Semi-Supervised Credit Card Fraud Detection via Attribute-Driven Graph Representation
Explore a novel approach for detecting credit card fraud using a semi-supervised attribute-driven graph representation. The technique leverages temporal aggregation and attention layers to automatically unify heterogeneous categorical attributes and detect fraudulent transactions without label leaka
1 views • 23 slides
Understanding Variables and Control in Research Design
In research design, variables play crucial roles as either dependent or independent factors, with extraneous variables potentially affecting study outcomes. Controlling for extraneous variables is essential to attribute effects solely to the independent variables. Research hypotheses aim to test pre
0 views • 6 slides
Acoramidis Improves Cardiac Function in Transthyretin Amyloid Cardiomyopathy
Acoramidis, a next-generation TTR stabilizer, shows promising results in improving cardiac function and promoting regression in Transthyretin Amyloid Cardiomyopathy. The ATTRibute-CM Cardiac Magnetic Resonance Substudy evaluated changes in cardiac structure, function, and amyloid burden after treatm
0 views • 8 slides
Best Property Appraisal in Khandallah
Are you looking for the Best Property Appraisal in Khandallah? Then contact Sarah Mairs Real Estate. They have regularly distinguished myself among the top 30 Leaders\u2019 agents as a monthly top lister or top seller. They attribute their success to
5 views • 6 slides
Understanding Hash Join Algorithm in Database Management Systems
In this lecture, Mohammad Hammoud explores the Hash Join algorithm, a fundamental concept in DBMS query optimization. The algorithm involves partitioning and probing phases, utilizing hash functions to efficiently join relations based on a common attribute. By understanding the intricacies of Hash J
1 views • 41 slides
Understanding Design Tactics and Quality Attributes
Quality attributes play a crucial role in system design by indicating how well a system meets stakeholder needs. Architecturally Significant Requirements (ASRs) have a profound impact on system architecture. Quality attributes can be operational (availability, reliability) or developmental (modifiab
2 views • 28 slides
Theories on the Origin of State: Divine, Force, Patriarchal, and More
Various theories such as Divine Origin, Force Theory, Patriarchal Theory, and others explain the origin of the state. Divine theories attribute state creation to God, while Force Theory emphasizes the strong subjugating the weak to establish authority. Each theory offers unique perspectives on the h
1 views • 24 slides
Enhancing Organizational and Individual Creativity Techniques in Entrepreneurship
Tips for enhancing organizational and individual creativity in entrepreneurship include fostering a culture that values creativity, embracing diversity, tolerating failure, providing support, and encouraging innovative thinking. Techniques like brainstorming, mind mapping, rapid prototyping, and att
0 views • 22 slides
Understanding Psychological Theories of Criminal Behavior
Psychologically-based criminologists attribute criminal behavior to individual factors such as negative early childhood experiences and inadequate socialization, leading to criminal thinking patterns and incomplete cognitive development. Probation and parole practices are influenced by rehabilitatio
0 views • 30 slides
Understanding Ciphertext Policy Attribute Based Encryption (CPABE)
Ciphertext Policy Attribute Based Encryption (CPABE) is a method that links access policies with ciphertext, allowing decryption based on user attributes rather than specific keys. This enhances security and flexibility in data access control. The encryption system also addresses challenges in remot
0 views • 26 slides
Understanding Naive Bayes Classifiers and Bayes Theorem
Naive Bayes classifiers, based on Bayes' rules, are simple classification methods that make the naive assumption of attribute independence. Despite this assumption, Bayesian methods can still be effective. Bayes theorem is utilized for classification by combining prior knowledge with observed data,
0 views • 16 slides
Understanding Semantic Roles in Linguistics
Semantic roles, also known as theta roles, play a crucial part in understanding the relationships between participants and verbs in a sentence. They include agents, experiencers, causers, positioners, subject complements, and objects. Agents are typically the doers of actions, experiencers receive e
1 views • 18 slides
Understanding Semantic Roles in Sentence Structure
Semanticists analyze sentences based on semantic structure rather than traditional syntactic terms like subject and object. Instead, they use semantic terms such as Agent, External causer, Instrument, Affected, Recipient, and Locative. These terms help describe how people and things participate in r
1 views • 26 slides
Essential Heroic Trait Comparison: Atticus vs. Another Hero
A comparative analysis through an argumentative synthesis essay between Atticus from TKAM and another hero, focusing on the most crucial trait all heroes should possess. The essay addresses opposing claims and highlights the importance of a singular heroic attribute.
