Understanding Malicious Attacks, Threats, and Vulnerabilities in IT Security
Malicious attacks, threats, and vulnerabilities in IT systems pose significant risks and damages. This chapter explores the types of attacks, tools used, security breaches, and measures to protect against cyber threats. Learn how security professionals safeguard organizations from malicious attacks
0 views • 24 slides
TEAM SWOT ANALYSIS
This comprehensive presentation template guides individuals or small groups through conducting a SWOT analysis to identify strengths, weaknesses, opportunities, and threats for a business. It includes questions to assess strengths, weaknesses, opportunities, and threats, a discussion section to dete
1 views • 8 slides
Artificial Intelligence in Cyber Security: Enhancing Threat Detection and Response
Artificial Intelligence (AI) is revolutionizing cyber security by enhancing threat detection, response, and prevention capabilities. By leveraging machine learning algorithms, AI enables organizations to identify cyber threats, analyze behavioral patterns, automate incident response, adapt to evolvi
1 views • 33 slides
Comprehensive Digital Risk Assessment Guide for Businesses
Conducting a digital risk assessment is vital for securing your business against threats like viruses, malware, hackers, and human errors. This guide outlines key areas to focus on, such as identifying critical assets, assessing potential impacts of breaches, prioritizing threats, utilizing tools li
3 views • 4 slides
To be or not to be – ‘insider/outsider positionality’: Methodological challenges in researching a group of Iraqi Kurdish migrants in the UK.
Research by Chra R. Mahmud explores the methodological challenges in studying Iraqi Kurdish migrants in the UK, focusing on insider-outsider positionality. The study delves into the lived experiences of this group, examining the researcher's status and identity negotiation during the research proces
0 views • 18 slides
Understanding Threats in Distribution Integrity Management Program
Distribution Integrity Management Program (DIMP) focuses on ensuring the integrity of pipelines by understanding and managing various threats. Operators are responsible for identifying, categorizing, and addressing potential threats such as corrosion, natural forces, excavation damage, and more to p
1 views • 39 slides
Insider Tips for Getting Your Overseas Education Loan Approved Quickly
For swift approval of your overseas education loan, research lenders thoroughly and compile a robust application. Consider a co-signer to bolster your credibility, showcase financial stability, and maintain clear communication with lenders. These insider tips streamline the loan approval process. To
1 views • 7 slides
Healthcare Executive's Guide to Ransomware Threats
This comprehensive guide covers essential information on ransomware threats in healthcare, including the definition of ransomware, how it works, email and network threats, and statistics. Gain insights from Troy Ament, a seasoned CISO in the healthcare sector, to safeguard your organization against
0 views • 17 slides
Insider Tips for Clinical Internship Success
Learn insider tips from experienced presenters on maximizing your success in applying for clinical internships. Gain valuable insights and strategies to enhance your chances of securing a placement.
0 views • 49 slides
Comprehensive Overview of Wharton Research Data Services for Insider Trading Analysis
Wharton Research Data Services (WRDS) offers a detailed and comprehensive coverage for insider trading analysis, executive compensation, and various transactional data. The platform compares favorably with competitors like 2iQ and Thomson Reuters, providing in-depth insights into various aspects suc
0 views • 17 slides
Cyber Threats and Security Controls Analysis for Urban Air Mobility Environments
The Urban Air Mobility (UAM) environment, with its service-oriented architecture, faces various cyber threats related to end-users, cyber-physical systems, cloud services, and on-premise computing. Threats include unauthorized interception of data, phishing attacks, and Denial of Service (DoS) incid
1 views • 9 slides
Understanding Hybrid Threats and Resilience through Civil Preparedness
Exploring the concept of hybrid threats that combine external threats and internal vulnerabilities, this academic viewpoint by Ramon Loik emphasizes the importance of civil preparedness in building resilience against crises. It delves into aspects such as target selection, active influencing, and th
0 views • 11 slides
Insider's Guide to NIH Peer Review for Reviewers by Richard Kitsis, M.D.
This insider's guide provides valuable insights for reviewers participating in NIH grant application peer reviews. It covers essential aspects such as staying grounded, getting started, writing reviews effectively, scoring applications, participating in meetings, and enjoying the overall experience.
