How to Protect Your On-Demand App from Cyberattacks and Data Breaches
On-demand app development solutions provide convenient services but also carry cybersecurity risks like hacking, malware, and data breaches. This comprehensive guide explores best practices to secure on-demand apps and protect sensitive user data. Learn how encryption, multifactor authentication, ac
0 views • 4 slides
Airport Security Market to be Worth $25.27 Billion by 2031
\u00ae, the airport security market is projected to reach $25.27 billion by 2031, at a CAGR of 8.6% from 2024 to 2031. Some of the major factors driving the growth of this market are stringent government regulations for airport security and the growing number of air passengers. In addition, increasi
8 views • 5 slides
KEERTHI SECURITY - Best Security Agencies In Bangalore
Keerthi Security is a security and facility management services provider in Bangalore. We are committed to offering top-notch security services for commercial and residential places. We aim to offer very secure and reliable security services to everyone. Our best-trained security guards are very sha
10 views • 11 slides
Malicious Attacks, Threats, and Vulnerabilities in IT Security
Malicious attacks, threats, and vulnerabilities in IT systems pose significant risks and damages. This chapter explores the types of attacks, tools used, security breaches, and measures to protect against cyber threats. Learn how security professionals safeguard organizations from malicious attacks
0 views • 24 slides
Sens Security Your Premier Personal Security Firm
In a world where personal safety cannot be taken for granted, Sens Security stands out as Melbourne's leading personal security firm. Our services are designed for those who demand the utmost in protection, whether you're a high-profile personality, a top executive, or an individual with unique secu
1 views • 6 slides
Sens Security Your Premier Personal Security Firm
In a world where personal safety cannot be taken for granted, Sens Security stands out as Melbourne's leading personal security firm. Our services are designed for those who demand the utmost in protection, whether you're a high-profile personality, a top executive, or an individual with unique secu
1 views • 6 slides
Sens Security Your Premier Personal Security Firm
In a world where personal safety cannot be taken for granted, Sens Security stands out as Melbourne's leading personal security firm. Our services are designed for those who demand the utmost in protection, whether you're a high-profile personality, a top executive, or an individual with unique secu
1 views • 6 slides
Role of Security Champions in Organizations
Security Champions play a vital role in decision-making concerning security engagement, acting as a core element in security assurance processes within a team. They foster a security culture, reduce dependency on the CISO, and promote responsible autonomy and continuous security education in the org
3 views • 13 slides
Privacy Breach Management Guide by Health PEI
Understanding, Preventing, and Managing Privacy Breaches in Healthcare: Learn about what constitutes a privacy breach, how to prevent breaches, steps to determine and manage breaches effectively, including containment, investigation, and notification processes.
0 views • 10 slides
Cyber Data Breach Review_ A Comprehensive Insight with LDM Global in the USA
In today's digital landscape, cyber data breaches pose significant threats to organizations of all sizes. A cyber data breach can result in severe financial losses, reputational damage, and legal ramifications. To navigate these challenges effectively, companies turn to expert services like those pr
2 views • 13 slides
Enhance Your Protection with MDR Cyber Security Services in Dallas
Do you wish to improve your security in Dallas against cyber threats? This is exactly where MDR Cyber Security services from Blackswan Cybersecurity can come in handy. While more complex forms of cyber threats and data breaches are becoming more popular, corporations need to acquire modern security
4 views • 8 slides
Roles of a Security Partner
Learn about the roles and responsibilities of a Security Partner, including requesting changes to security roles, approving security requests, and initiating access requests. Explore the overview of Workday Security, the security access request process, and the pre-request process flow. Discover how
2 views • 17 slides
Lessons from Recent Data Breaches: Insights and Strategies
This presentation covers the landscape of data breaches, leading causes, and steps to take when facing a cyber incident. It discusses the impact of large-scale cyber attacks by external threat actors, outlines key considerations for response, and provides tips for notifying affected individuals to m
2 views • 20 slides
Ransomware and Data Breaches in Public Libraries Analysis
Delve into the world of ransomware and data breaches in public libraries, exploring the definitions of ransomware and data breaches, the potential impacts on libraries, the financial losses incurred, and the value of library records. Understand the risks, implications, and consequences associated wi
0 views • 21 slides
Enhancing University Information and Records Management for Strategic Advancement
The University's continuous improvement strategy for 2020 focuses on managing information and records effectively to mitigate risks associated with data processing. Information is deemed a critical asset, and risks range from data breaches to operational disruptions. To address these challenges, an
1 views • 21 slides
Cybersecurity Challenges: Attacks on Web Applications and Cost of Security Breaches
