Automatic Incremental View Maintenance in DBSP: A Comprehensive Overview
Analyzing the automatic incremental view maintenance for rich query languages like DBSP. Discussing concepts such as incremental computation reuse, streaming language, relational computations, streaming operators, and more. Explore the conversion of arbitrary DBSP programs to incremental ones and th
4 views • 24 slides
Semi-Automatic Turnstile Gate
Automatic turnstile gates are a common sight in various public places such as train stations, stadiums, airports, and office buildings. They serve as a means of crowd control and security, allowing only one person to pass through at a time. These gates are typically equipped with sensors that detect
8 views • 1 slides
Automatic Gate Motor Abu Dhabi
Maintenance UAE is the eminent company to get high-quality service for automatic gate motor Abu Dhabi - Automatic Gate Motor Repair Abu Dhabi
0 views • 10 slides
Automatic Gate Motor Repair Abu Dhabi
Maintenance UAE is the eminent company to get high-quality service for automatic gate motor Abu Dhabi - Automatic Gate Motor Repair Abu Dhabi
0 views • 10 slides
Enhanced Security in Multiparty Computation
Explore the improved black-box constructions of composable secure computation, focusing on definitions, objectives, and the formalization basics of multiparty computation (MPC). Learn about the motivating security aspects in MPC and the real/ideal paradigm. Discover how MPC security involves compari
1 views • 68 slides
Automatic Recognition of Higher Education Qualifications Treaty Summary
Importance of automatic recognition of qualifications in higher education has been emphasized, leading to initiatives like the Treaty on Automatic Recognition of Higher Education Qualifications by Baltic and Benelux states. This treaty aims to enhance mutual trust, transparent recognition, and contr
1 views • 8 slides
Automatic Motorcycles & Sport Bikes | Venom Motorsports USA
Explore our selection of automatic motorcycles and sport bikes at Venom Motorsports USA. Featuring high-performance automatic sport bikes, our collection ensures a smooth and thrilling ride. Find models that offer a perfect blend of style, power, and
2 views • 8 slides
Automatic Motorcycles & Sport Bikes | Venom Motorsports USA
Explore our selection of automatic motorcycles and sport bikes at Venom Motorsports USA. Featuring high-performance automatic sport bikes, our collection ensures a smooth and thrilling ride.
2 views • 8 slides
Secure Computation Techniques in RAM Models with Efficient Automation
Explore the automation of efficient RAM-model secure computation techniques, including examples such as secure binary search. Discover how traditional solutions using circuit abstractions can be improved for sub-linear time computation through methods like Oblivious RAM. Learn about techniques such
0 views • 37 slides
Secure Multiparty Computation for Department of Education Data Sharing
This report discusses the use of Secure Multiparty Computation (SMC) to enable sharing of sensitive Department of Education data across organizational boundaries. The application of SMC allows for joint computation while keeping individual data encrypted, ensuring privacy and security within the Nat
0 views • 15 slides
Advancements in Active Secure Multiparty Computation (MPC)
Delve into the realm of secure multiparty computation under 1-bit leakage, exploring the intersection of DP algorithms, MPC, and the utilization of leakage for enhanced performance. Discover the overhead implications of achieving active security, as well as the evolution of secure computation protoc
0 views • 43 slides
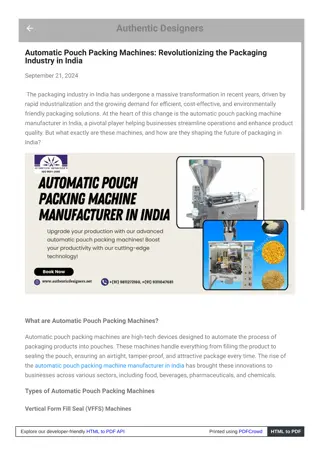
Automatic Pouch Packing Machine Companies in India
When evaluating Automatic Pouch Packing Machine Companies in India, industry leaders are distinguished by their commitment to innovation, quality, and customer support. The best Automatic Pouch Packing Machine Manufacturer in India integrates advance
0 views • 11 slides
Key Factors to Look for in Automatic Labeling Machine Manufacturers in India
When choosing an automatic labeling machine, it\u2019s crucial to consider several key factors to ensure optimal performance. Look for an Automatic Labeling Machine Manufacturer in India with a strong reputation for quality and reliability. Evaluate
0 views • 3 slides
Automatic Motorcycles for Effortless Riding | Venom Motorsports USA
Discover the convenience and ease of automatic motorcycles at Venom Motorsports USA. Our collection features a range of automatic bikes designed to simplify your riding experience. Perfect for both new and experienced riders, these motorcycles offer
2 views • 8 slides
Embedded System for Automatic Washing Machine using Microchip PIC18F Series Microcontroller
