Ask On Data for Efficient Data Wrangling in Data Engineering
In today's data-driven world, organizations rely on robust data engineering pipelines to collect, process, and analyze vast amounts of data efficiently. At the heart of these pipelines lies data wrangling, a critical process that involves cleaning, transforming, and preparing raw data for analysis.
2 views • 2 slides
Understanding the Coase Theorem: Property Rights and Economic Efficiency
The Coase Theorem, developed by economist Ronald Coase, posits that under certain conditions, bargaining related to property rights will lead to an optimal outcome regardless of the initial distribution. It provides a framework for resolving conflicts by emphasizing negotiation and efficient market
0 views • 10 slides
Understanding Data Rate Limits in Data Communications
Data rate limits in data communications are crucial for determining how fast data can be transmitted over a channel. Factors such as available bandwidth, signal levels, and channel quality influence data rate. Nyquist and Shannon's theoretical formulas help calculate data rate for noiseless and nois
0 views • 4 slides
Occupational Noise Exposure and Hearing Conservation Training Program
Learn about the Occupational Noise Exposure and Hearing Conservation Training Program presented by the Office of Environmental Health and Safety at ECU. This program aims to educate workers about the risks of noise-induced hearing loss, the importance of prevention, and the selection of appropriate
1 views • 20 slides
Understanding Naive Bayes Classifier in Data Science
Naive Bayes classifier is a probabilistic framework used in data science for classification problems. It leverages Bayes' Theorem to model probabilistic relationships between attributes and class variables. The classifier is particularly useful in scenarios where the relationship between attributes
1 views • 28 slides
Language Identification System for DARPA RATS Program Evaluation
The Patrol Team Language Identification System was developed for DARPA RATS Program to create algorithms and software for speech tasks in noisy environments. The system involved analyzing datasets, implementing subsystems for language identification, and evaluating performance across different langu
0 views • 19 slides
Family, Fun, and Thanksgiving Poetry Collection
Dive into a delightful collection of poems celebrating family life, gratitude, and the joy of Thanksgiving. From whimsical tales of noisy households to heartwarming reflections on love and togetherness, these charming verses by Catherine and Lawrence Anholt are sure to bring a smile to your face. Ex
0 views • 12 slides
Text Analytics and Machine Learning System Overview
The course covers a range of topics including clustering, text summarization, named entity recognition, sentiment analysis, and recommender systems. The system architecture involves Kibana logs, user recommendations, storage, preprocessing, and various modules for processing text data. The clusterin
0 views • 54 slides
Understanding Hearing Conservation and Noise Control in the Workplace
This presentation covers the importance of hearing conservation, the anatomy of the ear, different types of hearing loss, factors affecting the degree of risk, the concept of decibels, common noisy environments, and advantages and disadvantages of hearing protection methods. It emphasizes the need f
0 views • 29 slides
Protect Your Hearing: Strategies for Prevention
Strategies for minimizing noise-related threats in operational environments are crucial to prevent permanent hearing loss. Understanding the risks of loud noise exposure, utilizing hearing protection, undergoing regular audiometric testing, and maintaining noise records are essential components of t
0 views • 22 slides
Troubleshooting Common Computer Issues: Noisy Fans, Overheating, and Cooling Tips
Learn how to address common computer problems such as noisy fans and overheating. Discover practical solutions to reduce fan noise, prevent overheating, and keep your laptop cool for optimal performance. Expert tips on maintaining a healthy computer environment are shared by tech enthusiasts Saif Fa
0 views • 5 slides
Quantum Circuit Simulations and Electromagnetic Analyses in Quantum Photonics
Explore the world of quantum photonics with insights into two-qubit photon counters, jointed cavities, qubit pads, and quantum circuit simulations. Ansys simulations and experimental data by researchers Alessandro D'Elia and Claudio Gatti provide in-depth analysis of quantum phenomena. Discover the
0 views • 7 slides
Understanding Least Squares Estimation in Global Warming Data Analysis
Exploring least squares estimation in the context of global warming data analysis, this content illustrates the process of fitting a curve to observed data points using a simple form of data analysis. It discusses noisy observed data, assumptions, errors, and the importance of model parameters in ma
0 views • 38 slides
Exploring "When My Noisy Mind Quiets" by Georgia Heard
Dive into the poem "When My Noisy Mind Quiets" by Georgia Heard where the speaker reflects on finding peace and calm amidst a cluttered mind. The analysis explores themes of inner turmoil, self-reflection, and the transformative power of silence on one's voice and thoughts.
