
0 views • 6 slides
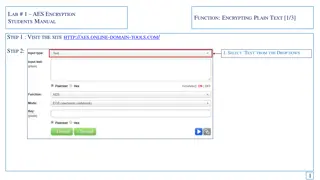
Guide to AES Encryption for Students - Encrypting and Decrypting Text
This manual provides a step-by-step guide on AES encryption for students. Learn how to encrypt plain text using a secure key, generate cipher text, and then decrypt it back to the original message. Follow the instructions on a specific website, enter your text, select encryption options, and save th
0 views • 6 slides
Understanding Loops and ASCII Values in Python
Learn about while loops, fencepost loops, and sentinel loops in Python programming. Explore how ASCII values are assigned to characters and how to manipulate them. Practice a Caesar cipher program to encrypt messages and discover common pitfalls in loop structures. Gain insights into the importance
1 views • 22 slides