Impact of Fact-Checking on Credibility Among Older Adults
Analyzing the impact of fact-checking on news credibility among older adults reveals that age is a key factor in information credibility. Older adults tend to give more credibility to various kinds of information, leading to potential challenges in discerning between true facts and false news. Fact-
5 views • 31 slides
Topic : Distinction between Modern and Traditional Logic.
Logic, as a normative study, focuses on distinguishing correct reasoning from incorrect. Traditional logic, based on Aristotle's work, emphasized syllogistic reasoning, while modern logic, pioneered by figures like Leibnitz and Russell, employs mathematical methods and symbolic logic for a more adva
2 views • 10 slides
COMPUTER ORGANISATION Register Transfer Language
Register Transfer Language is a symbolic notation used to describe the micro-operations transferring data among registers in computer organisation. It signifies the availability of hardware logic circuits to perform specified micro-operations and transfer results between registers. Register Transfer
6 views • 7 slides
Symbolic Execution Tree for a Program
Generate the complete symbolic execution tree for a given program by annotating nodes with path constraints and line numbers, aiding in understanding program execution flow.
0 views • 26 slides
Exploring 'Checking Out Me History' - A Poem Analysis Quiz
Unravel the layers of "Checking Out Me History" through a 10-question quiz delving into themes of identity, historical figures, and the narrator's sentiments towards education and heritage. Discover the hidden messages and insights within this powerful poem.
0 views • 12 slides
Explore the Rich Cultural Heritage of the Haida People
Delve into the fascinating world of the Haida, a Native American group from the Pacific Northwest Coast known for their intricate art, symbolic designs, and rich mythological heritage. Discover how Haida symbols capture important events in their history, explore their unique tattooing traditions, an
0 views • 8 slides
Exploring Symbolic Equations with Deep Learning by Shirley Ho at ACM Learning Event
Join Shirley Ho at the ACM Learning event to delve into the world of symbolic equations with deep learning. Discover insights on leveraging deep learning for symbolic equations and engage in a knowledge-packed session tailored for scientists, programmers, designers, and managers.
0 views • 5 slides
Decoding Symbolic Thinking: Exploring the Power of Symbols in Learning and Perception
Delve into the world of symbolic thinking through the eyes of renowned artist René Magritte and explore how symbols shape our perception and understanding of the world. From dissecting Magritte's iconic painting to unraveling the intricacies of language as a symbolic system, journey through the int
2 views • 15 slides
Overview of Subprograms in Software Development
Subprograms in software development provide a means for abstraction and modularity, with characteristics like single entry points, suspension of calling entities, and return of control upon termination. They encompass procedures and functions, raising design considerations such as parameter passing
4 views • 25 slides
Understanding Symbolic Interactionism in Sociology
Symbolic Interactionism is a school of thought in sociology that focuses on how individuals interact with each other through symbols, shaping social structures. It highlights the role of symbols in defining actions and meanings in social interactions. The concept explores how different socializing e
0 views • 18 slides
Quality Improvement Cycle: Plan, Do, Check, Act (PDCA)
The Quality Improvement Cycle follows the PDCA framework, involving planning, implementing, checking, and acting to continuously enhance processes. It begins with defining customer requirements, implementing processes effectively, checking for issues, and taking action to resolve any problems. The c
1 views • 6 slides
Symbolic Meanings of Twelve Chinese Zodiac Pairs Explained
Explore the symbolic meanings of the twelve Chinese zodiac pairs, highlighting the complementary personalities represented by each pair. From wisdom and diligence to bravery and care, the intricate relationships between these zodiac signs offer valuable insights into Chinese culture and values.
