Implementing Red Hat Identity Management (IPA) for Improved Identity Management and Access Control
Discover how BNL addressed challenges with individual Kerberos realms by migrating to Red Hat Identity Management (IPA) for streamlined SSO and federated access. Learn about the benefits of IPA architecture, user migration from OpenLDAP, and the successful implementation of IPA in a production envir
2 views • 14 slides
Secure Usage of Kibana & ElasticSearch in Multi-User Environments
Developments in access control for Kibana and ElasticSearch to address the lack of native access restrictions, with solutions based on CERN's and alternative Kerberos SSO integration methods, enabling user-specific filters and dashboard separation.
0 views • 23 slides
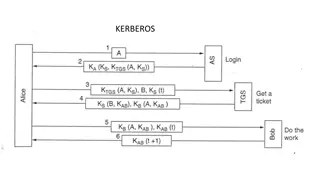
Understanding Kerberos Authentication in Network Security
Kerberos is a trusted authentication service for establishing secure communication between clients and servers in a distributed environment. Developed at MIT, it addresses threats like user impersonation and eavesdropping by providing centralized authentication. Kerberos relies on symmetric encrypti
0 views • 13 slides
Understanding Kerberos Authentication Protocol
Kerberos is a secure authentication protocol developed at M.I.T. to allow workstation users to access network resources securely. It involves three servers: Authentication Server (AS), Ticket-Granting Server (TGS), and the server performing the requested tasks. The AS verifies users, TGS issues tick
0 views • 12 slides
Practical Aspects of Modern Cryptography: November 2016
Exploring session-based protocols, SSL/TLS, certificates, and public key infrastructure, this presentation delves into the motivation behind secure online interactions, discussing the importance of verifying identities, ensuring data confidentiality, maintaining message integrity, and authenticating
0 views • 137 slides