Automated Mobile App QoE Diagnosis with Cross-layer Analysis
This work presents the QoE Doctor, a solution for accurate and repeatable QoE measurements and analysis in mobile apps. By introducing UI automation, it enables the replay of user behavior to measure UI layer QoE metrics without modifying app source code. The QoE Doctor also supports multi-layer dia
3 views • 28 slides
Layer 2 Token Marketing Services
Layer-2 token marketing promotes tokens built on scalable layer-2 solutions, highlighting benefits like faster transactions and lower fees. Get connected with our experts today and launch a lucrative \ntoken platform.
0 views • 3 slides
Understanding Ozone Depletion: Causes and Impact
The ozone layer, found in the stratosphere at 15 to 40 km altitude, plays a crucial role in absorbing harmful ultraviolet radiation. However, due to the use of Chlorofluorocarbons (CFCs), the ozone layer has been depleted, leading to the formation of the ozone hole. This depletion is caused by chemi
0 views • 27 slides
Understanding Multi-Layer Perceptrons in Neural Networks
In this lecture by Dr. Erwin Sitompul at President University, the focus is on Multi-Layer Perceptrons (MLP) in neural networks, discussing their architecture, design considerations, advantages, learning algorithms, and training process. MLPs with hidden layers and sigmoid activation functions enabl
2 views • 17 slides
NASA Platform Layer Updates for the CAELUM (7.0) Release
The National Aeronautics and Space Administration (NASA) discusses platform layer updates for the CAELUM (7.0) release of the Core Flight System in the 2021 Flight Software Workshop. The platform layer consists of the Operating System Abstraction Layer (OSAL) and Platform Support Package (PSP), whic
1 views • 20 slides
Introduction to Socket Programming for Client/Server Applications
Gain insights into socket programming for building client/server applications that communicate using the Socket API. Explore the fundamentals of TCP sockets, application layers, terminology, and client/server socket interactions. Understand how sockets serve as doors between application processes an
3 views • 15 slides
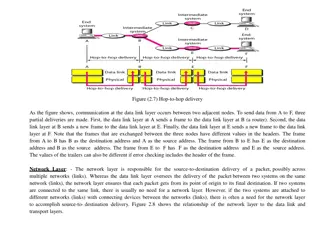
Understanding Communication Layers in Computer Networks
Communication in computer networks is facilitated through different layers such as the data link, network, and transport layers. Each layer has specific responsibilities in ensuring data delivery from one point to another. The data link layer handles communication between adjacent nodes, the network
3 views • 7 slides
Understanding Boundary Layer and Drag Forces in Fluid Dynamics
Boundary layer module explains the presence of viscous forces near a surface due to fluid flow, leading to laminar or turbulent boundary layers. Flow separation occurs when a boundary layer detaches from a surface, impacting lift and drag forces. Adverse pressure gradients and flow separation phenom
0 views • 19 slides
Understanding Paper and Thin Layer Chromatography (TLC) in Biochemistry
Chromatography techniques are used in laboratories to separate and identify components of mixtures. Paper chromatography is a type where a developing solution travels up a filter paper, separating compounds based on their affinity to the stationary phase. Thin Layer Chromatography (TLC) is a similar
0 views • 22 slides
Understanding the OSI Model and Layered Tasks in Networking
The content highlights the OSI model and layered tasks in networking, explaining the functions of each layer in the OSI model such as Physical Layer, Data Link Layer, Network Layer, Transport Layer, Session Layer, Presentation Layer, and Application Layer. It also discusses the interaction between l
1 views • 41 slides
Understanding Socket Programming and Application Interface
Socket programming involves creating interfaces for applications to communicate over a network. The application programming interface (API) defines how applications interact with the network through sockets, which serve as the point of connection between an application and the network. Different soc
0 views • 16 slides
Crash Course in C Sockets: Network Fundamentals
This lecture delves into the essentials of socket programming in C, covering the significance of C sockets in networking APIs. The session outlines the evolution of C sockets since 1983, emphasizing their role as the foundation of various socket APIs. It explains the client-server architecture, dist
0 views • 25 slides
Overview of Socket Programming in Computer Networks
This information presents a detailed overview of socket programming, covering topics such as Socket API, BSD Socket API, types of sockets (TCP vs UDP), and the basic functions related to I/O multiplexing. It explains the concept of sockets, their various types, their similarities, and differences, a
3 views • 53 slides
Bedforms in Unidirectional Flow: Characteristics and Formation
Bedforms in unidirectional flow exhibit various characteristics such as sediment layer thicknesses, boundary layer dynamics, presence of ripples and dunes, and the interplay between flow velocity and sediment deposition. These bedforms, including ripples and dunes, form due to interactions between t
3 views • 13 slides
Understanding RARP and Transport Layer in Computer Networking
Exploring Reverse Address Resolution Protocol (RARP) for mapping physical addresses to logical addresses in networking, along with insights on the Transport Layer's role in providing communication services to application processes. Learn about RARP packet formats, encapsulation, and the significance
