United States Lawful Interception Market
The United States Lawful Interception Market Size is Expected to Hold a Significant Share by 2033, at a CAGR of 14.45% during the forecast period 2023 to 2033.
2 views • 4 slides
Understanding Data Protection Essentials
Explore the fundamentals of data protection, including key principles, lawful processing, identifying personal data, managing breaches, and handling information rights requests. Learn about GDPR principles, special category data, and the lawful bases for processing personal information.
4 views • 15 slides
Pathogen-reduced platelets: clinical highlights
Pathogen-reduced platelets play a crucial role in reducing the risk of transfusion-transmitted infections through pathogen inactivation technology (PIT). This technology provides an additional layer of safety against various pathogens including viruses, bacteria, protozoa, and leukocytes. Platelet c
2 views • 17 slides
Early Intercept Project: Enhancing Mental Health Services in Arlington County
The Early Intercept Project is a collaborative effort between DBHDS, DHS, and ACSO aimed at improving mental health services in Arlington County. Key objectives include reducing ECO recidivism, integrating PBMP and FDP programs, and enhancing discharge planning for clients in state hospitals. Throug
0 views • 11 slides
Update on Pathogen Reduction of Platelets at National Haemovigilance Conference 2023
This update covers the latest developments in pathogen reduction of platelets, including the introduction of whole blood containing platelets. Key strategic initiatives focus on assessing post-collection blood product manipulation processes and developing new products to meet healthcare needs. The a
0 views • 25 slides
Understanding Spread Spectrum Communication
Spread spectrum communication is a favored technology in military and commercial applications due to its resistance to jamming and interception. By spreading signals over a wide range of frequencies, it enhances security through encryption and authentication, making it challenging for attackers to d
4 views • 17 slides
Exploring Nonlinear Relationships in Econometrics
Discover the complexities of nonlinear relationships through polynomials, dummy variables, and interactions between continuous variables in econometrics. Delve into cost and product curves, average and marginal cost curves, and their implications in economic analysis. Understand the application of d
2 views • 34 slides
Understanding Graphs of Straight Lines and Equations
Learn how to graph equations and find equations from graphs of straight lines. Explore tables of values, plotting points on a coordinate plane, drawing lines through points, and identifying relationships between graphs and algebraic expressions. Discover the gradient-intercept form of a straight lin
0 views • 14 slides
Understanding Lawful Consideration and Public Policy in Contracts
Lawful consideration and public policy play vital roles in determining the validity of agreements. According to Section 23 and Section 24 of contract law, consideration and object must be lawful, and agreements are void if they involve unlawful elements. Public policy considerations guide the judici
0 views • 4 slides
Understanding Quadratic Functions: Graphing and Analysis
This content covers graphing quadratic functions in the form f(x)=ax^2+bx+c, focusing on finding maximum and minimum values, domain, and range. Key concepts include determining the direction of the parabola, identifying the y-intercept and axis of symmetry, finding the vertex, and plotting points to
0 views • 10 slides
Understanding Bonam Partem in Legal Interpretation
Bonam Partem, meaning words in their lawful and rightful sense, has significant implications in legal interpretation. It entails that statutes should be interpreted based on their legitimate and recognized meanings. The principle is demonstrated in various legal cases, emphasizing the importance of
1 views • 7 slides
Understanding Best Fit Lines in Data Analysis
Exploring the concept of best fit lines in data analysis, this lesson covers how to determine a line of best fit from a scatter plot, interpret the slope and intercept of the line, and fit linear functions to data points. Through examples and steps, students learn to graph data, find the equation of
1 views • 36 slides
Understanding Equations of Planes in Three-Dimensional Geometry
In this module, we delve into the concept of planes in three-dimensional geometry. Starting with the definition of a plane and its general equation, we explore intercept form, normal form, and practical examples. Equations, concepts, and applications are explained methodically to enhance understandi
0 views • 11 slides
Mathematical Foundations for Computer Graphics: Geometry, Trigonometry, and Equations
This lecture covers essential mathematical tools for computer graphics, including 2D and 3D geometry, trigonometry, vector spaces, points, vectors, coordinates, linear transforms, matrices, complex numbers, and slope-intercept line equations. The content delves into concepts like angles, trigonometr
1 views • 53 slides
Soccer Player Techniques and Strategies for Success
Gain insights into effective soccer player outcomes and roles with detailed guidance on when to dribble, pass, intercept, turn, control, press, pass over distance, and shield the ball. Enhance your gameplay with tips on decision-making, positioning, and technique for a competitive edge on the field.
