Protection Analysis using the PAF
In this session, participants will learn how to utilize the Protection Analysis Framework (PAF) and its tools to conduct effective protection analysis. The session covers an overview of PAF, understanding its pillars, and analyzing data to comprehend essential protection concepts. Key points include
5 views • 48 slides
Red, Blue, Purple Team Development Discussion Panel
Explore best practices for team development in RBP security operations, focusing on operationalizing security focuses, assessing operator capabilities, implementing development pillars, and utilizing cyber ranges for hands-on skills training. Learn how to optimize security insight, architecture desi
0 views • 13 slides
The Digital Personal Data Protection Act 2023
The Digital Personal Data Protection Act of 2023 aims to regulate the processing of digital personal data while balancing individuals' right to data protection and lawful data processing. It covers various aspects such as obligations of data fiduciaries, rights of data principals, and the establishm
3 views • 28 slides
Understanding Information Flow in Software Security
Explore the concept of information flow in software security, focusing on implicit data flows from confidential sources to sinks. Learn about threat models, side channels, and defending against potential attacks in practical contexts. Delve into the complexities of maintaining security while conside
5 views • 26 slides
Governance and Managerial Leadership of Formal Social Protection in Africa: Insights from Cameroon's National Social Insurance Fund (CNPS)
This presentation delves into the governance and managerial leadership of formal social protection in Africa, focusing on Cameroon's CNPS system. It discusses the institutional evolution of social protection, the challenges faced by bureaucratic and political stakeholders, and the roles of various s
0 views • 8 slides
The Fight - A Story of Friendship and Understanding
Ranji finds himself in a fight over the rights to a pool but ends up befriending his adversary through a series of challenges and understanding. Despite initial conflict, they learn from each other, eventually becoming friends and forming a bond over shared experiences.
0 views • 9 slides
Bankruptcy Motion Practice Essentials
Dive into the key aspects of bankruptcy motion practice, from contested matters to adversary proceedings. Learn about the rules and guidelines, required documents for motions, and best practices for drafting motions in bankruptcy cases.
0 views • 12 slides
Eye Protection Training for Workplace Safety
Understand the importance of proper eye protection at work, including identifying at-risk job functions, selecting the right PPE, and knowing responsibilities for employees and employers. Training covers when PPE is necessary, how to use, maintain, and dispose of it properly, and the need for retrai
2 views • 28 slides
Understanding the General Data Protection Regulation (GDPR) and Data Protection Bill
The General Data Protection Regulation (GDPR) is a set of rules aimed at safeguarding individuals' personal data and privacy rights, with key changes from the previous Data Protection Act 1998. The GDPR introduces transparency, consent requirements, enhanced individual rights, breach notifications,
3 views • 40 slides
Exploring Att&ck Matrix: Engage Ludicrous Speed
Dive into the world of the Mitre Att&ck Matrix, where crazy ampersands and Trebuchet Font cues you in on how to engage Ludicrous Speed and understand the basics of attacker/adversary tactics, techniques, and common use cases. Explore matrices, prevent attacks, and work programmatically with Att&ck u
0 views • 26 slides
Abundant Life: Key to Success Through God's Help
Embrace the abundant life prepared for success through knowing that God sees, hears, and strengthens us. His help subdues our adversary, and Jesus advocates for us. Revelation of His thoughts empowers us to overcome challenges and achieve success, reflecting God's desire for our prosperity and victo
0 views • 10 slides
Groundskeeping Safety and Personal Protective Equipment Training
This presentation covers essential information on groundskeeping safety and the proper use of personal protective equipment (PPE). Topics include head protection, eye/face protection, hearing protection, respiratory protection, hand protection, body protection, foot protection, as well as guidance o
0 views • 35 slides
Rethinking Conditionalities in Social Protection Programs
The images and descriptions provided delve into the concept of conditionalities within social protection programs, highlighting how they can mask poor service quality, create opportunities for coercion, and strip away the protection and safety nets meant to support individuals. The narrative advocat
0 views • 8 slides
Taming Adaptivity in YOSO Protocols: The Modular Way
Explore the concept of taming adaptivity in YOSO protocols through a modular approach. The research delves into the efficiency, adversary adaptivity, role assignments, and compiler models in synchronous YOSO protocols. The visual presentations illustrate the framework, challenges, and strategies in
0 views • 19 slides
Dual System Encryption: Concept, History, and Recent Works
Explore the concept and history of dual system encryption, including the strategy of security proof, partitioning technique, and the adaptive security model. Understand how security is ensured through mathematical problem complexities and adversary challenges.
