The Digital Personal Data Protection Act 2023
The Digital Personal Data Protection Act of 2023 aims to regulate the processing of digital personal data while balancing individuals' right to data protection and lawful data processing. It covers various aspects such as obligations of data fiduciaries, rights of data principals, and the establishm
3 views • 28 slides
Data Guardianship_ Securing Sensitive Documents
The modern day digital world deals with data breaches and cyber threats, that\u2019s why the importance of secure document management in Los Angeles, cannot be overstated. Whether you\u2019re a small business owner, a healthcare professional, or an individual handling personal information, ensuring
9 views • 6 slides
Data Guardianship_ Securing Sensitive Documents
The modern day digital world deals with data breaches and cyber threats, that\u2019s why the importance of secure document management in Los Angeles, cannot be overstated. Whether you\u2019re a small business owner, a healthcare professional, or an individual handling personal information, ensuring
0 views • 6 slides
Safeguarding Canada's Research: Policy on Sensitive Technology Research and Affiliations of Concern (STRAC)
Canada's new Policy on Sensitive Technology Research and Affiliations of Concern (STRAC) aims to protect the country's research ecosystem from foreign entities posing security risks. The policy restricts funding for projects involving sensitive technology research if affiliated with military or stat
1 views • 10 slides
TSN and Time Sensitive Wireless
This document explores the relationship between IEEE 802.11 and Time Sensitive Networking (TSN), defining TSN in the context of 802.11 and highlighting the importance of TSN for improving packet delivery, reducing latency, and enhancing network reliability. Various features like Multi-AP, preemption
6 views • 18 slides
Mistakes to Avoid When Parenting as a Sensitive Father_
Are you a sensitive father raising a strong-willed child? While it's natural to make mistakes along the way, being aware of common pitfalls can help you navigate parenthood more effectively. Below, we are going to outline some common mistakes to steer clear of when parenting as a sensitive father, d
7 views • 6 slides
How BI Software Tools Secure Sensitive Business Information
Protecting sensitive business information is more important than ever. BI software tools play a crucial role in securing data through advanced security features such as data encryption, user access controls, real-time monitoring, audit trails, and data anonymization. These tools not only safeguard f
1 views • 6 slides
Understanding VA Privacy Issues and Sensitive Information
Explore the complex landscape of VA privacy issues, including data relationships, sensitive personal information (SPI), personally identifiable information (PII), individually identifiable information (III), and individually identifiable health information (IIHI). Learn about the roles and responsib
0 views • 29 slides
Examination of Personal Information Protection in Victorian Universities
The report discusses the importance of protecting personal information in Victorian universities due to the high volumes of sensitive data they hold. It emphasizes the responsibility to safeguard personal information through a risk-based approach, as outlined in the Privacy and Data Protection Act 2
0 views • 17 slides
Examination of Data Protection in Victorian Universities
Report explores the need for robust data protection in Victorian universities due to high volumes of personal and sensitive information held. It highlights the responsibility to safeguard personal data, emphasizing a risk-based approach for security. The examination by OVIC focused on privacy and se
0 views • 17 slides
Understanding Privacy in Information Security Training
Privacy awareness training is crucial, covering topics such as the definition of privacy, importance of privacy protection, Personally Identifiable Information (PII), and Sensitive PII. Discover why privacy is vital to maintaining public trust, preventing identity theft, and complying with laws. Lea
0 views • 55 slides
Guidance on Subject Access Requests under Data Protection Act 2018 for Social Workers in Children's Services
This guidance provides information on Subject Access Requests (SARs) under the Data Protection Act 2018, specifically tailored for social workers in children's services. It explains what SARs are, how requests can be made, considerations for handling requests related to children and young people, an
4 views • 11 slides
Data Protection Incidents and Fines: Lessons Learned
Learn from real-life data protection scenarios that led to fines and breaches, such as improper data handling with USB devices, confidential files ending up in public recycling, misdirected emails of sensitive data, and unsecured mobile devices leading to theft. Understand the consequences and best
0 views • 9 slides
Understanding the EU General Data Protection Regulation (EU GDPR)
