Becoming a Better Ally
Understanding privilege is essential to becoming a better ally in creating a more inclusive workplace. Privilege encompasses unearned benefits based on social groups like race, gender, and class. Instead of feeling guilty, individuals in positions of privilege should empathetically leverage their ad
0 views • 28 slides
Improving Multi-Link Power Management Efficiency in IEEE 802.11 Networks
The document discusses challenges with per-link power mode changes in multi-link scenarios in IEEE 802.11 networks, proposing a solution for more efficient power management. It addresses issues such as latency and inefficiencies in signaling for power mode changes, introducing scheduled multi-link p
6 views • 9 slides
Understanding Privilege and Oppression in Diversity Training Session
Explore privilege, intersectionality, and structural inequity in a training session led by Jo Yuen. Participants will learn key terms, allyship strategies, and engage in discussions to foster a safe and open environment. The session includes a working agreement, introductions, breakout discussions,
0 views • 22 slides
Insurance Investigations: Handling Privilege, Coverage, and Disclosure
Explore the nuances of responding to insurance investigations in this 90-minute interactive webinar. Learn how to cooperate effectively while protecting privilege, coverage, and confidential information. Gain valuable insights on preventing insurer abuse, misuse, and disclosure, as well as safeguard
0 views • 52 slides
Exploring Privilege and Racism in Our Communities
Delve into the concepts of privilege, white privilege, and systemic racism through dialogues and guidelines. Understand how unearned benefits affect social groups and ways to address these issues within our neighborhoods. Explore actions within your sphere of influence to promote equity and justice.
0 views • 6 slides
State Privilege to Refuse Production of Documents in Courts: A Comparative Analysis between Great Britain and India
Doctrine of state privilege allows governments certain privileges, such as the right to refuse production of documents in courts. This privilege is recognized in both Great Britain and India, with specific statutory provisions defining its scope and application. In Great Britain, the Crown's powers
2 views • 12 slides
Insightful Book Club Picks for Thoughtful Discussions on Race and Privilege
Thought-provoking book club picks for 2020-2021 explore topics of race, privilege, and feedback discussions around White Fragility and Rules of Engagement. These selections encourage open dialogue, trust-building, and self-reflection on challenging yet essential subjects.
0 views • 14 slides
A Comprehensive Guide to Getting a Driver Privilege Card in Virginia
Essential information on obtaining a Driver Privilege Card (DPC) in Virginia, including the three types of driving credentials, differences between the cards, requirements for applying, and necessary documents like proofs of identity, social security number, Virginia residency, and Virginia tax retu
0 views • 11 slides
Legal Professional Privilege in the Protection of Taxpayer Rights: South African Perspective
Legal professional privilege plays a crucial role in safeguarding taxpayer rights in South Africa. This privilege ensures that communications between a legal advisor and client remain confidential, promoting fairness in litigation and enabling a proper functioning adversarial system of justice. The
0 views • 16 slides
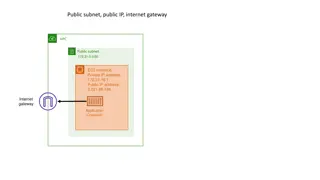
Networking Modes in AWS VPC Environments
Explore different networking modes such as Bridge mode with static mapping, Bridge mode with dynamic mapping, and AWS VPC networking mode in an AWS VPC environment with various configurations and scenarios.
0 views • 18 slides
Understanding Mode-S Radar Operations and Identifiers
This simplified explanation delves into the fundamental principles of radar operations, focusing on Primary and Secondary radar systems, including Mode A/C and Mode S functionalities. It covers radar interrogation, replies, and the significance of radar identifiers (II and SI codes) in managing over
0 views • 19 slides
Parallel Implementation of Multivariate Empirical Mode Decomposition on GPU
Empirical Mode Decomposition (EMD) is a signal processing technique used for separating different oscillation modes in a time series signal. This paper explores the parallel implementation of Multivariate Empirical Mode Decomposition (MEMD) on GPU, discussing numerical steps, implementation details,
1 views • 15 slides
Patch Bundle Mode Walkthrough for Device Configuration
Explore the Patch Bundle Mode walkthrough consisting of flowcharts and pseudo code examples for controlling a device's patch mode, downloading configurations, and changing device modes. The content provides a detailed guide on using commands to initiate patch burst mode, specify I2C addresses, and t
0 views • 4 slides
Understanding Legal Privilege in Investigations and Pre-termination Negotiations
This content delves into recent developments in the law of privilege, highlighting the types of privilege such as legal professional privilege, litigation privilege, and without prejudice privilege. It explains working definitions of legal advice privilege and litigation privilege, emphasizing commu
0 views • 13 slides
Understanding Privilege Escalation and Backdoor Installation in Cybersecurity
Privilege escalation allows unauthorized access to system resources, while backdoors enable persistent access for attackers. The attack scenario involves compromising a website to deploy malicious files, such as Remote Access Trojans, leading to potential system compromise.