0 views • 12 slides
Challenges in Security Analysis of Advanced Reactors
Analyzing the security aspects of advanced reactors involves considerations such as physical protection, facility sabotage, nuclear terrorism, cyber vulnerabilities, and emerging technologies. Highlighted risks include the need to protect nuclear material, insider threats, terrorist attacks causing
0 views • 8 slides
Understanding Adversarial Threats in Machine Learning
This document explores the world of adversarial threats in machine learning, covering topics such as attack nomenclature, dimensions in adversarial learning, influence dimension, causative and exploratory approaches in attacks, and more. It delves into how adversaries manipulate data or models to co
0 views • 10 slides
Overview of Insider Trading Laws and Notorious Cases
Insider trading, involving the trading of securities based on confidential information, is prohibited under various statutes such as Section 10(b) of the Securities Exchange Act of 1934 and SEC Rule 10b-5. The Insider Trading Sanctions Act of 1984 and the Insider Trading and Fraud Act of 1988 provid
0 views • 24 slides
Understanding Cyber Threats and the Role of Defenders in Organizations
Explore the world of cyber threats, including phishing, malware, and data breaches, and understand the importance of being a defender in your organization. Learn about key security mechanics, evolving threats, and the essential role of human vigilance in cybersecurity.
0 views • 17 slides
Essential Tips for Protecting Your Computer from Cyber Threats
Protecting your computer from cyber threats is crucial in today's interconnected world. By installing and regularly updating antivirus software, you can enhance your computer's security and safeguard your data from malicious attacks. Choose the right antivirus software based on recommendations, feat
0 views • 28 slides
Conservation Efforts and Threats to Biodiversity at Nolde Forest
Nolde Forest State Park, established by hosiery baron Jacob Nolde in the early 1900s, is a lush coniferous forest now dedicated to environmental education. The park faces threats to biodiversity such as natural disasters, invasive species, and human activity. Hurricane Sandy's impact in 2012 and the
2 views • 13 slides
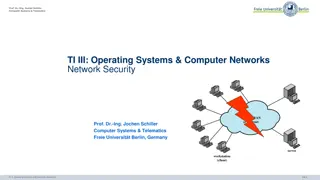
Understanding Network Security Threats and Goals in Computer Systems
Explore the concept of threats in communication networks, including examples of attacks such as hacking and data disclosure. Learn about key security goals like confidentiality, data integrity, accountability, availability, and controlled access. Discover technically defined threats like masquerade,
0 views • 32 slides
Understanding Internet Threat Landscape and Countermeasures
Delve into the complexities of identifying and mitigating threats in cyberspace at scale. Explore the challenges of detecting malicious activities, the need for broad-based blocklists, and the importance of tracking provider abuse percentages. Learn about the Pwnage Cycle, ICANN's efforts in measuri
0 views • 32 slides
Coastal Challenges: Threats and Uses Analysis
The Year 9 Geography homework booklet focuses on the topic of coasts, emphasizing grid references and mapping skills. Students are tasked with identifying grid references for shapes, drawing specific shapes on grids, and demonstrating understanding of 4 and 6 figure grid references. Additionally, in
0 views • 13 slides
Understanding Security Threats and Countermeasures
Explore the diverse threats posed by attackers in the information security landscape, ranging from employee sabotage to hacking incidents. Learn about fundamental security terminology, types of security compromises, and countermeasure strategies to prevent, detect, and correct security breaches. Gai
0 views • 32 slides
Understanding Security Threats and Vulnerabilities in Computer Systems
In computer security, threats exploit vulnerabilities to breach security and cause harm. Vulnerabilities arise from system weaknesses, attacker access, and capability. Threats include spoofing, data tampering, repudiation, information disclosure, denial of service, and elevation of privilege. Catego
0 views • 13 slides
Insider's Guide to Public Records: Unveiling Past vs. Present Trends
Explore the evolving landscape of public records through an insider's lens, covering topics such as state vs. federal laws, processing complex requests, and the importance of training. Discover the significance of transparency in public records requests, the shift towards digital records, and the im
0 views • 32 slides
IPv6 Security and Threats Workshop Summary
David Kelsey from STFC-RAL presented on IPv6 security and threats at the IPv6 workshop pre-GDB at CERN in June 2016. The workshop covered topics such as IPv6 protocol attacks, issues for site network security teams and sys admins, new features of IPv6, security pros and cons, immediate IPv6 concerns
0 views • 29 slides
Mobile Issues and Cyber Threats in Nigeria - Presentation by Dr. J.O. Atoyebi, NCC
