Decoding the Impact: Techno-Economic Analysis Unveiled
Delve into the crucial role of Techno-Economic Analysis in understanding the true significance of innovations and implementations. Learn how this process shapes decisions by evaluating both technological feasibility and economic viability together.
2 views • 13 slides
Conjunctive Searchable Symmetric Encryption From Hard Lattices
Discusses outsourcing storage and computing, encrypted data computing, and searchable symmetric encryption for data security in cloud environments. It touches on topics like data confidentiality, user revocation, and performance-oriented implementations.
2 views • 30 slides
Digital Techniques (22320)
This digital techniques course covers topics such as number systems, logic circuits, combinational and sequential circuits, as well as practical implementations and microprojects. The examination scheme includes theory and practical components. Reference books are also provided for further learning.
3 views • 8 slides
In-Depth Look at Breaking HTTP Servers, Proxies, and Load Balancers
Explore the world of disrupting HTTP technology with authors Ben Kallus and Prashant Anantharaman. Delve into vulnerabilities, DARPA-funded projects, and the interesting exploits in HTTP implementations. Witness the journey that involves discovering multiple vulnerabilities, receiving grants for res
2 views • 51 slides
Understanding Ministerial Public Juridic Persons in Church Law
Ministerial Public Juridic Persons (MPJPs) are legal entities within Canon or Church Law established for specific purposes with designated individuals representing them. They play a crucial role in stewarding ministries and connecting them directly to the Church. The emergence of MPJPs reflects Vati
0 views • 22 slides
Catholic Diocesan Vision Update and Parish Development Strategy
The Diocesan Vision Update for October 2023 outlines a mission to fulfill the trust of Jesus Christ through vibrant communities of missionary disciples. Archbishop Bernard Longley leads the charge towards co-responsibility and joyful service. Feedback from the Synod 2023 points to progress in discer
1 views • 12 slides
Understanding Lists, Stacks, and Queues in Abstract Data Types
Explore the concepts of Abstract Data Types (ADT) related to lists, stacks, and queues. Learn about ADT definition, high-level data types, operations, iterators, and their implementations. Delve into the significance of iterators for navigating different data structures efficiently.
3 views • 21 slides
OBPMark and OBPMark-ML: Computational Benchmarks for Space Applications
OBPMark and OBPMark-ML are computational benchmarks developed by ESA and BSC/UPC for on-board data processing and machine learning in space applications. These benchmarks aim to standardize performance comparison across different processing devices, identify key parameters, and provide recommendatio
10 views • 20 slides
Infusing Intellectual and Developmental Disability Curriculum in Medical School
This presentation highlights the integration of an Intellectual and Developmental Disability (IDD) curriculum in medical schools, emphasizing the importance of addressing healthcare disparities. The curriculum evolution, including grants and remote implementations due to the COVID-19 pandemic, is di
6 views • 6 slides
Case Studies on Successful Revenue Technology Implementations in Cargo Services (1)
In the fast-paced world of cargo services, optimizing pricing strategies remains a pivotal challenge for businesses aiming to boost profitability and maintain competitive advantage. Revenue technology, specifically tools that enable dynamic and cargo pricing, has revolutionized how companies approac
2 views • 5 slides
LINKED LIST.MODULE 3
Explore the concept of linked lists, a linear collection of data elements represented as nodes with information and addresses to the next node. Learn about implementations, traversing, and searching algorithms in linked lists with detailed explanations and visuals.
