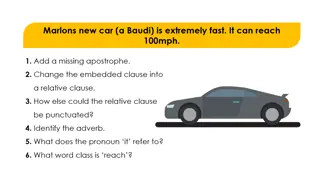
Enigmatic Nightly Quest for Illuminating Spheres
As a mysterious figure navigates a tranquil lake, collecting glowing spheres under the night sky, an aura of secrecy and urgency surrounds his mission. The atmosphere is enigmatic and captivating, with hints of a hidden world waiting to be discovered.
1 views • 8 slides
Overview of the Official Secrets Act, 1923 in India
The Official Secrets Act, 1923 in India focuses on protecting official records of the Central and State Governments, safeguarding information privacy, and imposing penalties for activities prejudicial to the State's interests. Rooted in the British colonial era, the Act aims to maintain national sec
2 views • 12 slides
Comprehensive Guide to Electoral Observation and Reporting
This comprehensive guide covers various aspects of electoral observation and reporting, including pre-election preparations, election day processes, and post-election verification. Topics discussed include legal frameworks, voter registration, election administration, political party registration, v
2 views • 20 slides
Sadao's Dilemma: The Enemy's Escape
Sadao, a skilled surgeon, faces a moral dilemma when treating an American soldier in secrecy. Despite planning for the soldier's disposal, he ultimately aids in the soldier's escape, leading to conflicting emotions and confrontations with the General. The story delves into themes of duty, loyalty, a
0 views • 7 slides
Impact of Right to Information Act on Transparency and Accountability: Challenges and the Way Forward
The Right to Information Act is a crucial tool in transforming the culture of secrecy to transparency. It aims to promote accountability, eradicate corruption, and empower citizens. However, the implementation of RTI faces challenges such as lack of proactive thinking in bureaucracy and infrastructu
11 views • 15 slides
Exploring Jewish Customs & Rituals: Embracing End-of-Life Conversations
The content delves into the importance of discussing death and embracing Jewish customs and rituals related to end-of-life practices. It highlights efforts to educate the community about the Chevrah Kadisha, Tahara, and other traditional practices. The goal is to promote understanding and acceptance
0 views • 39 slides
Reflections on the Word: Joel 2:12-18, Psalms 51, 2 Corinthians 5:20-6:2, Matthew 6:1-6, 16-18
In the readings from Joel, Psalms, 2 Corinthians, and Matthew, we are called to wholeheartedly return to God, seeking mercy and compassion for our sins. We are reminded to offer sincere repentance, seek reconciliation with God, and perform acts of righteousness with humility and sincerity, knowing t
0 views • 22 slides
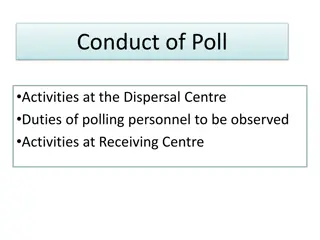
Polling Activities and Duties at Various Centers
Duties and activities at dispersal, receiving, distribution centers, and on polling day are crucial for ensuring a fair election process. Micro-observers play a key role in observing and reporting any irregularities. Polling personnel must adhere to strict guidelines, such as verifying voter identif
1 views • 58 slides
Securing Protocols with Fully Encrypted Protocols (FEPs)
In this research presented at the Cryptographic Applications Workshop, Ellis Fenske and Aaron Johnson address the challenges of Fully Encrypted Protocols (FEPs). They highlight the lack of precise understanding, formalized goals, and proven security in existing FEPs. The work introduces new security
0 views • 29 slides
The Politics of Radical Open Access Publishing: A Genealogical Exploration
Exploring the intersections of radical open access publishing, secrecy, authorship, dissemination, and experimentation through a genealogical lens. Key figures like Janneke Adema and Gary Hall are discussed, along with the political nature of books. The importance of openness and conversation in int
0 views • 20 slides
Unraveling the Mystery of Area 51
Delve into the intriguing world of Area 51, a place shrouded in secrecy and surrounded by alien conspiracy theories. Discover the compelling reasons behind why Area 51 has become one of the greatest mysteries of our time, as explored through videos and discussions on alien encounters and government
0 views • 15 slides
Cryptography in Bounded Storage Model: Ensuring Secure Communication
Cryptography in the Bounded Storage Model provides insights into securing communication with secrecy and authenticity. The model limits adversaries' memory without runtime restrictions, ensuring unconditional security for various primitives. Explore how this model safeguards messages from eavesdropp
0 views • 42 slides
Unveiling Global Financial Secrecy: The Financial Secrecy Index
The Financial Secrecy Index sheds light on global financial secrecy by identifying jurisdictions offering opacity to non-residents to evade laws and taxes. It critiques tax haven lists, highlights OECD standards, and calls for objective measures. It showcases global transparency standings and emphas
0 views • 16 slides
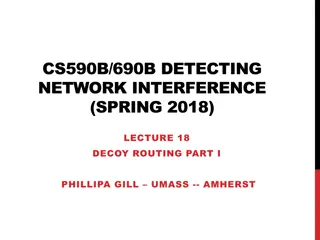
Decoy Routing in Internet Circumvention Strategies
Decoy routing in network interference involves making hosts on the internet appear as proxy servers, enabling access to blacklisted sites with normal latency and throughput. The approach aims to maintain content secrecy and actual destination privacy by making traffic filtering difficult for interme
0 views • 14 slides
Combatting Money Laundering: Understanding the AMLA and BSA
The Anti-Money Laundering Act (AMLA) and Bank Secrecy Act (BSA) play crucial roles in preventing money laundering and illicit activities. The AMLA imposes liabilities on businesses and individuals, with low intent thresholds, while the BSA empowers the Treasury to enforce AML programs. Understanding
0 views • 32 slides
Post-Quantum Cryptography: Safeguarding Secrets in the Digital Age
Delve into the realm of post-quantum cryptography and learn about the evolving landscape of secure communication. Explore topics such as Supersingular Isogeny Graphs, Ring-Learning With Errors, and the significance of key exchange in maintaining confidentiality. Discover the foundations of public ke
0 views • 39 slides
Secrets on Public Blockchain: Security and Efficiency
Exploring the challenges of maintaining secrecy on a public blockchain, this study emphasizes the importance of proactive secret-sharing protocols to safeguard sensitive information from adversaries while ensuring efficiency and scalability. The research delves into the complexities of keeping secre
0 views • 22 slides
Proxy Voting in Indian Elections: Developments and Perspectives
India has seen progress in allowing proxy voting for Non-Resident Indians, with recent proposals to extend this privilege to overseas Indians. The initiative aims to enhance voter participation, especially for those residing abroad. While some political parties support proxy voting, concerns exist r
0 views • 35 slides
Gospel Doctrine
Jesus's miracles, the youth's donation to missionary fund, and Elder William R. Bradford's response highlight the importance of selfless service and true discipleship. Lessons learned include the value of quiet recognition, service devoid of seeking recognition, and following Jesus's teachings in se
0 views • 39 slides
Overview of Trade Secrets and Legal Framework in the United States
Understanding trade secrets, their definition, protection, and examples is crucial for businesses operating in the United States. This content provides insights into the laws, including the Uniform Trade Secrets Act and the Economic Espionage Act, governing trade secrets at both state and federal le
0 views • 39 slides