The EU General Data Protection Regulation (EU GDPR) is a comprehensive regulation that governs the processing of personal data of individuals in the EU. It came into effect on May 25, 2018, and applies to all organizations handling personal data of EU residents. The regulation includes key definitio
4 views • 21 slides
Overview of Personal Data Protection Bill, 2018
The Personal Data Protection Bill, 2018 addresses concerns regarding personal privacy amidst advancing technology. It grants rights to individuals and mandates transparency in handling personal information. The Bill stems from the recognition of the right to privacy as fundamental. It defines terms
0 views • 23 slides
Personal Data Protection Requirements in the Health Sector: EU Twinning Project Overview
This document provides an overview of the personal data protection requirements in the health sector, specifically focusing on the European Union Twinning Project. It covers topics such as legitimation, principles, implementation, enforcement, code of conduct, and European provisions, including the
0 views • 25 slides
Hide Content from Bots in Shopify
Implement effective content hide content from Bots in Shopify strategies on your store from accessing sensitive information. To protect sensitive data and improve site security, make use of cutting-edge bot identification and blocking strategies. Ass
1 views • 6 slides
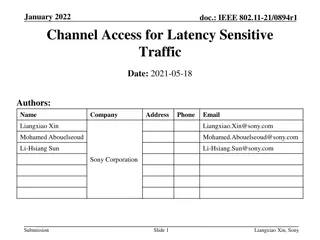
Enhancing Channel Access for Latency-Sensitive Traffic in January 2022
In the documentation IEEE 802.11-21/0894r1, the focus is on improving channel access for latency-sensitive traffic through concepts like Restricted TWT (Target Wake Time). The proposal suggests methods to protect TWT Service Periods from non-TWT scheduled STAs, ensuring prioritized transmission of l
0 views • 11 slides
Exploring Human-Data Interactions in Personal Digital Data Engagements
Delve into the intricate world of human-data interactions in the realm of personal digital data engagements. Investigate how individuals use and perceive their digital data, exploring the intersections of technology, data usage, and human life. Discover the vitality of digital data in shaping our so
0 views • 19 slides
Detecting Sensitive Data Disclosure via Text Analysis
This article discusses techniques for detecting sensitive data disclosure, including taint analysis and bi-directional text correlation analysis. It covers existing detection methods, challenges with generic APIs, and solutions using text correlation analysis to determine data sensitiveness. Example
0 views • 34 slides
Understanding Alabama Data Breach Notification Act for County Governments
Alabama's Data Breach Notification Act requires all county governments and related entities to comply with specific security measures to protect sensitive information of residents. The law mandates prompt investigation and notification in case of a breach, defining what constitutes a breach and sens
1 views • 36 slides
Virginia Department for Aging and Rehabilitative Services Cyber Security Policies
The Virginia Department for Aging and Rehabilitative Services (DARS) mandates cyber security awareness training for individuals with access to sensitive systems, requiring completion upon access grant and annual refreshers. Compliance with Virginia Information Technology Agency policies is essential
0 views • 17 slides
Exploring CTE Data Collections and Security Protocols in Education
Delve into the world of CTE data collections through this informational session hosted by the Oregon Department of Education. Learn about the basics of CTE data submission, resources available to data submitters, and the importance of maintaining data security and privacy. Gain insights into the str
0 views • 26 slides
Gentle Cleanser for Maintaining Healthy and Refreshed Sensitive Skin
Atomy Aidam offers a gentle cleanser that maintains the health and freshness of sensitive skin, leaving you with a revitalizing feeling. The Oriental Herb Complex, developed with natural herbs like chamomile and rosemary, enhances skin immunity and provides a natural aroma that keeps your private ar
0 views • 4 slides
Gender Equality, SDGs, and Small Islands Developing States: Targets and Implementation
Goal 5 of the SDGs focuses on transformative change for gender equality, with key targets addressing discrimination, violence, unpaid care work, and participation in decision-making. Additionally, gender-sensitive targets are integrated into other SDG goals, recognizing the gender dimension in areas
0 views • 10 slides
Climate-Sensitive Tree Growth Modeling in Sierra Nevada Ecoregion
This project focuses on climate-sensitive individual tree growth models for the Sierra Nevada Ecoregion, aiming to provide accurate projections for forest adaptation and mitigation research. Collaborators and researchers utilize a sophisticated model structure to evaluate the impact of climate chang
0 views • 19 slides
Understanding Trauma-Sensitive Discipline Policies in Schools
Explore the concept of trauma-sensitive discipline policies in schools within the framework of VTSS TFI 1.6. Gain insights into changes in the Model Code of Conduct, identify vulnerable decision points, and incorporate trauma-sensitive approaches to respond to challenging behaviors. Embrace proactiv