0 views • 29 slides
Location Privacy Protection Strategies: A Comprehensive Overview
This study delves into optimal strategies to safeguard location privacy against localization attacks in the realm of location-based services. Discussing the shortcomings of anonymization and obfuscation as standalone defenses, it explores the challenges and pitfalls in designing effective protection
0 views • 26 slides
IEEE 802.11-17/1373r1 PHY Security Overview
This document outlines the security requirements for the IEEE 802.11-17/1373r1 protocol, focusing on authentication, encryption algorithms, key management, and message integrity in both associated and unassociated states. It also addresses securing against adversaries with specified response times,
0 views • 10 slides
Analysis of Onion Routing Security and Adversary-based Metrics
In this comprehensive analysis, the security aspects of Onion Routing are scrutinized along with adversary-based metrics. Various security vulnerabilities such as compromised relays and potential attacks on the first and last routers are examined. Existing metrics like entropy coefficients and proba
0 views • 21 slides
Quantum Query Complexity Measures for Symmetric Functions
Explore the relationships between query complexity measures, including quantum query complexity, adversary bounds, and spectral sensitivity, in the context of symmetric functions. Analysis includes sensitivity graphs, the quantum query model, and approximate counting methods. Results cover spectral
0 views • 19 slides
Introduction to Cryptography: The Science of Secure Communication
Cryptography is the study of methods for sending and receiving secret messages securely. This lecture explores the application of number theory in computer science, focusing on the design of cryptosystems like public key cryptography and the RSA cryptosystem. The goal of cryptography is to ensure th
0 views • 53 slides
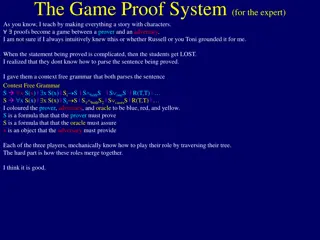
Game Proof System for Experts: Interactive Storytelling Approach
Teaching proofs as a game between a prover, an adversary, and an oracle using context-free grammar and character roles. This system helps students understand complex statements by breaking them down and providing interactive gameplay for better comprehension and engagement.
0 views • 14 slides
Adversarial Risk Analysis for Urban Security
Adversarial Risk Analysis for Urban Security is a framework aimed at managing risks from the actions of intelligent adversaries in urban security scenarios. The framework employs a Defend-Attack-Defend model where two intelligent players, a Defender and an Attacker, engage in sequential moves, with
1 views • 26 slides
Location Privacy Protection using Physical Layer Cooperation
The research presents PhantomPhantom, a system for protecting location privacy by leveraging physical layer cooperation. It explores the challenges of adversary localization systems and proposes solutions such as transmission power and frequency variations. The concept of creating ghost locations an
1 views • 13 slides
Understanding Spiritual Authority and Defeating the Devil
Explore the power of spiritual authority through five dimensions, including redemptive, inherited, positional, delegated, and empowered authority. Discover how to resist the adversary, the devil, who seeks to devour and attack through personal assaults and circumstances. Gain insights from passages
0 views • 23 slides
The Legendary Adventures of Beowulf
Beowulf is a courageous warrior who battles three formidable monsters - Grendel, Grendel's Mother, and a Dragon. He defeats each adversary with valor and strength, showcasing his prowess as a warrior and leader. As king of the Geats, Beowulf's heroic deeds and ultimate sacrifice inspire loyalty and
2 views • 11 slides
Boundary and Fence Patrolling in Robotics Research
Research by Jurek Czyzowicz and team focuses on patrolling boundaries with unreliable robots to prevent intrusions. They investigate agent deployment strategies to protect terrains efficiently. The study explores optimizing visit frequencies to environmental points and coordination methods for multi
0 views • 17 slides
The Importance of Social Protection and the African Union in Africa
Social protection is recognized as a fundamental human right, and efforts within the African Union have been made to promote social protection programs to combat poverty in Africa. The growth of social protection initiatives since the Ouagadougou declaration of 2004 has led to increased awareness an
0 views • 12 slides
Importance of Fall Protection Systems in Workplace Safety
Fall protection systems play a crucial role in preventing injuries and fatalities caused by falls at the workplace. Understanding the anatomy of a fall, statistics on fall-related incidents, and the various philosophies of fall protection can help companies plan and implement effective fall protecti