0 views • 7 slides
DNA Data Archival: Solving Read Consensus Using OneJoin Algorithm
DNA data storage presents challenges in archiving digital information efficiently due to the nature of biological media. This article delves into the complexities of DNA data storage, emphasizing the importance of robust archival solutions. The OneJoin algorithm offers a scalable and cross-architect
0 views • 8 slides
Understanding N-Gram Models in Language Modelling
N-gram models play a crucial role in language modelling by predicting the next word in a sequence based on the probability of previous words. This technology is used in various applications such as word prediction, speech recognition, and spelling correction. By analyzing history and probabilities,
0 views • 101 slides
Geoscientific Data Analysis Using Unix and GMT: Practical Methods and Techniques
Explore techniques for analyzing geoscientific data using Unix and GMT, including handling irregularly spaced data, fitting curves, processing noisy data, and utilizing filtering methods. Learn about spline usage, polynomial fitting, correlation coefficients, and Gnuplot functionalities.
0 views • 23 slides
Analog Accelerator: Memristor Basics and ISAAC Accelerator
Explore the world of analog acceleration with topics covering memristor basics and the ISAAC accelerator. From understanding noisy analog phenomena to leveraging wires as ALUs, delve into crossbars for vector-matrix multiplication and the challenges of high ADC/DAC area/energy. Discover solutions li
0 views • 23 slides
Explainable Recommendation Using Attentive Multi-View Learning
The research presented at the 33rd AAAI Conference on Artificial Intelligence focuses on developing an explainable deep model for recommendation systems. It addresses challenges in extracting explicit features from noisy data and proposes a Deep Explicit Attentive Multi-View Learning Model. This mod
0 views • 19 slides
Understanding Spelling Correction Through the Noisy Channel Model
Explore the fascinating world of spelling correction using the Noisy Channel Model, which involves tasks such as error detection, correction, types of errors, rates of errors, and strategies for non-word and real-word spelling errors. Learn about applications and implications in various contexts suc
0 views • 51 slides
Spelling Correction Techniques and Models in Information Retrieval
Explore the world of spelling correction through the lens of Information Retrieval and Web Search. Dive into probabilistic models, non-word and real-word spelling errors, rates of spelling errors, correction strategies, and more. Gain insights from Christopher Manning on applications, types of error
0 views • 48 slides
Understanding Probability and Planning Under Uncertainty
Probability plays a crucial role in decision-making under uncertainty, where factors like laziness, ignorance, and randomness influence outcomes. This lecture covers key concepts in probability, including outcomes, events, random variables, and conditional independence. It also delves into the chall
0 views • 42 slides
Understanding Small Set Expansion in Johnson Graphs
In this detailed piece, Subhash Khot, Dor Minzer, Dana Moshkovitz, and Muli Safra explore the fascinating concept of Small Set Expansion in Johnson Graphs. The Johnson Graph is defined as a representation where nodes are sets of size K in a universe of size N, and two sets are connected if they inte
0 views • 14 slides
Consensus Relevance with Topic and Worker Models
Study focuses on recovering actual relevance of a topic-document pair using noisy predictions from multiple labelers. Various supervised, semi-supervised, and unsupervised approaches are explored. The goal is to obtain a more reliable signal from the crowd or benefit from scale through expert qualit
0 views • 15 slides
Strategic Communication in Bayesian Persuasion
Understanding the concepts of cheap talk and Bayesian persuasion in strategic communication, where information can be conveyed via direct communication even in the presence of conflicts of interest. Explore how biased senders influence noisy communication, and analyze communication equilibria in sce
0 views • 22 slides
Challenges and Advances in Multilingual and Code-Mixed ASR Systems
Recent advances in multilingual and code-mixed models for streaming end-to-end ASR systems present challenges including low resource Indic language data, multiple dialects, code-mixing, and noisy environments. These challenges impact ASR modeling by causing convergence issues, higher Word Error Rate
0 views • 34 slides
Algorithm for Determining Endpoints in Speech Recognition
This article discusses an algorithm proposed by L.R. Rabiner and M.R. Sambur in 1975 for determining endpoints in isolated utterances. The algorithm focuses on detecting word boundaries in speech through the recognition of silence, which can lead to reduced processing load and increased convenience,
0 views • 22 slides
The Power of Silence and Solitude in Spiritual Growth
Embracing silence and solitude as spiritual disciplines can lead to profound introspection, contemplation of past and future, and a deepening relationship with God. Drawing inspiration from biblical examples, this practice offers a unique way to connect with one's inner self and faith, amidst a nois
0 views • 14 slides
Innovative Device-Free Passive Motion Detection System
This research presents RASID, a robust WLAN device-free passive motion detection system that can detect human presence without the need for carrying any devices or interacting actively with the system. By analyzing changes in received signal strength behavior, the system can identify human motions.
