Principles of Cyber Security
Threat actors prioritize targeting networks to exploit vulnerabilities, leading to various attacks such as interception, DNS attacks, and MITM attacks. MITM attacks involve eavesdropping on communications or impersonating parties, with techniques like session replay to steal credentials. Implementin
0 views • 7 slides
Security Breach: Detecting and Exploiting SQL Injection in Contact Groups
Suspect a potential SQL injection in the macros used in Contact groups? Learn how to identify and exploit it through blind SQL injection techniques. Follow step-by-step instructions to execute a payload that alters user data and gain unauthorized access. Stay vigilant and proactively safeguard your
3 views • 27 slides
Understanding Bacterial Pathogenesis: Key Concepts and Factors
Bacterial pathogenesis involves the ability of certain bacteria to cause disease by attributes such as transmissibility, adherence, motility, invasion, and toxigenicity. Pathogens can exploit host defenses, while virulence determines the severity of infection. Learn about opportunistic pathogens, no
7 views • 36 slides
Understanding and Preventing Scams: A Comprehensive Guide
Scams can affect anyone, with victims often being over 55 years old. Organized criminals utilize various techniques such as befriending, grooming, and manipulation to exploit individuals. Common scams include identity theft, email scams, and fake job adverts. It's crucial to remain vigilant, never g
1 views • 11 slides
Understanding Balance of Power Theory in Global Politics
Balance of Power Theory in global politics emphasizes the distribution of military capability among states to prevent hegemony and maintain national security. It is a realist theory that highlights the importance of preventing any single state from dominating others. The theory discusses how stronge
0 views • 15 slides
The Algerian War and Decolonization in Modern France
The Algerian War of Independence (1954-1962) marked a significant chapter in modern French history, leading to the decolonization of Algeria. The conflict involved brutal tactics, mass expropriations, and human rights violations, as France sought to exploit Algeria for economic gain. The rule over A
6 views • 34 slides
Corporate Account Takeover & Information Security Awareness Presentation
Discover the threat of Corporate Account Takeover, a growing electronic crime, where cybercriminals utilize malware to fraudulently access and transfer funds from corporate online banking accounts. Learn about malware, types of transactions targeted, and how criminals exploit victims through various
1 views • 25 slides
Fundamentals of Ethical Hacking
Ethical hackers are often called \u201cwhite hats\u201d in contrast to \u201cblack hats,\u201d who are the malicious hackers. White hats use their skills to improve security and protect information, while black hats exploit vulnerabilities for illega
0 views • 1 slides
Understanding Futures Markets: Mechanism and Pricing Dynamics
Futures markets play a crucial role in price convergence between futures and spot prices of underlying assets. Traders can exploit arbitrage opportunities when the futures price deviates from the spot price during the delivery period. Settlement of futures contracts can be done through offsetting, d
2 views • 13 slides
Understanding Cyber Security and Risks
Cyber security, also known as IT security or computer security, is crucial for safeguarding information systems from theft, damage, and disruption. With the increasing connectivity of devices through the internet, the importance of cyber security cannot be overstated. Cyber risks encompass cyber cri
2 views • 24 slides
Understanding Network Denial of Service (DoS) Attacks
Network Denial of Service (DoS) attacks aim to disrupt services by overwhelming them with traffic. These attacks can occur at various layers of the network stack and exploit weaknesses to achieve their goal. Amplification attacks, such as the Smurf attack and DNS Amplification attack, can significan
2 views • 52 slides
Beware of the Grandparent Scam - Protect Yourself from Fraud
The Grandparent Scam is a prevalent form of fraud where scammers impersonate a grandchild in distress, seeking financial assistance. The criminals exploit emotions and pressure victims into sending money through various means. Learn how to spot and avoid falling victim to this scam to safeguard your
0 views • 9 slides
Romance Scams: A Growing Threat in Chesterfield
The Chesterfield Police Department investigated 45 reports of scams and frauds in 2020, resulting in over $1.5 million in losses. One prevalent scam discussed in the slides is Romance Scams, where suspects build fraudulent online relationships to exploit victims emotionally and financially. The susp
0 views • 9 slides
Understanding Penetration Testing Tactics and Techniques
In the realm of secure software engineering, penetration testing plays a crucial role in proactively identifying vulnerabilities. This involves delving deep to exploit potential weaknesses and simulate real-world attack scenarios. Skilled testers, both in-house and external, use frameworks like MITR
0 views • 16 slides
Carnegie Mellon Secure Systems Verification Research
Carnegie Mellon University's research focuses on secure hypervisor systems, address space separation, and verification tasks to ensure security properties in the presence of adversaries. Challenges include scalability in model checking due to complex data structures in address translation. The aim i
3 views • 20 slides
Limitations of Deep Learning in Adversarial Settings
Deep learning, particularly deep neural networks (DNNs), has revolutionized machine learning with its high accuracy rates. However, in adversarial settings, adversaries can manipulate DNNs by crafting adversarial samples to force misclassification. Such attacks pose risks in various applications, in
0 views • 38 slides
Understanding Exploit Development Fundamentals
Explore key concepts in exploit development, including vulnerabilities, exploits, 0days, memory management, instructions vs. data, and program address space. Learn about stack manipulation and how to take advantage of system flaws effectively.