0 views • 50 slides
Approximation Algorithms for Stochastic Optimization: An Overview
This piece discusses approximation algorithms for stochastic optimization problems, focusing on modeling uncertainty in inputs, adapting to stochastic predictions, and exploring different optimization themes. It covers topics such as weakening the adversary in online stochastic optimization, two-sta
0 views • 33 slides
PSync: A Partially Synchronous Language for Fault-tolerant Distributed Algorithms
PSync is a language designed by Cezara Drăgoi, Thomas A. Henzinger, and Damien Zufferey to simplify the implementation and reasoning of fault-tolerant distributed algorithms. It introduces a DSL with key elements like communication-closed rounds, an adversary environment model, and efficient runtim
0 views • 22 slides
Improving Consumer Protection in Ghana: Insights from the Sixth Annual African Dialogue Consumer Protection Conference
The Sixth Annual African Dialogue Consumer Protection Conference held in Lilongwe, Malawi in September 2014 shed light on the challenges faced by Ghana's consumer protection policies. Irene Aborchie-Nyahe, a legal consultant, highlighted the gaps in Ghana's legislative framework, lack of effective i
0 views • 14 slides
Top Ten Construction Violations FY 2018 Overview
The top ten violations in construction for fiscal year 2018 are related to fall protection, scaffolding, ladders, safety training, eye and face protection, general safety provisions, head protection, aerial lifts, hazard communication, and fall protection systems criteria and practices. The violatio
0 views • 11 slides
Understanding Carnegie Mellon's Protection and Security Concepts
Carnegie Mellon University emphasizes the importance of protection and security in operating systems. Protection involves preventing unauthorized access by users, while security focuses on external threats and authenticating system users. The goals of protection include preventing access violations
0 views • 37 slides
Understanding the Operations of the Devil: A Biblical Perspective
The devil, known as Satan, is a key figure in the Bible with references in both the Old and New Testaments. This overview delves into his existence, personality, names, and deceptive nature, highlighting his role as the adversary of Christians. Believers and unbelievers face different challenges in
0 views • 38 slides
Jesus Overcomes Temptation in the Wilderness According to Luke 4:1-13
Jesus, filled with the Holy Spirit, faced temptation from the devil in the wilderness for forty days. The devil tried to lure Jesus with worldly power and possessions, but Jesus remained steadfast, quoting scripture and emphasizing the worship of the Lord. After enduring all temptations, Jesus emerg
0 views • 19 slides
Understanding Data Protection Regulations and Definitions
Learn about the roles of Data Protection Officers (DPOs), the Data Protection Act (DPA) of 2004, key elements of the act, definitions of personal data, examples of personal data categories, and sensitive personal data classifications. Explore how the DPO enforces privacy rights and safeguards person
0 views • 33 slides
Understanding Political Parties and Factional Politics
Political parties are groups with shared values aiming to win power through elections. They produce manifestos outlining their policies. Factions within parties may support different leaders or policies, influencing party dynamics. Parties play essential roles in shaping government policies and enga
0 views • 24 slides
Enhancing Nuclear Security Through Creative Vulnerability Assessment
Creative and effective vulnerability assessment and testing are essential in nuclear security to identify weaknesses and improve defense systems against intelligent adversaries. The need for in-depth assessment and realistic testing is emphasized to uncover vulnerabilities that adversaries may explo
0 views • 8 slides
The Challenges of Protecting Privacy with Differential Privacy
The article discusses the motivation behind using differential privacy to protect sensitive data while enabling useful queries. It highlights the promise of differential privacy, challenges faced, attacks on existing systems like PINQ and Airavat, and introduces a defense system called The Fuzz. The
0 views • 24 slides
Workshop on Data Protection: Mauritius Police Force Presentation
The workshop on data protection by Mrs. D. Madhub, Data Protection Commissioner, held on May 15, 2019, focused on the Data Protection Act, the Data Protection Office, definitions, functions, powers, and obligations related to data protection, covering areas such as processing of personal data and ri
0 views • 46 slides