0 views • 10 slides
Understanding Linear Equations and Graphs
Exploring linear equations in slope-intercept form, the concept of slope, graphing techniques, and real-world applications. Learn about positive and negative slopes, horizontal and vertical lines, slope-intercept form, and interpreting graphs. Examples guide you through finding slope, graphing lines
0 views • 8 slides
History of Marine Recreational Fisheries Survey in US Virgin Islands
The Marine Recreational Fisheries Statistical Survey (MRFSS) program in the US Virgin Islands has a rich history dating back to the late 1970s. Initially conducted through personal interviews and later transitioned to telephone and intercept sampling methods, the program aimed to collect data on rec
0 views • 9 slides
Mathematical Problem-solving Challenges for Week 21
Engage in various mathematical challenges involving coin counting, ticket sales, algebraic expressions, and more. Solve problems on identifying the number of coins, selling baked goods, determining vegetable costs, and finding slope-intercept forms. Sharpen your math skills and enhance problem-solvi
1 views • 15 slides
Intercept X - Early Access Program Overview
Intercept X's Early Access Program offers advanced security solutions to combat active adversaries and advanced malware. The program covers deep learning techniques, false positive mitigations, and credential theft protection. It focuses on protecting against various threats such as credential theft
0 views • 14 slides
The Vital Role of Encryption in Safeguarding the Digital Economy
Encryption plays a crucial role in protecting the digital economy by providing secure communication channels. Professor Peter Swire from Ohio State University emphasizes the need for strong encryption over weak cybersecurity measures. He discusses the history of wiretaps, the shift to strong cryptog
0 views • 15 slides
The Intersection of Criminal Justice Reform and Medicaid Reform: Health Care as a Key Intercept to Recidivism
This study examines the integration of criminal justice reform (SB 91) and Medicaid/behavioral health redesign and reform (SB 74) in Alaska. It highlights the history of SB 91, the problems faced by the state's prison system, findings from data analysis, and the impact of SB 91 in reducing the inmat
1 views • 45 slides
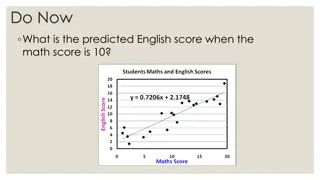
Understanding Regression Lines for Predicting English Scores
Learn how to utilize regression lines to predict English scores based on math scores, recognize the dangers of extrapolation, calculate and interpret residuals, and understand the significance of slope and y-intercept in regression analysis. Explore the process of making predictions using regression
0 views • 34 slides
Examples of Data Analysis Techniques and Linear Regression Models
In these examples, we explore data analysis techniques and linear regression models using scatter plots, linear functions, and residual calculations. We analyze the trends in recorded music sales, antibiotic levels in the body, and predicted values in a linear regression model. The concepts of slope
0 views • 11 slides
Quadratic Functions and Models: Characteristics and Equations
Explore writing quadratic functions given specific characteristics such as vertices, x-intercepts, and points passed through. Learn how to form equations in vertex form, intercept form, and standard form by plugging in values and solving systems of equations. Practice creating quadratic functions wi
0 views • 8 slides
Linear Function Modeling in Snowy Tree Cricket Chirp Rates
Based on the book "Functions, Data, and Models" by S.P. Gordon and F.S. Gordon, this presentation discusses how to model the chirp rate of snowy tree crickets in relation to temperature using linear functions. It covers finding the linear function, interpreting the slope and intercept, determining d
0 views • 13 slides
Pre-Algebra PSSA Practice Test Slides and Rainfall Measurement Analysis
In this content, you will find a series of slides for a PSSA practice test in Pre-Algebra. Additionally, it includes a scenario where Bill measures rainfall using a rain gauge, requiring analysis of rainfall data and the creation of a slope-intercept equation. The scenario also asks to interpret the
0 views • 16 slides
Understanding Linear Equations and Relationships
Explore various questions related to linear equations, slopes, y-intercepts, proportional relationships, and unit rates with step-by-step solutions and explanations. Practice identifying linear functions and graphing equations through real-life scenarios. Enhance your understanding of slope-intercep
0 views • 16 slides
Understanding Functional Form Fitting in Data Analysis