1 views • 41 slides
Database System Concurrency Control and Transactions Overview
Studying relational models, SQL, database system architecture, operator implementations, data layouts, and query optimization laid the foundation for advanced topics like Concurrency Control and Recovery. Discover how transactions group related actions, ACID properties ensure data integrity, and the
0 views • 57 slides
Evaluation of DryadLINQ for Scientific Analyses
DryadLINQ was evaluated for scientific analyses in the context of developing and comparing various scientific applications with similar MapReduce implementations. The study aimed to assess the usability of DryadLINQ, create scientific applications utilizing it, and analyze their performance against
0 views • 20 slides
Hands-on Machine Learning with Python: Implement Neural Network Solutions
Explore machine learning concepts from Python basics to advanced neural network implementations using Scikit-learn and PyTorch. This comprehensive guide provides step-by-step explanations, code examples, and practical insights for beginners in the field. Covering topics such as data visualization, N
2 views • 13 slides
A Comprehensive Overview of ATS STEM Framework for Teachers
Explore the ATS STEM framework for teachers, focusing on key principles like problem-solving design, disciplinary knowledge, and integrated STEM practices. Discover how to incorporate transversal competencies and formative assessments into STEM education, supported by real-world contexts and appropr
0 views • 76 slides
STM32WB BLE SW Application Sequencer Architecture Overview
The STM32WB BLE SW Application Sequencer is a specialized framework that optimizes while loop bare-metal implementations to avoid race conditions, especially in low power modes. It is not intended to compete with standard operating systems but rather with bare-metal implementations. The sequencer al
2 views • 14 slides
Understanding Synthetic Aperture Radar (SAR) Modes and Implementations
Explore the world of Synthetic Aperture Radar (SAR) through various modes and implementations, covering topics such as SAR coordinate systems, pulse compression, range-Doppler algorithms, Born approximation, SAR scene simulation, and more. Dive into the distinctions between unfocused SAR and focused
0 views • 18 slides
Understanding Priority Queues and Heap Data Structures
Priority queues play a key role in computer science algorithms by managing data based on priority levels. The use of heap data structures enhances the efficiency of priority queue operations. This tutorial covers the basics of priority queues, their applications, different implementations such as li
0 views • 30 slides
Priority Queues in Java: Implementation and Use Cases
Explore the concept of priority queues in Java, covering implementations using unsorted and sorted linked lists, as well as heaps. Learn about the differences between a queue and a priority queue through reading quizzes and discover various priority queue implementation options. Dive into priority q
1 views • 42 slides
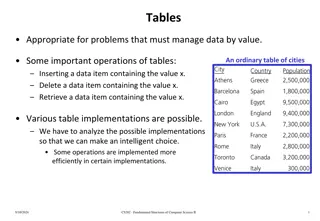
Implementations and Operations of Tables for Managing Data
An analysis of different table implementations for managing data by value, discussing operations like insertion, deletion, and retrieval. The post explores various linear and nonlinear implementations such as sorted arrays, linked lists, and binary search trees, highlighting the importance of select
0 views • 54 slides
Array Indices: Starting at 0 or 1?
The debate over whether array indices should start at 0 or 1 continues. A compromise of 0.5 was rejected, leading to discussions on JavaScript syntax, function definitions, and iterator implementations in programming. Explore the intricacies of array indexing and programming practices.
1 views • 19 slides
Priority Queues: Operations and Implementations
Priority queues are data structures that allow efficient insertion, deletion, and retrieval of elements based on their priority. This information-rich content covers various aspects of priority queues, including ideal times, binomial queues, Dijkstra's algorithm for single-source shortest paths, and
0 views • 11 slides
Understanding Priority Queues and Heaps in CSE 373 Lecture
Today's lecture in CSE 373 covers the Priority Queue Abstract Data Type (ADT), the properties of heaps, and their implementations. Key topics include the completeness property of heaps, different priority queue implementations such as the binary search tree for faster insert and find operations, and
0 views • 21 slides
Enhancing 3DIC Implementations with Mix-and-Match Die Stacking
This study by Kwangsoo Han, Andrew B. Kahng, and Jiajia Li delves into the improved performance of 3DIC implementations through the mix-and-match die stacking technique. By integrating slow and fast tiers, they aim to enhance parametric yield and optimize design-stage processes for a more efficient
0 views • 19 slides
Understanding Queues in Computer Science: Principles and Implementations
Explore the concept of queues in computer science, focusing on ordered collections of data following the FIFO principle. Learn about queue ADTs, implementations in Python, and delve into a simulation of a Printer Queue problem. Discover how to model printing tasks as random events and analyze the im
0 views • 15 slides
Understanding DNS Flag Day and EDNS: A Comprehensive Overview