Evolution of GSM in Nigeria, the impact of mobile phone deregulation, and the rise of cyber threats highlighted in a presentation by Dr. J.O. Atoyebi of the Nigerian Communications Commission. The report reveals Nigeria's position in global internet security threats and the challenges faced by the c
0 views • 7 slides
Understanding Computer Threats and Security Measures
Computer threats are constantly evolving, posing risks such as unauthorized access, data manipulation, and cyber-attacks. This chapter discusses various types of threats to users, hardware, and data security measures to mitigate these risks. Learn about identity theft, malware, cyber terrorism, and
0 views • 21 slides
Recognizing and Preventing Insider Threats in National Security
Insider threats pose a significant risk to national security and industry, involving individuals using authorized access to carry out harmful actions. This content covers the definition of insider threats, indicators, consequences, and ways to recognize and report suspicious behaviors. It emphasizes
0 views • 15 slides
Understanding Threat Assessment in Conservation: Direct, Stress, and Indirect Threats
Within threat assessment for conservation, different types of threats are identified and categorized, including direct threats which are human-induced actions directly affecting conservation targets, stressors which result from biophysical impacts of actions on targets, and indirect threats contribu
0 views • 24 slides
Understanding Cyber Threats in Today's Digital Landscape
Cyberspace is a vast realm encompassing the Internet, where we engage in various activities ranging from communication to entertainment. With the majority of children exposed to the online world, cybersecurity awareness is crucial to tackle the rising cyber threats. These threats include job frauds,
0 views • 33 slides
Understanding WHARTON Research Data Services Insiders Database
WHARTON Research Data Services (WRDS) Insiders Database covers insider transactions from June 30, 2003, sourced from SEC Form 3, 4, and 5 filings. The database is structured into six distinct datasets, providing comprehensive coverage on insider trades and related information. It includes details on
0 views • 15 slides
Insider's Guide to Management Consulting: Application, Interviews, and Networking Tips
Get an insider's scoop on the world of management consulting with tips on applications, interview preparation, and networking strategies. Learn about the purpose of the St. Olaf Management Consulting Group, application requirements, resume writing, networking essentials, interview processes, and cra
0 views • 21 slides
Non-Interactive Anonymous Router with Quasi-Linear Computation
Explore the concept of a Non-Interactive Anonymous Router with Quasi-Linear Computation, Receiver Insider Protection (RIP), Sender Insider Protection (SIP), and Multi-Client Functional Encryption. The comparison of anonymity notions in NIAR and the motivation behind the non-interactive anonymous shu
0 views • 29 slides
Understanding Experiments and Threats to Validity
Explore the world of experimental research, internal and external validity, threats to validity, and the importance of proper study design in ensuring the credibility of research results. Learn about confounding variables, threats to internal validity such as environmental factors and group comparis
0 views • 15 slides
Headhunters Recruitment_ The Insider’s Guide to Getting Hired in 2023
Unlock career success with Headhunters Recruitment: Your essential 2023 guide to insider tips for a successful hiring journey. Explore expert advice now!
0 views • 7 slides
Understanding Insider Trading: The Case of Rajat K. Gupta and Raj Rajaratnam
The story delves into the scandal of insider trading involving Rajat K. Gupta and Raj Rajaratnam. Gupta, a prominent figure at Goldman Sachs, allegedly leaked confidential information to Rajaratnam, who made substantial profits through illegal trading activities. This case not only tarnished Gupta's
0 views • 8 slides
Navigating Current and Emerging Cyber Threats: Leadership Insights
Delve into the realm of current and emerging cyber threats with a focus on leadership considerations. Understand the evolving landscape of cyber risks, the importance of cyber expertise in leadership planning, and the essential role of cybersecurity in today's digital world. Explore the various thre
0 views • 16 slides
Understanding Threats and Attacks in Information Systems
Threats and attacks pose risks to information systems through vulnerabilities that can be exploited, leading to data loss, system unavailability, and compromised security. Four primary classes of threats include unstructured threats from inexperienced individuals, structured threats from skilled hac
0 views • 21 slides
Comparison of Traditional and Cyber Threat Assessment Methodologies
In the digital age, understanding cyber threats alongside traditional threats is crucial. Cyber adversaries operate globally and are hard to identify, posing challenges for intelligence agencies. The ease of acquiring cyber skills and resources makes cyber threats dynamic and dangerous. Classical cy
0 views • 17 slides