Explore the intricacies of fitting different functional forms to data sets, considering error bars and weight factors. The analysis covers fitting to various models such as A=a+bT, A=a/(1+bT), 1/A=a+bT, 1/A=a+BT, fitting ln(A)=1+bT, and flipping axes to handle thickness errors more effectively. Key
0 views • 14 slides
Intercept X Early Access Program: Sophos Tester Overview
The Intercept X Early Access Program encompasses the Sophos Tester, a tool designed by Karl Ackerman, Principal Product Manager of Endpoint Security Group, in July 2017. This tool allows users to demonstrate attack techniques without harming their PCs. It is safe to use and functions with Intercept
0 views • 16 slides
Understanding Lawful Bases in AI Data Processing
Explore the importance of identifying lawful bases when utilizing AI, considerations for statistical accuracy, addressing bias and discrimination risks, and ensuring transparency in AI processes. Discover guidance from the ICO and The Alan Turing Institute on explaining decisions made with AI, and l
0 views • 18 slides
Evolution of Surveillance in Cloud Computing
Delve into the historical progression of surveillance in cloud computing, from the era of lawful intercept agencies pressuring the internet community to weaken its tech to the modern landscape where mobile devices dominate traffic, leading to new challenges and solutions in protecting data privacy a
0 views • 33 slides
Cyber Security Engineering: Understanding the Importance and Examples
Cyber security is crucial due to the uncontrollable nature of digital devices and the potential for unauthorized access and manipulation, leading to severe consequences like data leakage, information distortion, and unauthorized access. Two examples illustrate the real-world implications of cyber th
0 views • 20 slides
Understanding Random Slopes in Data Analysis
Exploring the impact of grand-mean and group-mean centering on intercept interpretation with random slopes, as well as variations in slope/intercept covariance. Differentiating between fixed and random coefficients, and the effects of adding group mean as a Level 2 variable. Delving into within vs.
0 views • 21 slides
Effective Strategies for Justice-Involved Individuals with Mental and Substance Use Disorders
The Sequential Intercept Model outlines various effective strategies at different intercept points to support individuals with mental and substance use disorders involved in the justice system. These strategies include cross-system collaboration, routine identification of individuals with disorders,
0 views • 12 slides
Cisco Architecture for Lawful Intercept in IP Networks
This document outlines Cisco's architecture for supporting lawful intercept in IP networks, detailing a general solution with common interfaces for monitoring telecommunication networks by law enforcement agencies worldwide.
0 views • 9 slides
Ensuring a Lawful Workplace in Hospitality Management
This chapter emphasizes the importance of understanding and complying with laws that impact restaurant and foodservice operations. It covers federal, state, and local employment laws, legal aspects of food safety and serving alcohol, as well as procedures to protect the operation from legal actions.
0 views • 36 slides
Guide to Process Children's Personal Data Under GDPR
Explore steps such as reading guides, conducting an information audit, identifying risks, and understanding lawful bases for processing children's personal data under GDPR. Consider Data Protection Impact Assessments and lawful bases like consent, contract performance, legal obligations, vital inter
0 views • 24 slides
Understanding Transit Survey Methods for Data Collection
Explore the various types of surveys used in transit systems, including longitudinal, cross-sectional, and single-point surveys. Learn about different survey modes such as on-board/intercept, telephone, mail, web-based, and smartphones. Understand the advantages and limitations of each survey method
0 views • 32 slides
MitM Attack by Name Collision: Implications and Vulnerability Assessment
In this research study, the authors delve into the risks and vulnerabilities associated with Man-in-the-Middle (MitM) attacks exploiting name collision in the era of new generic Top-Level Domains (gTLDs). The study highlights how attackers can intercept web traffic by manipulating vulnerable domains
0 views • 25 slides
Exploring Equations in Two Variables
Explore the creation and graphing of linear equations in two variables to represent relationships between quantities. Understand the concept of slope, y-intercept, and the slope-intercept form of equations. Practice creating tables of values, writing algebraic equations, and graphing on coordinate a
0 views • 22 slides