DNS Flag Day marks a coordinated effort to remove workarounds in DNS implementations, impacting domains in various ccTLDs like .CL, .CZ, .SE, .NU, and .NZ. Enhanced DNS (EDNS) provides a mechanism for supporting new options, but issues arise from poor DNS implementations causing delays and hindering
0 views • 20 slides
Understanding ADT List Operations and Implementations
In this detailed content, you will learn about the specifications and operations involved in working with an ADT list. The structure, domain operations, and user instructions are clearly outlined for efficient implementation. The content also delves into the representation and implementation aspects
0 views • 30 slides
Understanding Python Iterators and Generators
Exploring the concepts of iterators and generators in Python, including how to iterate through elements, utilize generator expressions, and measure memory usage. See examples of iterable objects, iterator usage, and the central role of iterators in for loops. Additionally, learn about changing and e
0 views • 30 slides
Efficient Snapshot Implementations in Distributed Systems
This content discusses various snapshot implementations in distributed systems, focusing on achieving faster and sub-linear snapshot complexity. It covers topics such as multi-writer registers, tree structures, polylogarithmic snapshots, and the challenges of ensuring consistency across processes. T
0 views • 16 slides
PacketGuardian: A Tool for Static Detection of Packet Injection Vulnerabilities
This research paper introduces PacketGuardian, an effective static analysis tool designed to evaluate the robustness of protocol implementations against packet injection attacks. This tool supports precise context, flow, field-sensitive taint analysis, implicit flow analysis, and employs a summary-b
0 views • 23 slides
Practical Implementations of Arithmetic Coding
Explore the practical implementations, advantages, and disadvantages of arithmetic coding in this informative guide. Learn about the basic algorithm, dynamic interval expansion, integer arithmetic coding, and methods to improve the speed of arithmetic coding. Dive deep into encoding algorithms, exam
0 views • 78 slides
Understanding Queues: Operations, Implementations, and Applications
Explore the world of queues, a fundamental data structure with operations like enqueue and dequeue, and implementations using arrays or linked lists. Dive into the applications of queues and their significance in various scenarios. Uncover the basics of queue operations and their practical implicati
0 views • 30 slides
AI-Based Compression and Understanding of Industrial Data (MPAI-CUI) - Company Performance Prediction Use Case
AI-based Compression and Understanding of Industrial Data (MPAI-CUI) is a standard developed by the MPEG standards group. This standard focuses on transforming data into a more suitable format for applications. The presentation will cover the introduction to MPAI, applications, a demo for anonymous
0 views • 25 slides
Understanding ADTs: Lists, Stacks, and Queues - Implementation and Operations
Explore the world of Abstract Data Types (ADTs) - Lists, Stacks, and Queues, focusing on their operations like adding, removing, and accessing elements. Learn the differences between array and linked list implementations, along with insights on how to manipulate data structure implementations. Dive
0 views • 18 slides
High Performance User-Level Sockets over Gigabit Ethernet
Presentation overview of the design challenges, performance enhancement techniques, and results related to implementing high-performance user-level sockets over Gigabit Ethernet networks. The background and motivation discuss the limitations of traditional kernel-based implementations and the need f
1 views • 34 slides
Overview of HERDOS TES and SNiPER TES
HERDOS TES and SNiPER TES are discussed in detail, outlining their implementations and distinctive features. The discussion includes insights on TES requirements, concrete implementations, DataBuffer usage, HERD TES reliance on podio, and the migration plan to podio
0 views • 10 slides
Java Peer Instruction Materials Review
Materials by Cynthia Lee under a Creative Commons License discussing Java concepts such as Iterator design pattern, composition vs. inheritance, legality of certain code snippets, and clarity on the accessibility of public and protected class elements to clients. Additionally, a step towards using J
0 views • 34 slides
Exploring Web Services at IRIS: Implementations and Coordination
Discover the world of web services at IRIS through a detailed exploration of implementations, international coordination efforts, and the team behind these endeavors. Learn about the definition of web services, practical examples, and the various data and processing services offered by IRIS to suppo
0 views • 24 slides
Understanding Noise*: A Verified Secure Channel Protocol Library
Explore Noise*, a library of high-performance secure channel protocol implementations that have been verified for correctness. The Noise protocol examples, such as IKpsk2, showcase key exchange patterns used in applications like WhatsApp and Wireguard VPN. Discover the importance of verified impleme
0 views • 18 slides
Coverage-Directed Differential Testing of JVM Implementations
The paper discusses the importance of coverage-directed differential testing for Java Virtual Machine (JVM) implementations. It covers challenges in identifying JVM defects, solutions using test oracles, and examples of JVM behavior discrepancies. The study emphasizes the need for obtaining test cla
0 views • 45 slides