1 views • 8 slides
Understanding Sociological Perspectives
Sociologists employ three primary theoretical perspectives to explain how society influences young people and vice versa: the symbolic interactionist perspective, the functionalist perspective, and the conflict perspective. Symbolic interactionism focuses on symbols and face-to-face interactions, wh
1 views • 18 slides
Runtime Checking of Expressive Heap Assertions
Motivated by the unreliability of large software systems due to concurrency bugs and limitations of static analysis, the goal is to enable runtime analysis of deep semantic properties with low overhead. This involves checking expressive heap assertions at runtime with minimal impact on performance,
0 views • 15 slides
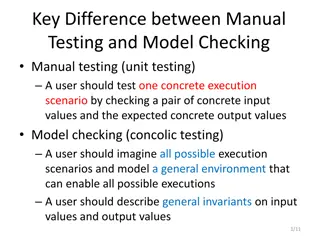
Difference Between Manual Testing and Model Checking
Manual testing focuses on testing specific scenarios with concrete inputs and outputs, while model checking involves imagining all possible scenarios to create a general environment for testing. In manual testing, users test specific execution scenarios, whereas in model checking, users envision and
2 views • 4 slides
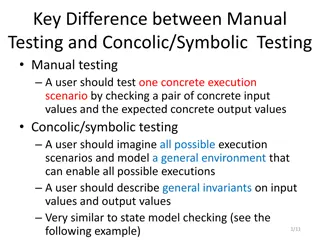
Difference Between Manual Testing and Concolic/Symbolic Testing in Software Development
Manual testing involves checking concrete input and output values for specific execution scenarios, while concolic/symbolic testing requires imagining all possible scenarios and modeling a general environment. General invariants on input and output values are described, similar to state model checki
0 views • 4 slides
Event Log Alignment for Conformance Checking
Approach based on ILP for aligning event logs and process models, ensuring multi-perspective conformance checking. Examples illustrate trace executions with and without problems, utilizing Petri Nets with data. Alignments between log and process traces are analyzed, showing the existence of multiple
0 views • 21 slides
Understanding Symbolic Logic: A Modern Approach
Delve into the world of symbolic logic where traditional and modern approaches differ. Learn how symbolic languages help overcome challenges with natural languages, leading to a clearer understanding of deductive reasoning through the analysis of premises, conclusions, compound statements, and logic
1 views • 32 slides
Understanding Propositional Logic at Kwame Nkrumah University
Dive into the world of symbolic logic and compound statements with a focus on Propositional Logic at Kwame Nkrumah University in Ghana. Explore the concepts of connectives, simple and compound statements, truth values, and more. Enhance your logical reasoning skills through a tutorial on symbolic lo
0 views • 57 slides
Introduction to Symbolic Logic: Understanding Logical Inferences
Logic is the study of reasoning methods to distinguish between correct and incorrect arguments. Symbolic Logic involves representing logic symbolically for easier understanding and manipulation. Logical inferences help in making decisions based on reasoning chains. The content discusses the use of l
1 views • 28 slides
Understanding Algorithms and Combination in Theory
Cover operations, quantifier elimination, and applications like strongest post-condition and procedure summaries are explored in the context of algorithms and their combination, shedding light on symbolic model checking, uninterpreted functions, and more.
0 views • 20 slides
Context-Aware Identification of Check-worthy Claims in Political Discussions
This work explores the intersection of man and machine in countering malicious communication in social networks, focusing on fact-checking in political discussions. The research investigates the need for technology to verify the accuracy of public figures' statements, considering the thriving field
0 views • 21 slides
Ceremonial Possession Practices in Europe's New World Conquest
Patricia Seed's book explores how European nations utilized ceremonial practices to claim ownership of the New World between 1492-1640. Each nation employed symbolic gestures to legitimize their rule, leading to conflicts over territory. Critics such as Las Casas, Van Der Donck, and Williams challen
0 views • 11 slides
Exploring Architecture and Challenges of Proof Assistants
Explore the architecture of proof assistants, discussing the use of tactics, formal proofs, and the difficulty in utilizing these tools. Discover the contribution of a new architecture for proof assistants, addressing extensibility and error checking, with a focus on soundness guarantees. Delve into
0 views • 41 slides
Bounded Satisfiability Checking for Early Legal Compliance Verification
Early verification of legal compliance is crucial to avoid consequences such as violating regulations like GDPR. Through bounded satisfiability checking using Metric First-order Temporal Logic (MFOTL), this research focuses on system design verification for regulatory compliance. The study addresses
0 views • 29 slides
Essential Guide to Opening and Managing a Checking Account
Learn the importance of opening a checking account, the process of choosing a bank, criteria to consider, and the steps to open an account. Understand the different services offered by banks and the key factors to keep in mind when selecting a financial institution. Discover the benefits and require
0 views • 39 slides