0 views • 41 slides
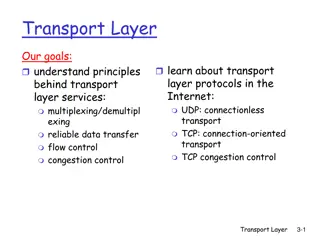
Understanding Internet Transport Layer Services and Protocols
In the realm of networking, exploring the principles of transport layer services is crucial. This involves concepts like multiplexing/demultiplexing, reliable data transfer, flow control, and congestion control, which are facilitated by protocols such as UDP and TCP. The transport layer acts as a br
0 views • 56 slides
Understanding Data Link Layer Communication in Computer Networks
Exploring the data link layer in computer networks, this lecture discusses the node-to-node communication, services provided, such as framing, flow control, error control, and congestion control. Through a series of images, the concept of links and nodes, as well as the responsibilities of the data
0 views • 16 slides
Understanding Data Link Layer in Computer Networking
The Data Link Layer (DLL) is the second layer of the OSI model, responsible for error detection and correction, framing, addressing, synchronization, flow control, and multi-access protocols. It deals with logical link control and media access control, addressing destination hardware, avoiding data
0 views • 49 slides
Enhancements to International Survey of Herbicide Resistant Weeds and Website Overhaul Plan
In 2019, Ian Heap, Director of the International Survey of Herbicide Resistant Weeds (HRAC), is leading an initiative to enhance the survey and overhaul the website to target completion by year-end. The website will undergo a three-tiered redesign focusing on presentation layer, application layer, a
0 views • 11 slides
Meridian: An SDN Platform for Cloud Network Services
Meridian is an SDN platform developed by Mohammad Banikazemi, David Olshefski, Anees Shaikh, John Tracey, and GuohuiWang at IBM T. J. Watson Research Center. The platform focuses on providing cloud network services efficiently. It encompasses an architecture that enables faster and more convenient n
0 views • 21 slides
Understanding ZFS: Structure and Operations
Explore the comprehensive structure and operations of ZFS, covering aspects like MOS layer, object-set layer, Dnode, Block Pointer, and TRIM operations. Learn about the meta-object set (MOS), dataset and snapshot layer (DSL), and storage pool allocator (SPA) modules within ZFS. Understand how ZVOLs,
0 views • 10 slides
Understanding Sockets: A Comprehensive Overview
Sockets provide a standard interface for network protocols like TCP/IP, enabling connections between machines to send and receive data. The TCP protocol, part of the TCP/IP suite, is crucial for internet communications. Learn about the logical structure of sockets and how to create socket connection
0 views • 37 slides
Understanding the Planetary Boundary Layer in Atmospheric Science
The Planetary Boundary Layer (PBL) plays a crucial role in atmospheric dynamics, divided into surface, mixed, stable, and residual layers. During the day, the mixed layer experiences convective motions due to surface heating, while the stable layer dominates during the night. Understanding these lay
0 views • 18 slides
Understanding Transport Layer Security (TLS) and Secure Sockets Layer (SSL)
This content delves into the concepts of Transport Layer Security (TLS) and Secure Sockets Layer (SSL), exploring their origins, application in web security, and protocol stack integration. It covers the TLS/SSL handshake process, key derivation, data transfer mechanisms, and the significance of the
0 views • 26 slides
Understanding Dynamic Routing on Fast Data Plane with VPP and BIRD
Explore the concept of dynamic routing on a fast data plane featuring VPP (Vector Packet Processing) and BIRD (Internet Routing Daemon). Learn how packets traverse a graph, routing mechanisms like BGP, RIP, OSPF, and how sockets and plugins interact to forward traffic efficiently. Discover how VPP a
0 views • 12 slides
Understanding Modular Layer 2 in OpenStack Neutron
Modular Layer 2 (ML2) is a new core plugin in OpenStack Neutron that enables interface with various network mechanisms and types for enhanced flexibility and efficiency. It replaces deprecated plugins like Open vSwitch and Linuxbridge, offering a more modular and feature-rich approach for managing l
0 views • 31 slides
Understanding Earth's Atmosphere: A Detailed Overview
The Earth's atmosphere is a vital layer of gases that encircles our planet, providing the necessary conditions for life to thrive. It consists of several distinct layers, each with unique characteristics and functions. From the troposphere closest to the surface to the thermosphere extending to grea
0 views • 29 slides
Developing Sustainable Infrastructures Amid Climate Change and Global Disasters
Prof. H.A. Odeyinka's keynote paper discusses the importance of developing sustainable infrastructures amidst declining economic resources in the face of climate change and global disasters. It highlights the concepts of climate change, sustainable development, atmospheric layers, ozone layer, carbo
0 views • 25 slides
Understanding Application-layer Protocols in Computer Communication and Networks
Explore Chapter 2 of the course on Computer Communication and Networks, focusing on the application-layer protocols in the client-server paradigm, specific protocols like HTTP and SMTP, client-server architecture, peer-to-peer architecture, and addressing needs in the network application layer.