The design of an embedded system for an automatic washing machine using Microchip PIC18F series microcontroller allows for upgradeability and customization. It features manual, fully automatic, and semi-automatic modes, with user-friendly interfaces such as a keypad and LCD display. The system ensur
0 views • 9 slides
COMET: Code Offload by Migrating Execution - OSDI'12 Summary
The research paper discusses COMET, a system for transparently offloading computation from mobile devices to network resources to improve performance. It outlines the goals of COMET, its design, and evaluation, focusing on distributed shared memory and bridging computation disparity through offloadi
0 views • 31 slides
Actively Secure Arithmetic Computation and VOLE Study
Exploring actively secure arithmetic computation and VOLE with constant computational overhead at Tel Aviv University. Understanding how functions are represented in secure computation using arithmetic circuits over boolean circuits. Efficiently evaluating arithmetic circuits over large finite field
0 views • 36 slides
Reforming Automatic Renewal and Continuous Service Offers Act
The bill aims to regulate automatic renewal and continuous service offers by requiring businesses to provide clear terms and obtain customer consent. It includes provisions for free trials, cancellation policies, refund processes, and notification of changes. Exemptions are provided for specific ind
0 views • 7 slides
Enhancing Multi-Party Computation Efficiency Through ORAM Techniques
Explore the realm of efficient random access in multi-party computation through the reevaluation of classic schemes and the introduction of new approaches. Discover the potential of ORAM in improving performance and reducing costs in various computational tasks, such as secure multi-party computatio
0 views • 22 slides
Exploring Secure Computation in the Age of Information
Welcome to Secure Computation Lecture 1 by Arpita Patra. The course covers evaluation policies, projects, and references in the realm of secure computation. The content delves into the significance of information security across various sectors, emphasizing the importance of safeguarding sensitive d
0 views • 36 slides
Secure Two-Party Computation and Basic Secret-Sharing Concepts
In today's lecture of "Foundations of Cryptography," the focus is on secure two-party and multi-party computation, emphasizing semi-honest security where Alice and Bob must compute without revealing more than necessary. Concepts such as real-world vs. ideal-world scenarios, the existence of PPT simu
0 views • 27 slides
Linear Communication in Secure Multiparty Computation for Efficient and Fast Processing
The research focuses on achieving perfectly secure multiparty computation (MPC) with linear communication and constant expected time. It explores efficient approaches using a broadcast-hybrid model and P2P communication, aiming to balance speed and efficiency in MPC. The study highlights the importa
0 views • 23 slides
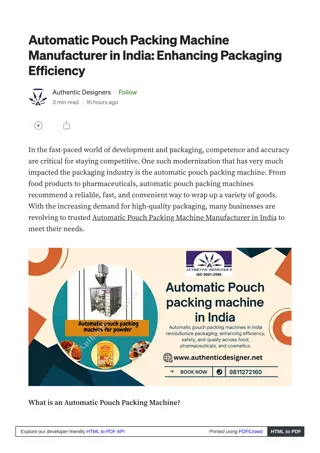
Known Automatic Pouch Packing Machine Manufacturer in India: Authentic Designers
Automatic pouch packing machines are ideal for food, pharmaceuticals, and consumer goods, they accommodate diverse pouch sizes and materials. Affordable automatic pouch packing machine manufacturer in India, like Authentic Designers are setting new s
2 views • 4 slides
WylasTiming - Wireless Semi-Automatic Timing System Overview
WylasTiming is a wireless semi-automatic timing system developed in Australia, utilizing off-the-shelf hardware and Android handsets. It provides accurate timing with automatic race starting and instantaneous data transmission. The timekeeper simply stops the clock at the end of the race, and data i
0 views • 15 slides
Investigation of the Effects of Automatic Scoring Technology on Human Raters' Performances in L2 Speech Proficiency Assessment
This research explores the impact of automatic scoring technology on human raters in assessing L2 speech proficiency. It aims to compare the performances of expert and non-expert teachers, assess whether providing detailed feedback influences their judgments, and determine how to enhance the collabo
0 views • 20 slides
Secure Computation Challenges and Solutions in Data Mining
Exploring the intersection of secure computation and data mining, this content uncovers key challenges such as improving algorithms, converting programs for secure computation, and addressing parallelizability issues. It highlights the importance of cryptography in ensuring data privacy and presents
0 views • 30 slides
Covert Computation: Ensuring Undetectable Engagement
Covert computation aims to conceal the fact that computation is occurring and hide engagement in certain tasks like secure computation, authenticated key exchange, and more. By making messages indistinguishable and utilizing steganographic channels, it becomes possible to keep the activities covert