0 views • 13 slides
Understanding Privilege and Its Implications in Society
Exploring various forms of privilege such as class, ability, religion, sexuality, and race, this content delves into the advantages individuals may have based on their social identities. It discusses how privilege influences one's access to resources, treatment in society, and overall experiences in
1 views • 14 slides
Understanding Legal Privilege and Confidentiality in the Legal System
Legal privilege and confidentiality play crucial roles in protecting communications between clients and lawyers, especially in the context of legal advice and ongoing litigation. This article explores the nuances of privilege, types of communications covered, scenarios where privilege can be waived,
1 views • 15 slides
Understanding CMRR in Differential Amplifiers
Differential input amplifiers, including operational, instrumentation, and difference amplifiers, play a crucial role in amplifying differential signals while rejecting common-mode noise. The Common-Mode Rejection Ratio (CMRR) is a key parameter in these amplifiers, indicating their ability to suppr
0 views • 48 slides
Exploring Equality, Equity, and Social Justice
This content delves into important topics such as the impact of diversity, privilege, and the need for inclusivity in society. It discusses the significance of recognizing privilege, understanding marginalized groups, and taking action to combat inequalities. The inclusion of diverse viewpoints spar
0 views • 26 slides
Legal Case Analysis: Brunton v. Kruger
Donald Patrick Eckler, a partner at Pretzel & Stouffer, Chartered, represents clients involved in a will contest case between June Brunton and her family members. The case involves allegations of undue influence and diminished capacity in the execution of trust documents. The court examines the conf
0 views • 9 slides
Best Bond Cleaning Services in Kenny
If you want the Best Bond Cleaning Services in Kenny, visit Privilege Cleaning. Privilege Cleaning provides 5-star standard commercial cleaning in Canberra for offices, retail outlets, showrooms, supermarkets, schools, hospitals, and more. Their prof
1 views • 6 slides
Understanding Queer Perspectives on Privilege, Whiteness, and Class
Explore the nuanced concepts of privilege, whiteness, and class through a queer lens as discussed in Bruce Henderson's book "Queer Studies: Beyond Binaries." Delve into the invisible benefits of privilege, the implications of whiteness as a societal construct, and the intersectionality of social and
0 views • 22 slides
Understanding Privilege and Creating Safe Zone Programs at SMA
Creating safe spaces and bystander training programs at SMA involves launching interventions, ally programs, and understanding campus-wide privilege. The agenda includes sharing resources, discussing campus climate challenges, and promoting collaboration. Introductions highlight key personnel. Outco
0 views • 18 slides
Understanding Ableism and Non-Disabled Privilege
Ableism and Non-Disabled Privilege are explored in depth, highlighting definitions and concepts related to power, privilege, oppression at individual, institutional, and cultural levels. The content delves into attitudes, beliefs, socialization, and behaviors that perpetuate discrimination, as well
0 views • 12 slides
Understanding Privilege Escalation in Windows and Linux Systems
Privilege escalation attacks are malicious tactics used by attackers to gain unauthorized access and elevated privileges in a system. These attacks exploit vulnerabilities in operating systems and web applications, allowing attackers to move deeper into a network to access high-value assets. This co
0 views • 28 slides
Understanding the Fiduciary Duty Exception to Attorney-Client Privilege
Several courts have deliberated on extending attorney-client privilege to protect communications between law firms' in-house counsel seeking advice on handling potential malpractice claims. This exception, known as the fiduciary duty exception, has faced scrutiny and rejection in recent cases, safeg
0 views • 36 slides
Handling Privilege and Discovery Issues in Corporate Litigation
Exploring privilege assertions and discovery rules in Illinois law for corporate litigation cases, emphasizing the burden of proof on privilege assertion, strong disfavor of privileges, and exceptions in certain circumstances. Understanding the importance of disclosure in legal proceedings and the n
0 views • 51 slides
Understanding User Mode, Kernel Mode, Interrupts, and System Calls in Computer Architecture
In modern computers following Von Newman Architecture, programs and data are stored in RAM. The CPU, RAM, ROM, and devices communicate via address and data buses. The system operates in both kernel and user modes, where kernel mode allows full system control, while user mode restricts access for sec