0 views • 60 slides
Understanding Application Layer Protocols in Communication Networks
Explore the fundamentals of application layer protocols in communication networks, including HTTP, DNS, FTP, and email. Learn about the client-server model, peer-to-peer communication, and the basic workings of TCP sockets. Discover the importance of message syntax, semantics, and processing rules i
0 views • 51 slides
Understanding Transport Layer Services and Challenges
The transport layer provides essential services for reliable communication between end-hosts, including error detection, recovery, and timing preservation. Different transport service models, connection paradigms, and challenges like packet delay, reordering, and loss are discussed in comparison to
0 views • 22 slides
Asynchronous Zero-copy Communication in Sockets Direct Protocol over InfiniBand
This study explores the implementation of Asynchronous Zero-copy Communication for Synchronous Sockets in the Sockets Direct Protocol over InfiniBand. It discusses InfiniBand's high performance, low latency, and advanced features, as well as the Sockets Direct Protocol as a high-performance alternat
0 views • 36 slides
Enhancing Bitcoin Network Through Trust Extraction and Blockchain Scalability
Explore methods to extract trust from the blockchain and enhance scalability through Layer 1 and Layer 2 changes, including parameters adjustment, consensus algorithm modifications, sharding, payment networks, and side chains. Learn about payment channels, Bitcoin throughput, and strategies to incre
0 views • 23 slides
Understanding Networking Sockets API in Operating Systems
Delve into networking sockets API for inter-process communication and data transfer, exploring client-server models, request-response protocols, and communication paradigms across different networks. Learn about the mechanisms in OS for networking, examining practical examples, codes, and readings t
0 views • 30 slides
Understanding ARP, ICMP, and DHCP in TCP/IP Protocol Stack
ARP (Address Resolution Protocol) plays a crucial role in bridging the Layer 2/Layer 3 addressing boundary in the TCP/IP protocol stack, allowing IP to be agnostic about layer 2 addressing while still using layer 2 for packet delivery. Machines ARP for MAC addresses within their local network, where
0 views • 39 slides
High Performance User-Level Sockets over Gigabit Ethernet
Presentation overview of the design challenges, performance enhancement techniques, and results related to implementing high-performance user-level sockets over Gigabit Ethernet networks. The background and motivation discuss the limitations of traditional kernel-based implementations and the need f
1 views • 34 slides
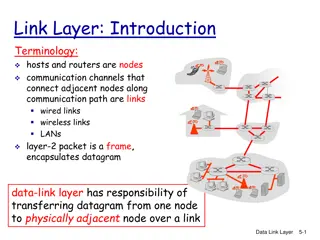
Understanding the Link Layer in Computer Communication and Networks
The link layer, an essential component in computer networks, is implemented at every host through adapters like NICs or Ethernet/802.11 cards. It handles tasks such as frame encapsulation, error checking, and flow control to ensure reliable data transmission between nodes. Link layer services includ
0 views • 64 slides
Understanding Link Layer in Computer Networking
The link layer, also known as the data link layer, plays a crucial role in transferring data between adjacent nodes over communication links. This layer is responsible for framing, access control, reliable delivery, error detection and correction, flow control, and more. It is implemented in network
0 views • 34 slides
Advanced Flow Control Mechanisms for Sockets Direct Protocol over InfiniBand
Discussing the benefits of InfiniBand technology in high-speed networking, challenges TCP/IP faces in utilizing network features properly, and the implementation of Sockets Direct Protocol (SDP) to enhance network performance and capabilities, with a focus on advanced flow control techniques using R
0 views • 28 slides
Comprehensive Overview of Encryption Techniques and Algorithms
Explore the world of encryption with insights into symmetric and public key encryption, certificate authorities, secure sockets layer, substitution ciphers, block ciphers, AES, and public key cryptography. Delve into the intricacies of encryption keys and algorithms, including the AES process, Diffi
0 views • 31 slides