Exploring the Archetypal Symbolism of the Whale in Moby-Dick
The concept of the whale as an archetype, deeply rooted in human consciousness, is examined through the lens of Moby-Dick. The symbolic significance of the whale, drawing on mythology and literature, captures universal themes of fear, awe, and nature's power. Delving into the literary analysis of Mo
0 views • 4 slides
Differential Assertion Checking and Relative Correctness in Software Verification
Differential assertion checking compares two similar programs to identify errors, while relative correctness ensures all assertions pass, highlighting failed assertions. The content discusses the challenges and benefits of these techniques in software verification, with examples of correct and buggy
0 views • 17 slides
Divide & Conquer Approach to Model Checking
Addressing the state space explosion issue in model checking, this work by Canh Minh Do, Yati Phyo, and Kazuhiro Ogata introduces a divide & conquer approach focusing on until and until stable properties. The research extends techniques to handle these properties effectively, emphasizing mitigation
2 views • 17 slides
Understanding the Decision-Making Process of Checking Behaviors Among Doctors and Patients
Recent research by Ido Erev from Technion and University of Warwick, along with Alvin E. Roth and others, explores the coexistence of insufficient and over-checking behaviors among individuals, including doctors and patients. The study delves into the factors influencing checking decisions, highligh
0 views • 24 slides
Understanding Symbolic Logic and Rules of Inference
Explore the realm of symbolic logic and rules of inference through Modus Ponens, Well Formed Formulas (WFFs), truth tables, and more. Discover how logic is topic-neutral and test arguments for validity using truth tables. Dive into the world of logical equivalence and consistency with practical exam
0 views • 15 slides
Enhancing Online Service Security through Symbolic Transaction Certification
The research discusses securing multiparty online services through the certification of symbolic transactions, addressing logic flaws and the importance of program verification. The Certification of Symbolic Transaction (CST) approach is presented as an effective way to verify system-wide properties
0 views • 22 slides
Symbolic Communication in African Literary Arts: Proverbs and Visual Symbols
Exploring the use of African proverbs and symbols as forms of communication in literature, particularly in Nigeria. The incorporation of Adinkra patterns, Akan symbols, and visual representations of proverbs in fiction writing and cultural traditions is highlighted, showcasing the rich symbolic heri
0 views • 13 slides
Understanding Culture: Definition, Components, and Variations
Culture encompasses the entire way of life for a group of people, comprising material and symbolic elements passed down through generations. Categories include material and symbolic culture, with aspects like beliefs, customs, gestures, language, norms, and artifacts shaping cultural identity. Langu
0 views • 15 slides
Exploring Human-Animal Relationships Through Social Science Research: A 25-Year Review
Delve into the intricate world of human-animal interactions with a comprehensive examination of 25 years of social science research. Discover thought-provoking studies that explore the symbolic, cultural, and emotional dynamics shaping our relationships with animals. From the moral universes of cock
0 views • 27 slides
Input Elimination Transformations for Scalable Verification and Trace Reconstruction
This work introduces new input elimination techniques for scalable model checking in industrial applications, focusing on trace reconstruction. The transformations aim to make the netlist more tractable for solving, involving various algorithms such as retiming, phase abstraction, and bitwidth reduc
0 views • 27 slides
Understanding Symbolic Execution and Directed Automated Random Testing
Symbolic Execution is a method used for analyzing programs to determine inputs causing each part to execute, vital in program testing. However, limitations arise in cases without code availability, hindering definitive path conditions. Directed Automated Random Testing (DART) overcomes this through
0 views • 20 slides
Understanding Predicate Logic and Quantifiers for Symbolic Proofs
Dive into the realm of predicate logic and quantifiers, exploring the nuances of symbolic proofs and evaluating logical statements. Learn about bound variables, domain considerations, and strategies for constructing iron-clad proofs using quantifiers.
0 views • 36 slides
Analysis of Device Drivers and Testing: Advancements and Challenges
This presentation explores the critical issues related to device driver bugs leading to OS crashes. It delves into methods like software model checking, testing, and analysis to identify and prevent such bugs. With a focus on Linux device driver architecture, it categorizes common driver bugs and di
2 views • 21 slides
Orthogonal Vectors Conjecture and Sparse Graph Properties Workshop
Exploring the computational complexity of low-polynomial-time problems, this workshop delves into the Orthogonal Vectors Problem and its conjectures. It introduces concepts like the Sparse OV Problem, first-order graph properties, and model checking in graphs. Discussing the hardness of problems rel
2 views • 22 slides