0 views • 29 slides
Understanding Sexual Assault Communications Privilege and Balancing Public Interests
Exploring the complexities and practical challenges surrounding Sexual Assault Communications Privilege (SACP), this content delves into the reasons for its establishment, the services it provides, and the implications for both defence lawyers and complainants in sexual assault trials. It sheds ligh
0 views • 19 slides
Understanding Waiver of Client Legal Privilege in Civil Law
Discussion on the waiver of client legal privilege in civil law, focusing on the governing laws, requirements of inconsistency, implications of s.122 of the ENULA (NT), and the fact-sensitive nature of such cases. Insights presented from the NTBA-CDU 2014 Civil Law Conference held in Dili, Timor-Les
0 views • 13 slides
Local MAC Address Assignment Protocol (LAAP) and 802.1CQ
The Local MAC Address Assignment Protocol (LAAP) in conjunction with 802.1CQ specifies protocols and procedures for locally unique assignment of MAC addresses in IEEE 802 networks. LAAP operates in two modes - Server Mode and Peer-to-Peer Mode, ensuring efficient allocation of MAC addresses while av
0 views • 15 slides
Practical and Ethical Issues in Office of the Child's Representative
The role of the Guardian ad Litem (GAL) in safeguarding the child's privilege in dependency and neglect cases, guidance for determining privilege holders, ethical obligations of the GAL, and procedures for waiver and disputes over waiver scope are discussed in the context of practical and ethical is
0 views • 19 slides
Understanding Attorney-Client Privilege for Financial Institutions
Explore the intricacies of attorney-client privilege, bank examination privilege, and work product doctrine in the context of internal investigations and audits within financial institutions. Learn how these protections safeguard confidential information, promote open communication, and guide intera
0 views • 46 slides
Windows Security Overview and Best Practices
Windows operating system security overview focusing on preventing unauthorized access, privilege escalation, and password vulnerabilities. Includes countermeasures such as setting proper permissions, implementing strong passwords, and detecting vulnerabilities. Covering topics like remote password g
0 views • 6 slides
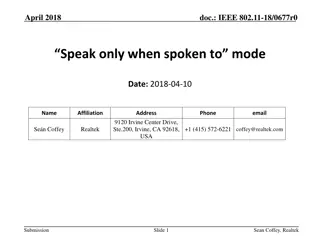
IEEE 802.11-18/0677r0: Speak-Only-When-Spoken-To Mode in Wireless Networking
This document discusses the implementation of a speak-only-when-spoken-to mode in IEEE 802.11-18/0677r0 for managing various devices within wireless networks. It highlights the benefits of this mode for maintaining throughput efficiency and coexistence, especially in scenarios involving 11b-only dev
0 views • 7 slides
Understanding mean, median, and mode in statistics
In statistics, the mean represents the average value, the median is the middle value that divides a dataset into two halves, and the mode is the most frequent value. This guide explains how to calculate these statistical measures and provides examples. Additionally, it demonstrates how to estimate t
0 views • 11 slides
Control Plane Security in Self-service Cloud Platforms
Exploring the risks and implications of client security on cloud platforms, this content discusses potential attacks, limitations in deploying services, and a proposed solution called SSC. The paper highlights the need for privilege separation and least privilege principles to enhance cloud security
0 views • 45 slides
Understanding Attorney-Client Privilege
Privilege in law refers to the right to block certain evidence from being admitted in a case, even if it is relevant. Attorney-client privilege, like the one defined in Texas Rule 503, allows individuals consulting a lawyer for legal advice to keep their discussions confidential. Exceptions to this
0 views • 54 slides
Understanding Context Switching and User-Kernel Interaction in Operating Systems
Context switching in operating systems involves a seamless transition between user-level threads without the kernel's awareness. User-level code manages register state and stack pointers, while user-kernel mode switching requires changing processor privilege levels and agreement on information excha
0 views • 25 slides
Evolution of Vertica - Eon Mode Vertica Overview
Explore the advancement of Vertica from Enterprise Mode to AWS Eon Mode, offering fast, scalable, and open architecture SQL databases. Learn about the simplified provisioning and data loading process in Eon Mode Vertica using EC2 instances with storage and an S3 bucket.
0 views • 17 slides