0 views • 34 slides
Best Practices for Protecting Sensitive Data
Learn about password and credit card data security, storing passwords securely, data in transit vs. data at rest, and the importance of using salts to protect password hashes from offline attacks. Discover how to securely store passwords using encryption, hashing, and more to minimize exposure of se
0 views • 30 slides
Building a Secure Access & SQL Server Solution with Anders Ebro
Anders Ebro, a Principal consultant with Exacto A/S, shares insights on building a secure access and SQL server solution. With a background in SQL development and experience in managing sensitive data, Anders emphasizes the importance of security aspects such as limiting access to sensitive data, ro
0 views • 20 slides
Understanding the Risks of Sensitive Sectors in Free Trade Agreements
Explore the intricacies of sensitive sectors in Free Trade Agreements (FTAs) through an in-depth analysis of the potential dangers and benefits. Delve into the complexities of preferential tariff cuts, trade creation versus diversion, rules of origin, and the exemption of sensitive sectors. Learn ho
0 views • 27 slides
Regulation of Non-Personal Data and Its Scope
The discussion delves into the expanding scope of legal instruments surrounding personal data regulation, including the definitions and implications of identifiable natural persons, processing of personal data, and metadata. It explores the necessity of regulating non-personal data alongside persona
0 views • 9 slides
Understanding Data Protection Regulations and Definitions
Learn about the roles of Data Protection Officers (DPOs), the Data Protection Act (DPA) of 2004, key elements of the act, definitions of personal data, examples of personal data categories, and sensitive personal data classifications. Explore how the DPO enforces privacy rights and safeguards person
0 views • 33 slides
Exploring Regulatory Challenges and Opportunities in Big Data Applications
Discussing the regulatory perspective on commercial versus humanitarian and development applications of big data, this conversation with regulators highlights the differences and similarities in utilizing data for various sectors. Emphasizing the importance of trust, confidentiality, and data securi
1 views • 17 slides
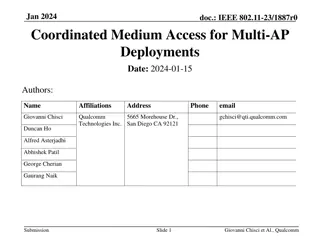
Coordinated Medium Access for Multi-AP Deployments in IEEE 802.11 Networks
The document discusses a solution to reduce latency, increase throughput, and improve reliability in networks with latency-sensitive traffic by introducing coordination between access points (APs). This involves leveraging mechanisms like Restricted TWT (rTWT) and Coordinated rTWT (C-rTWT) to facili
0 views • 12 slides
Understanding Sketching and Locality Sensitive Hashing in Data Mining
Explore the concepts of Jaccard Similarity and Cosine Similarity in data mining, along with their applications in recommendation systems and finding near-duplicates. Discover how Sketching and Locality Sensitive Hashing techniques help in efficiently identifying similar items and solving the Nearest
0 views • 63 slides
The Water Sensitive City Theory: Climate Change Adaptation Approach
The Water Sensitive City Theory explores how cities can evolve into integrated, adaptive, and climate-resilient water systems. It emphasizes restoring natural water balance, providing ecosystem services, and fostering water-sensitive communities. This approach is crucial for climate change adaptatio
0 views • 16 slides
Hide Content from Bots in Shopify
Implement effective content hide content from Bots in Shopify strategies on your store from accessing sensitive information. To protect sensitive data and improve site security, make use of cutting-edge bot identification and blocking strategies. Ass
0 views • 6 slides
My Personal Spacer – Live the Difference with Your Personal Space
Introducing My Personal Spacer, a unique invention designed to provide individuals with their personal space in a crowded world where diseases are prevalent. This innovative device enables users to maintain a comfortable distance from others without having to verbally express it. With the slogan "I
0 views • 9 slides
Managing Sensitive Data in Cloud Infrastructures: Best Practices and Considerations
Explore the orchestration of cloud infrastructures for handling sensitive data, including the importance of context, legal considerations, and utilizing self-assessment tools like CAIQ. Learn about QDR's current infrastructure at Syracuse University and the challenges of storing sensitive data in th
0 views • 10 slides
Trust-Based Data Governance Models and Their Impact on Personal Data Regulation
This article delves into trust-based data governance models, contrasting them with control-based models in the context of personal data regulation. It explores the challenges and benefits associated with both approaches, emphasizing the emergence of new models centered on trust such as data stewards
0 views • 11 slides