0 views • 46 slides
Understanding Heap Overflows: An Introduction to Exploit Development
Learn about heap overflows in exploit development, including heap structure, memory maps, exploiting vulnerabilities, and controlling writes in the heap. Understand the difference between stack and heap, viewing heap in gdb, targeted exploit techniques, and the challenges of controlling EIP in the h
0 views • 17 slides
Introduction to Network Security Course
This network security course by Professor Christo Wilson covers fundamental security principles applicable to all systems, designing secure networked systems, understanding attacker mindsets, and respecting ethical boundaries in security research. The course aims to equip students with the ability t
0 views • 26 slides
Understanding BGP and DNS Worms in Network Security
Border Gateway Protocol (BGP) is crucial for network communication, allowing autonomous systems to exchange routing information. BGP works by announcing network ownership and directing traffic efficiently. However, BGP Blackhole attacks pose a threat, where malicious entities reroute traffic to disr
0 views • 37 slides
Understanding Low-Intensity DoS Attacks on BGP Infrastructure
Low-intensity Denial of Service (DoS) attacks present a new challenge in cyber warfare, blending in with regular traffic to target communication channels like HTTP, SMTP, and DNS. These attacks require multiple participating hosts to flood the target with useless packets, gradually overloading serve
0 views • 25 slides
Safely Logging Password-Derived Measurements for Web Login Systems
Design a secure measurement framework called Gossamer to assess risks associated with password-based measurements for web login systems. Explore ways to differentiate between benign and malicious traffic, and consider adding instrumentation to enhance security. Learn how attackers exploit password-d
0 views • 12 slides
Understanding Frame Pointer Attacks and Exploit Development with pwntools
Explore the concepts of frame pointer attacks, LD_PRELOAD usage, and exploit development with pwntools library. Discover how to spawn a shell using LD_PRELOAD or a constructor, along with the limitations and challenges associated with command-line exploitation.
0 views • 30 slides
Reflections on Wealth and Corruption in Monetary Worth
Reflecting on the theme of wealth and corruption, the series of images depict the consequences faced by the rich for their ill-gotten gains. Descriptions of riches corroded, garments moth-eaten, and treasures acquired through wrongful means serve as a stark reminder of the impending miseries awaitin
0 views • 18 slides
Understanding Security Threats and Vulnerabilities in Computer Systems
In computer security, threats exploit vulnerabilities to breach security and cause harm. Vulnerabilities arise from system weaknesses, attacker access, and capability. Threats include spoofing, data tampering, repudiation, information disclosure, denial of service, and elevation of privilege. Catego
0 views • 13 slides
Understanding Privilege Escalation in Windows and Linux Systems
Privilege escalation attacks are malicious tactics used by attackers to gain unauthorized access and elevated privileges in a system. These attacks exploit vulnerabilities in operating systems and web applications, allowing attackers to move deeper into a network to access high-value assets. This co
0 views • 28 slides
Statistical Dependencies in Sparse Representations: Exploitation & Applications
Explore how to exploit statistical dependencies in sparse representations through joint work by Michael Elad, Tomer Faktor, and Yonina Eldar. The research delves into practical pursuit algorithms using the Boltzmann Machine, highlighting motivations, basics, and practical steps for adaptive recovery
0 views • 47 slides
Intercept X Early Access Program: Sophos Tester Overview
The Intercept X Early Access Program encompasses the Sophos Tester, a tool designed by Karl Ackerman, Principal Product Manager of Endpoint Security Group, in July 2017. This tool allows users to demonstrate attack techniques without harming their PCs. It is safe to use and functions with Intercept
0 views • 16 slides
Understanding Human Trafficking: Definitions and Red Flags
