Understanding Binary Codes and Character Coding Techniques
Binary codes, such as ASCII and EBCDIC, are crucial in representing data in computers and digital systems. They play a key role in error detection and data encoding. This article discusses the basics of binary coding, various types of binary codes, character coding techniques like ASCII and EBCDIC, and the importance of unique codes for proper encoding and decoding. Explore the world of binary coding and its applications in securing communication and reducing errors in digital communication.
Download Presentation

Please find below an Image/Link to download the presentation.
The content on the website is provided AS IS for your information and personal use only. It may not be sold, licensed, or shared on other websites without obtaining consent from the author. Download presentation by click this link. If you encounter any issues during the download, it is possible that the publisher has removed the file from their server.
E N D
Presentation Transcript
Binary Codes By Mrs. Adline Rajasenah Merryton
Outline Introduction. Character coding. Error detection codes. Gray code. Decimal coding. The Hashemite University 2
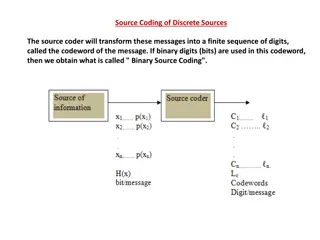
Introduction Binary code is a sequence of 1 and 0 to represent specific values or quantities. Simply it is a substitution or a simplification technique. Binary code objectives: Security assurance: encryption and decryption techniques used to secure communication and data storage. Civil applications: such as text coding in computers, and codes used to reduce digital communication errors opportunities. Mainly we are interested in civil applications. The Hashemite University 3
General Rules of Binary Codes For n-bit binary code, the number of values that can be codes (or simply the max number of codes) = 2n. The min number of bits required to code m values = ciel[log10m/log102]. The max number of bit used to code m values can be >= min limit computed using the above equation (i.e. there is no restrictions on the maximum limit of the used bits). Each value must be assigned a unique code and vice versa to enable correct encoding and decoding. The Hashemite University 4
Binary Codes Types Character coding. Error detection codes. Gray code. Decimal coding. The Hashemite University 5
Character Coding -- ASCII ASCII stands for American Standard Code for Information Interchange . It is a 7-bit code. So, each character is assigned a 7- bit binary value. This value is used by the digital systems (e.g. Computers) to correctly store and manipulate text data. Originally used on non IBM systems. Basis of most currently used digital systems. Need to add an additional bit to make the code 8-bit to be stored in a byte. Two options are provided: Simply add 0 in the MSB. Use it in even or odd-parity error detection coding as will be seen later. The Hashemite University 6
ASCII Table The Hashemite University 7
Character Coding -- EBCDIC EBCDIC stands for Extended Binary Coded Decimal Interchange Code . 8-bit code. Originally used in IBM mainframes. Provide a larger set of codes than ASCII. Less common than ASCII. The Hashemite University 8
Character Coding -- Unicode Designated as the universal code for text coding. Comes to provide a large set of codes, i.e. solve the limitations found in ASCII and EBCDIC. 16-bit code. Used in the Internet. The Hashemite University 9
Error Detection Codes I Data communication requires special codes and algorithms to determine whether the received data is the same as the one transmitted, i.e. error free. The simplest error detection code is based on adding a parity bit for ASCII code. Parity means that two things are equal (identical). Simply add a 1 or 0 to the MSB in ASCII (parity) to make the number of ones in that byte either odd (odd parity) or even (even parity). Even parity is most common. E.g.: for 0111100 add 0 to MSB to obtain an even parity and 1 to obtain an odd parity. The Hashemite University 10
Error Detection Codes II The sender and the receiver know in advance the used parity type (odd or even). The sender add the parity bit to each byte before transmission. The receiver checks the parity before decoding the data. Assume that even parity is used, if the number of ones in a byte found to be odd, this means that there is an error in this byte. The Hashemite University 11
Error Detection Codes III Disadvantages: Both even and odd parity can detect odd number of error bits only. So, if two bits are in error for example, the parity remains correct. Parity cannot determine the locations of the bits in error. Cannot determine the number of bits in error. What to do when detecting an error in the received message? Ask the sender to retransmit the message. Or use an error correction algorithm to recover the original message. The Hashemite University 12
Gray Code Also, known as The Reflected Binary Code . The main idea of Gray code is that any two subsequent codes differ in one bit only. Useful for error detection and correction in digital communication systems. Manly used in applications that produce values in an increasing (or decreasing) order, i.e. similar to the counter concept. Gray code can be 1-bit, 2-bit, 3-bit, etc., based on the number of values needed to be coded. The Hashemite University 13
3-bit Gray Code Decimal 0 1 2 3 4 5 6 7 Binary 000 001 010 011 100 101 110 111 Gray Code 000 001 011 010 110 111 101 100 The Hashemite University 14
Gray Code Conversion I The first method includes conversion in one direction only (from binary value to Gray). Start from the LSB, if the next bit (in the higher significance location) is 1 invert the current bit. If it is 0 then do not change the current bit. E.g. convert 11011 to Gray code. 11011 1 Answer = 10110 0 1 1 0 Remains the same since the bit after it is 0 Inverted (1 0) since the bit after it is 1 The Hashemite University 15
Gray Code Conversion II The second method includes conversion in two directions and it is based on the usage of the XOR logical function. Convert Binary to Gray as follows: Copy the most significant bit For each smaller i do G[i] = XOR(B[i+1], B[i]) (to convert binary to Gray) The Hashemite University 16
Gray Code Conversion III Convert Gray to Binary as follows: Copy the most significant bit B[i] = XOR(B[i+1], G[i]) (to convert Gray to binary) The Hashemite University 17
Decimal Coding I BCD is the main example of decimal coding. BCD Code (Binary Coded Decimal): A code used to represent each decimal digit of a number by a 4-Bit Binary Value. Valid Digits for 0-9 are (0000 to 1001) the binary codes 1010 to 1111 are invalid. So, the BCD code of each digit is the binary conversion of that decimal digit. BCD comes to provide: A solution for the difficulty of the conversion between binary and decimal. Easier to be understood by humans. The Hashemite University 18
Decimal Coding II Decimal 0 1 2 3 4 5 6 7 8 9 BCD 0000 0001 0010 0011 0100 0101 0110 0111 1000 1001 The Hashemite University 19
Decimal Coding III For a compound number of decimal (multi- digit number) the BCD of that number is simply the substitution of the BCD code of each digit. E.g. 12310 000100100011 (BCD) So, n digit decimal number needs 4*n binary bits to be represented in BCD. Pay attention to number justification when it is in BCD. Also, note that numbers in BCD are decimal not binary numbers. The Hashemite University 20
Decimal Coding IV Note that a BCD digit needs 4 bit to be stored. The smallest storage unit in computer is byte which is larger than what needed by 1 BCD digit. There are two types of BCD code depending on how to store BDC digits in a byte. BCD code types: Packed BCD: a byte can store two BCD digits. So, for example, the number 867810 needs 2 bytes. Unpacked BCD: a byte can store one BCD digit in the lower nibble while the higher nibble contains zeros. So, for example, the number 867810 needs 4 bytes. The Hashemite University 21
Additional Notes This lecture covers the following material from the textbook: Chapter 1: Section 1.7 The Hashemite University 22