0 views • 43 slides
Whisper: A Wristwatch-Style Wearable Handset
Whisper is a unique wrist-worn handset that allows users to interact with their cellphones by inserting a fingertip into the ear canal. It offers hands-free operation with over ten commands accessible through finger taps, ideal for adjusting settings or making calls. The bone conduction technology e
0 views • 6 slides
Strategies for Dealing with Noisy Data in Classification Problems
Dealing with noisy data in classification problems is crucial for maintaining model performance. This challenge requires identifying noise, understanding its types, implementing noise filtering techniques, and using robust learners. Experimental comparative analysis helps in evaluating these strateg
0 views • 45 slides
Secure Computation Laboratory: Modeling Attacks on PUF Systems
Explore the research on physically unclonable function (PUF) modeling attacks using Logistic Regression and CMA-ES algorithms. Learn to simulate and analyze reliable and noisy PUF instances, implement attacks, and assess modeling accuracy. The laboratory goals include simulating APUF and XOR PUF sys
0 views • 10 slides
Improved Cepstra Minimum-Mean-Square-Error Noise Reduction Algorithm for Robust Speech Recognition
This study introduces an improved cepstra minimum-mean-square-error noise reduction algorithm for robust speech recognition. It explores the effectiveness of conventional noise-robust front-ends with Gaussian mixture models (GMMs) and deep neural networks (DNNs). The research demonstrates the benefi
0 views • 43 slides
Exploring Noisy Output in Neural Networks: From Escape Rate to Soft Threshold
Delve into the intricacies of noisy output in neural networks through topics such as the variation of membrane potential with white noise approximation, autocorrelation of Poisson processes, and the effects of noise on integrate-and-fire systems, both superthreshold and subthreshold. This exploratio
0 views • 34 slides
Understanding Neural Response Variability and Connectivity Dynamics
Explore the intricate relationship between feedforward, feedback, and response variability in neural networks. Dive into the impact of noise on effective connectivity and network topology, as well as the challenges posed by noisy and delayed communication between brain regions. Discover the applicat
0 views • 14 slides
Handling Label Noise in Semi-Supervised Temporal Action Localization
The Abstract Semi-Supervised Temporal Action Localization (SS-TAL) framework aims to enhance the generalization capability of action detectors using large-scale unlabeled videos. Despite recent progress, a significant challenge persists due to noisy pseudo-labels hindering efficient learning from ab
0 views • 30 slides
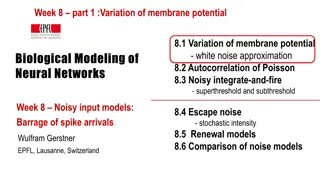
Exploring Membrane Potential Variations in Neural Networks
Delve into the dynamics of membrane potential variations in neural networks through topics like white noise approximation, autocorrelation of Poisson processes, and the Noisy Integrate-and-Fire model. Investigate how these variations manifest at different thresholds, shedding light on the biological
0 views • 63 slides
Data Link Control and Protocols in Computer Networks
This chapter discusses various protocols for handling data link control in computer networks, focusing on noiseless and noisy channels. It covers protocols like Stop-and-Wait ARQ, Go-Back-N ARQ, and Selective Repeat ARQ, explaining how they ensure error-free transmission and flow control. The concep
0 views • 12 slides
Data Mining Course Project Overview: Pre-Processing to Classification
Explore the challenges and tasks involved in a data mining course project, from pre-processing to redefining classification tasks. The project involves handling a large dataset with numerous features, including numerical and categorical ones, addressing missing values, noisy data, and feature select
0 views • 33 slides
Understanding Machine Learning: Decision Trees and Overfitting
Foundations of Artificial Intelligence delve into the intricacies of Machine Learning, focusing on Decision Trees, generalization, overfitting, and model selection. The extensions of the Decision Tree Learning Algorithm address challenges such as noisy data, model overfitting, and methods like cross
0 views • 13 slides