0 views • 25 slides
Christianity: Key Beliefs, Teachings, and Jesus' Sacrifice
Christianity is a monotheistic religion centered on beliefs in God's omnipotence, benevolence, and the existence of evil. Christians attribute their moral conscience and sense of right and wrong to God. The faith also incorporates teachings about Jesus' suffering and crucifixion, emphasizing forgive
3 views • 9 slides
Addressing Childhood Obesity: A Call for Action in London
Childhood obesity in London is a significant concern, with 1 in 3 children in Year 6 being overweight or obese. This issue has far-reaching impacts on both children and society, including health problems and increased healthcare costs. Experts attribute the rising obesity rates to environmental and
2 views • 9 slides
Understanding LXI Network Security in Industrial Environments
LXI Security Overview provides insights into the critical attribute of security in industrial networks, focusing on LXI instruments connected to company networks. The presentation covers security standards, communication channels, encryption, PKI, certificates, and proposals for secure communication
1 views • 41 slides
Encouraging Creative Thinking in Islam: Lessons from Quran and Hadith
Explore the concept of creative thinking in Islam through the lens of Allah's attribute as the Originator (Al-Badi'u). Discover how the Quran and Hadith narratives emphasize the importance of innovation, development, and wisdom in solving complex problems and benefiting society. Delve into stories o
0 views • 16 slides
GIS Data Models for Spatial Planning Training in Maputo, Mozambique
Explore the concepts of GIS data models including vector vs. raster, spatial relationships, spatial operations, and representation of real-world entities in a spatial database. Understand how spatial data models are used to manipulate spatially-referenced information and define the spatial location
1 views • 32 slides
Understanding Forms: Checkboxes, Select Boxes, Radio Buttons
Explore how to create and differentiate checkboxes, select boxes, and radio buttons in forms. Learn about the value attribute, the importance of naming elements clearly, and the purpose behind sharing group names for radio buttons. See practical examples and gain insights into enhancing user experie
0 views • 21 slides
Overview of Attribute Control Charts in Quality Management
Attribute control charts are used in quality management to monitor the conformity of products or services based on specific characteristics. Unlike variable charts, attribute charts categorize items as conforming or non-conforming. This summary discusses the importance of attribute charts, focusing
0 views • 71 slides
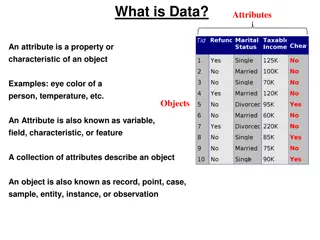
Understanding Data Attributes and Types for Analysis
Exploring the concept of data attributes, this information covers attributes as properties of objects, the distinction between experimental and observational data, types of attributes like qualitative and quantitative, and the properties of attribute values. It also delves into examples and categori
2 views • 32 slides
Understanding Decision Trees in Machine Learning
Decision trees are a popular machine learning technique that maps attribute values to decisions. They involve tests that lead from the root to leaf nodes, with each internal node representing a test on an attribute. The use cases range from the restaurant waiting problem to boolean classification an
2 views • 21 slides
Understanding Attribute Selection Measures in Decision Trees
Decision trees are popular in machine learning for classification tasks. This content discusses the importance of attribute selection measures such as Information Gain, Gain Ratio, and Gini Index in constructing accurate decision trees. These measures help in selecting the most informative attribute
0 views • 16 slides
Understanding the C4.5 Algorithm in Machine Learning
Explore the C4.5 algorithm, a powerful tool in the realm of machine learning. Delve into topics such as numeric attributes, information gain, entropy calculations, and handling missing values. Learn about the importance of attribute selection, class-dependent discretization, and making optimal split
0 views • 17 slides
Introduction to Decision Tree Classification Techniques
Decision tree learning is a fundamental classification method involving a 3-step process: model construction, evaluation, and use. This method uses a flow-chart-like tree structure to classify instances based on attribute tests and outcomes to determine class labels. Various classification methods,
5 views • 20 slides
Understanding Data Preparation in Data Science
Data preparation is a crucial step in the data science process, involving tasks such as data integration, cleaning, normalization, and transformation. Data gathered from various sources may have inconsistencies in attribute names and values, requiring uniformity through integration. Cleaning data ad
1 views • 50 slides