0 views • 16 slides
Overview of Turing Machines: Introduction, Tape, and Computation
Turing Machines are fundamental in the theory of computation, capable of recognizing all computable languages. They consist of a Finite State Machine combined with an infinite tape. The tape is initialized with input on the left end, and a TM's computation can either halt by entering special accept
0 views • 29 slides
Computation for Real Estate Sector in Bangalore Branch of ICAI
Practical overview of GST computation for real estate transactions in Bangalore, with details on old rates with ITC and new rate regime effective from April 1, 2019. The content discusses different transactions, conditions for new rates without ITC, and provides insights on the 80:20 computation met
0 views • 39 slides
Fides: A System for Verifiable Computation Using Smart Contracts
Fides presents a system for verifiable computation using smart contracts, focusing on blockchain basics, Ethereum, smart contracts, and outsourcing computation. It explores key components of blockchain, Ethereum's decentralized computing platform, properties of smart contracts, and the concept of ve
0 views • 25 slides
Insights into Secure Computation with Minimal Interaction
This paper revisits the concept of secure computation with minimal interaction, focusing on the challenges and possibilities of achieving secure multiparty computation in 2 rounds. Specifically exploring scenarios with 3 and 4 parties, the study delves into the reasons for choosing n=3, n=4, and t=1
0 views • 23 slides
Overview of Income Computation and Disclosure Standards (ICDS)
The Income-tax Act, 1961 introduced Income Computation and Disclosure Standards (ICDS) to be followed by certain assesses for computation of income. ICDS applies to taxpayers using the mercantile system of accounting from the Assessment Year 2016-17 onwards. Non-compliance with ICDS can lead to Best
0 views • 49 slides
Automatic Labeling Machine from Authentic Designers : Increase Your Efficiency
Enhance your production process with the best automatic labeling machine, designed to maximize efficiency and accuracy. Ideal for businesses of all sizes, the automatic labeling machine, from Authentic Designers helps streamline operations, save time
0 views • 10 slides
Blackbox Verifiable Computation Scheme Overview
This summarized content discusses the concept of blackbox verifiable computation, focusing on the challenges faced by clients and servers, the role of helper oracles, positive results utilizing homomorphic encryption, and background information on Random Self Reducible (RSR) functions. The protocol
0 views • 20 slides
Parallel Computation for Matrix Multiplication
Matrix multiplication is a fundamental operation with diverse applications across scientific research. Parallel computation for matrix multiplication involves distributing the computational workload over multiple processors, improving efficiency. Different algorithms have been developed for multiply
0 views • 36 slides
Advances in Completely Automatic Decoder Synthesis
This presentation by Y.C. Chou and H.S. Liu on "Towards Completely Automatic Decoder Synthesis" covers topics such as motivation, preliminary concepts, main algorithms, and experimental results in the field of communication and cryptography systems. The content delves into notation, SAT solvers, Cra
0 views • 35 slides
Top Automatic Pouch Packing Machine Manufacturers for Efficient Packaging
Explore the best packaging solutions with Automatic Pouch Packing Machine. These Automatic Pouch Packing Machine Manufacturer in India machines provide unmatched efficiency, precision, and cost savings for industries like food, pharmaceuticals, and
0 views • 11 slides
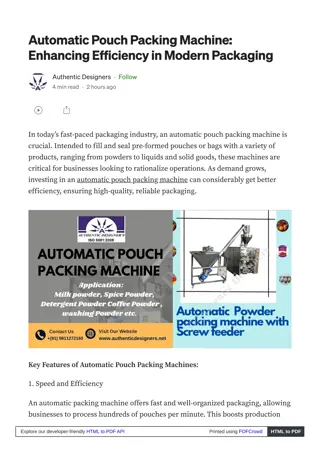
Advanced Automatic Pouch Packing Machines for Efficient Packaging
Our automatic pouch packing machine offers the perfect solution for businesses looking to enhance packaging efficiency. Automatic pouch packing machine designed to fill and seal pouches with precision, these machines handle a wide range of products,
0 views • 11 slides
How Automatic Adjustments in Microwave Ovens Simplify Cooking
Discover how automatic adjustments in microwave ovens make cooking easier by optimizing time, power, and precision for perfectly cooked meals every time. \/\/lahorecentre.hashnode.dev\/how-automatic-adjustments-in-microwave-ovens-simplify-cooking
7 views • 1 slides
Advanced Techniques in Multi-Party Computation
Explore cutting-edge methods in Multi-Party Computation (MPC), including leveraging Fully Homomorphic Encryption (FHE) for minimal round complexity, constructing MPC directly via FHE techniques, and simplifying multi-key FHE constructions for efficient decryption. Learn about key concepts such as di
0 views • 17 slides