In the realm of cybersecurity, attacks on web applications pose a significant threat with 78% of attacks targeting applications. The consequences of these attacks are immense, with projected costs reaching $6 trillion annually by 2021. Notable breaches in recent years highlight the urgency for robus
8 views • 23 slides
Special Audit Report on Caribbean Maritime University (CMU) - December 2019
The special audit report on Caribbean Maritime University revealed unsatisfactory HR practices, poor governance, deficiencies in oversight, procurement breaches, and mismanagement of contracts. Issues included inconsistent HR practices, unapproved emoluments, infrequent council meetings, and inadequ
0 views • 12 slides
Ensuring Digital Security Governance in the Modern Business Landscape
In today's digital landscape, companies and board directors must actively establish good controls to safeguard sensitive information crucial for sustained business operations. This involves understanding risks, enforcing robust security measures, and staying abreast of evolving threats. Failure to p
0 views • 12 slides
Information Security Basics
Information security involves protecting information and systems from unauthorized access, use, disclosure, disruption, modification, or destruction. This includes safeguarding assets from various threats such as hackers, malware, natural disasters, and human errors. The chapter covers topics like u
0 views • 27 slides
Response Patterns to Data Breaches in Firm IT Investment
This research explores how firms reallocate internal IT resources in response to security breaches and the impact of these allocation patterns on future firm performance. It delves into the allocation of IT budgets, changes in IT staffing, and examines antecedents and consequences of security breach
0 views • 47 slides
Essential Steps for Personal Data Breach Management
Detect, identify, and respond effectively to personal data breaches by containing the breach, assessing risks, notifying relevant authorities and affected individuals, and implementing measures to prevent future occurrences. Debunk common myths surrounding breach reporting and focus on mitigating ne
0 views • 5 slides
Louisiana Coastal Flooding Litigation Overview
The content discusses various aspects related to the Katrina Canal breaches consolidated litigation in Louisiana, focusing on the legal implications, failures in flood control measures, geology of coastal Louisiana, coastal elevations, and the impact of canal breaches on flooding in the region. It a
1 views • 30 slides
Privacy Breach Response and Reporting under the Health Information Act
Understanding privacy breaches under the Health Information Act (HIA) is crucial for organizations dealing with health data. This document outlines what constitutes a breach, mandatory notification requirements, factors to consider in determining risk of harm, and potential offences and penalties fo
0 views • 21 slides
Importance of Privacy & Data Security Training in Healthcare
Privacy and data security training in healthcare is crucial due to the interconnected nature of the industry, putting patient information at risk. Breaches have resulted in significant financial losses, emphasizing the need for mandatory training to safeguard patient privacy. Understanding responsib
0 views • 27 slides
HIPAA and Research Data Security Training for Researchers at BU Charles River Campus
This training provides essential information on how HIPAA impacts human subject research, the importance of protecting health data, reporting breaches, and utilizing BU resources. It also covers implications of HIPAA in research, national standards, consequences of breaches, and scenarios where HIPA
0 views • 37 slides
Security Threats and Countermeasures
Explore the diverse threats posed by attackers in the information security landscape, ranging from employee sabotage to hacking incidents. Learn about fundamental security terminology, types of security compromises, and countermeasure strategies to prevent, detect, and correct security breaches. Gai
0 views • 32 slides
NHS Sussex Conflicts of Interest Breach Register Summary May 2024
NHS Sussex manages conflicts of interest breaches by recording and publishing them on their website. Breaches are documented with details of the nature of the breach and actions taken. In May 2024, no breaches were reported. Previous months had breaches due to late declarations of interest. Staff we
0 views • 5 slides
Practical Computer Security Course Overview
Explore the crucial aspects of practical computer security in this comprehensive course led by Dr. Mark Ciampa from Western Kentucky University. From analyzing security vulnerabilities to understanding cyber threats and safeguarding your digital assets, this course equips you with essential knowledg
0 views • 114 slides
Comprehensive Course Review: Security Research Cornerstones at Carnegie Mellon University
Dive into the essential topics of software security, network security, OS security, and cryptography in the course offered by Vyas Sekar at Carnegie Mellon University. Explore control flow hijacks, cryptography terminology, and the importance of network security in protecting data transmissions. Lea
1 views • 41 slides
UIC Security Division Overview and International Activities
The UIC Security Division plays a crucial role in supporting the security platform of the International Union of Railways (UIC). Headed by Jacques Colliard, the division is based in Paris and consists of key personnel like Marie-Hélène Bonneau, Jos Pires, and Laetitia Granger. The division's activ
0 views • 12 slides
Automating Security Operations Using Phantom
Isabella Minca, an intern for 4 months in the Security Team at Adobe, presents an overview of automating security operations using Phantom. The presentation covers goals, security alerts, Phantom playbooks, handling security data, and the capabilities of Phantom in orchestrating security responses.