Detection and Attribution of Flow and Sediment Fluxes in the Nile Basin
This study aims to detect and attribute climate change impacts on flow and sediment loads in the Nile basin using climate data and hydrological models. The research focuses on historical data and involves evaluating models, completing paper writing, and finishing the detection and attribution analys
0 views • 4 slides
Understanding Upper Airway Cough Syndrome and Chronic Cough Causes
Upper Airway Cough Syndrome (UACS) encompasses conditions like rhinitis and sinusitis, leading to chronic cough lasting more than 8 weeks. Common causes include asthma, GERD, and airway diseases. Differences in terminology between countries exist, with UACS being more widely accepted in the US. The
0 views • 42 slides
Understanding Global Warming and the Greenhouse Effect
Scientists attribute the observed global warming trend to human activities that enhance the greenhouse effect, trapping heat in the atmosphere. The greenhouse effect, crucial for life on Earth, involves gases like water vapor and methane that contribute to warming. Nitrous oxide, another potent gree
0 views • 13 slides
Overview of IG3IS and Global Greenhouse Gas Watch
IG3IS, the Integrated Global Greenhouse Gas Information System, serves as a bridge between greenhouse gas measurement-based data and decision-making for governments and industries. It aims to quantify, attribute, and track changes in greenhouse gas emissions through a hybrid approach combining emiss
3 views • 12 slides
The Devastating Impact of Colony Collapse Disorder on Honey Bees
A profound look into the catastrophic effects of Colony Collapse Disorder (CCD) on honey bee populations, causing the loss of millions of beehives and threatening crop pollination. Scientists attribute CCD to a deadly mix of fungicides and pesticides found in pollen samples, disrupting bees' neurolo
0 views • 6 slides
Engineering Graduate Attribute Development Workshop at Queen's University
This workshop, led by Brian Frank, Director of Program Development at the Faculty of Engineering and Applied Science, focused on applying assessment principles to CEAB graduate attribute requirements and planning processes for program improvement. The session outcomes included using tools, technolog
0 views • 76 slides
Enhancing Math Instruction Through Reflective Practice
Explore strategies for implementing and maintaining fidelity in math tasks, investigate attribute changes with partners, set lesson goals, select examples for class discussions, and emphasize making connections among mathematical concepts. Reflect on linear vs. quadratic equations and advantages of
0 views • 17 slides
Genetic Algorithm for Attribute Selection in Data Mining
Genetic algorithm (GA) is a powerful method for attribute selection in data mining as it efficiently explores numerous attribute combinations. By choosing the most important features and ignoring the rest, GA can enhance the data analysis process through methods like feature extraction and artificia
0 views • 41 slides
PEIA Open Enrollment Plan Year 2023 - Important Updates
PEIA Open Enrollment for the Plan Year 2023 is scheduled from April 2 to May 15. Changes made during this period will be effective from July 1. Benefit Coordinators must approve any changes by May 20. Members can make changes by visiting the PEIA website, calling the helpline, or filling out forms o
0 views • 36 slides
Shibboleth Identity Provider V3 Deployment Considerations and Key Differences for V2 Deployers
Configuration in V3 involves smaller files divided by topics, use of Velocity templates for interfaces, and separate read-only system files for safe upgrades. The V2 to V3 upgrade brings changes in XML files like attribute-resolver.xml and relying-party.xml. Clustering options and quick new features
0 views • 9 slides
Understanding Vertical Fragmentation in Distributed Information Systems
Vertical fragmentation in distributed information systems involves partitioning a relation into smaller fragments based on attributes and primary keys to improve application performance. Information requirements include attribute affinity and access frequencies, with examples of attribute usage and
0 views • 12 slides
Understanding Decision Trees in Classification
Decision trees are a popular machine learning algorithm for classification tasks. They consist of nodes representing conditions, branches indicating decisions, and leaves representing outcomes. By choosing the best attribute and splitting data recursively, decision trees can efficiently classify dat
0 views • 47 slides
Advanced Concepts in Association Analysis: Handling Categorical Attributes
Explore advanced concepts in association analysis, focusing on the handling of categorical attributes. Learn how to apply association analysis to non-asymmetric binary variables, including examples and potential solutions for skewed attribute value distributions. Discover techniques for managing att
0 views • 48 slides