This presentation covers the definitions of labor trafficking and sex trafficking, highlighting the methods used to exploit victims through force, coercion, and fraud. It also discusses potential red flags to identify individuals who may be victims of trafficking, such as living conditions, financia
0 views • 11 slides
Understanding Unix/Linux Hacking Techniques
Explore Unix/Linux hacking techniques including footprinting, scanning, enumeration, vulnerability mapping, remote access, data-driven attacks, buffer overflow, input validation, and countermeasures. Discover methods to gain root access, exploit vulnerabilities, perform brute force attacks, and secu
0 views • 6 slides
Transition to Post-Capitalism: Unconditional Citizen Income in Mexico
Unstoppable technology advancements in capitalism lead to the replacement of human labor, creating an insufficient wage-labor income link. The concept of an Objective Limit of Capitalism (OLC) suggests that the need to exploit human labor will diminish as science progresses, highlighting the necessi
0 views • 7 slides
Defending Against Cache-Based Side-Channel Attacks
The content discusses strategies to mitigate cache-based side-channel attacks, focusing on the importance of constant-time programming to avoid timing vulnerabilities. It covers topics such as microarchitectural attacks, cache structure, Prime+Probe attack, and the Bernstein attack on AES. Through d
0 views • 25 slides
Understanding Spectre and Meltdown Security Vulnerabilities
Spectre and Meltdown are two critical security vulnerabilities that exploit microarchitectural features to gain unauthorized access to memory. These vulnerabilities enable attackers to read memory that should be inaccessible, targeting branch prediction and exception handling mechanisms. Side channe
0 views • 19 slides
IEEE 802.11-19 Presentation on Strongest Tap FTM for PEDMG
Presentation on utilizing FTM measurements for the strongest arrival path in obstructed LOS scenarios, focusing on clock offset estimation, precise synchronization for wireless speakers, and positioning enhancement. The proposed method aims to exploit both best and first path information to localize
0 views • 15 slides
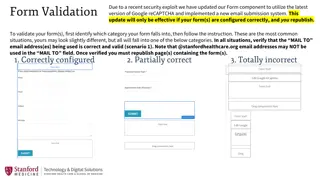
Form Component Security Update Instructions
In response to a security exploit, a new version of the Form component has been released with updated Google reCAPTCHA and email submission system. Follow the detailed instructions to validate and configure your forms correctly based on the identified categories - Correctly configured, Partially cor
0 views • 4 slides
Understanding Plant-Nematode Interaction: Defense Mechanisms and Parasitism
In the intricate relationship between plants and parasitic nematodes, plant defenses play a crucial role in combating biotrophic pathogens. The nematodes exploit various strategies to suppress these defenses and establish successful parasitism. The defense mechanisms of plants involve pre-existing b
0 views • 13 slides
Understanding Behavioral Asset Pricing: Factors Influencing Price and Return Expectations
Behavioral asset pricing models link investment asset returns with various factors such as risk, liquidity, and cognitive biases. This chapter delves into how features and characteristics influence the pricing of assets like cars and stocks, exploring the utilitarian, expressive, and emotional benef
0 views • 46 slides
Approximate Hardware Synthesis for Energy-Efficient Designs
The paper introduces an Approximate High-Level Synthesis (AHLS) approach for generating energy-optimized register-transfer-level hardware implementations from accurate high-level C descriptions. This approach considers joint precision and voltage scaling to maximize energy reductions while maintaini
0 views • 20 slides
Insight into Browser Instrumentation for Exploit Analysis
Explore the complex world of browser instrumentation and exploit analysis through the lens of Mihai Neagu's research at Bitdefender. Delve into the intricacies of exploit kits, malware delivery services, behavior analysis, and hidden aspects of exploit execution processes.
0 views • 19 slides
Understanding EternalBlue Exploit: History, Vulnerabilities, and Impact
EternalBlue is a notorious exploit developed by the NSA and leaked by the Shadow Brokers hacker group. It has been used in significant cyberattacks like WannaCry and NotPetya, targeting Windows systems through SMB protocol vulnerabilities. This exploit's impact and the various attacks it has been ut
0 views • 17 slides