0 views • 28 slides
Importance of Security in Web Development
Our perception of security has evolved to acknowledge the presence of malicious actors and potential vulnerabilities in web applications. To write secure code, developers must assume the worst-case scenario and adopt a security mindset that trusts no one. Attackers have various goals, such as steali
0 views • 18 slides
VAST: A Unified Platform for Interactive Network Forensics
VAST is a comprehensive platform designed for interactive network forensics, addressing the increasing frequency of security incidents and large-scale data breaches. It aims to provide solutions for detecting, analyzing, and preventing breaches efficiently, with features like data exploration, query
0 views • 17 slides
Data Breaches and Privacy Concerns: An Overview
Privacy expert Marilyn Prosch, Ph.D., sheds light on the significant issue of privacy, emphasizing recent data breaches in various institutions and outlining some alarming cases where sensitive information was compromised. The incidents range from stolen laptops and office break-ins to mishandling o
0 views • 34 slides
Cyber Security: Trends, Challenges, and Solutions
Cyber security is vital for safeguarding digital assets from threats like data breaches, malware, and emerging technologies. This article explores the elements of cyber security, its applications, current challenges, and methods to combat them. The comparison of AES and DES encryption algorithms hig
1 views • 11 slides
Comprehensive DevOps Security Training Overview
This Certified DevOps Security Practitioner course provides a deep dive into implementing DevSecOps, integrating security into the DevOps processes. Covering topics like security testing, Docker security, automation, and more, the training aims to equip participants with the necessary skills to embe
1 views • 5 slides
Importance of Physical Security in the Workplace
Learn why physical security is crucial for safeguarding people and property, preventing unauthorized access, and enhancing overall safety in the workplace. Explore key components, basic measures, and ways to secure assets through passwords, locks, barriers, and surveillance. Understand the significa
0 views • 32 slides
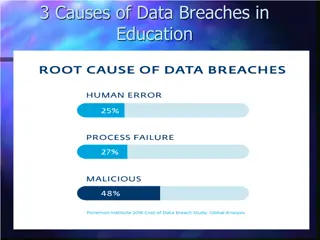
Data Breach Causes in Education
Data breaches in education are often caused by human errors, process failures, and malicious breaches. Human errors include leaving computers unlocked, sharing passwords, and carelessly discarding sensitive information. Process failures involve not keeping software up-to-date, lack of security polic
0 views • 15 slides
Legal Issues in Data Breaches and Confidentiality Violations
The content covers various scenarios related to breach of confidence, liability of businesses in safeguarding data, and legal causes of action in case of data breaches. It discusses real-life analogies and legal principles concerning the mishandling of confidential information, including a case stud
1 views • 23 slides
Comprehensive Integrated Security Solution Overview by Microsoft
Ponemon Institute's Cost of Data Breach Study reveals the significant financial impacts of data breaches. Microsoft offers an intelligent, unified enterprise defense solution through Microsoft Threat Protection, Azure Security Center, and Azure Sentinel. This comprehensive array of integrated securi
0 views • 6 slides