Evolution and Plant Systematics Lecture Overview
This lecture outline delves into the concepts of evolution, unity, and diversity of organisms on Earth, covering topics such as fossils, Lamarck and Darwin's theories, adaptation, natural selection, artificial selection, Carolus Linnaeus' systematics, plant evolution, and the demonstration of evolut
5 views • 26 slides
Evolutionary Models in Molecular Biology
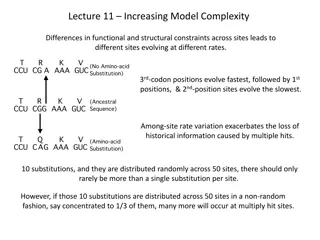
Differences in functional and structural constraints across sites lead to varying rates of evolution in molecular sequences. Understanding the complexities of site-specific rates, among-site rate variation, site-specific rates models, invariable sites model, and continuous methods is crucial for acc
6 views • 15 slides
Phylogenetic Status of Peripatus: Exploring its Systematic Position
Peripatus, known as claw bearers, exhibits characteristics of both annelids and arthropods, making it an intriguing species in the study of evolutionary biology. Considered as an intermediate link between these two phyla, Peripatus raises questions about its classification and evolutionary history.
0 views • 10 slides
Understanding Phylogeny and Evolution in Angiosperms
Phylogeny is the study of evolutionary relationships among organisms, depicted in phylogenetic trees based on shared characteristics. This overview delves into terms like homology, analogy, monophyly, and co-evolution in angiosperms with an emphasis on taxonomy, systematics, and the evolutionary his
1 views • 25 slides
Understanding Cladograms and Phylogenetic Analysis
Cladograms are used in cladistics to illustrate evolutionary relationships between organisms based on shared ancestral and derived characters. They are created by grouping species by common descent, forming clades that include an ancestral species and all its descendants. Valid clades are monophylet
0 views • 11 slides
Understanding Evolutionary Mechanisms: Natural Selection, Genetic Drift, and Gene Flow
Exploring the forces behind evolutionary change, this content delves into natural selection, genetic drift, and gene flow. Examples such as the bottleneck effect, founder effect, and Amish population polydactylism are presented to illustrate how these mechanisms shape genetic diversity. The impact o
0 views • 14 slides
Enhanced Security in Multiparty Computation
Explore the improved black-box constructions of composable secure computation, focusing on definitions, objectives, and the formalization basics of multiparty computation (MPC). Learn about the motivating security aspects in MPC and the real/ideal paradigm. Discover how MPC security involves compari
1 views • 68 slides
Evolutionary Insights of Basidiomycota Dikaryons
Basidiomycota, a successful fungal group with 30,000 known species, predominantly exhibits filamentous vegetative growth while also producing yeast forms. The multi-layered cell wall and regularly septate hyphae with dikaryotic mycelium are key characteristics. Recent experimentation on Schizophyllu
0 views • 20 slides
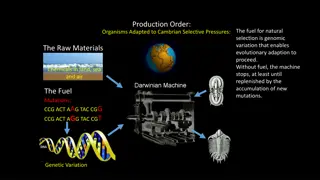
Insights into Evolutionary Adaptation and Genetic Variation
The production order highlights the essential role of genomic variation as fuel for natural selection, driving evolutionary adaptation. The Cambrian Explosion timeframe reveals a rapid increase in evolutionary adaptation, showcasing the appearance of diverse animal phyla over a relatively short peri
5 views • 6 slides
Secure Computation Techniques in RAM Models with Efficient Automation
Explore the automation of efficient RAM-model secure computation techniques, including examples such as secure binary search. Discover how traditional solutions using circuit abstractions can be improved for sub-linear time computation through methods like Oblivious RAM. Learn about techniques such
0 views • 37 slides
Secure Multiparty Computation for Department of Education Data Sharing
This report discusses the use of Secure Multiparty Computation (SMC) to enable sharing of sensitive Department of Education data across organizational boundaries. The application of SMC allows for joint computation while keeping individual data encrypted, ensuring privacy and security within the Nat
0 views • 15 slides
Advancements in Active Secure Multiparty Computation (MPC)
Delve into the realm of secure multiparty computation under 1-bit leakage, exploring the intersection of DP algorithms, MPC, and the utilization of leakage for enhanced performance. Discover the overhead implications of achieving active security, as well as the evolution of secure computation protoc
0 views • 43 slides
Computing Triplet and Quartet Distances Between Evolutionary Trees
Study on computing triplet and quartet distances in evolutionary trees, comparing rooted vs. unrooted, binary vs. arbitrary degree trees. Discusses algorithms, experimental results, and evolutionary tree construction methods. Includes analysis on cultural phylogenetics and evolutionary tree comparis
0 views • 27 slides
COMET: Code Offload by Migrating Execution - OSDI'12 Summary
The research paper discusses COMET, a system for transparently offloading computation from mobile devices to network resources to improve performance. It outlines the goals of COMET, its design, and evaluation, focusing on distributed shared memory and bridging computation disparity through offloadi
0 views • 31 slides
Actively Secure Arithmetic Computation and VOLE Study
Exploring actively secure arithmetic computation and VOLE with constant computational overhead at Tel Aviv University. Understanding how functions are represented in secure computation using arithmetic circuits over boolean circuits. Efficiently evaluating arithmetic circuits over large finite field
0 views • 36 slides
Enhancing Multi-Party Computation Efficiency Through ORAM Techniques
Explore the realm of efficient random access in multi-party computation through the reevaluation of classic schemes and the introduction of new approaches. Discover the potential of ORAM in improving performance and reducing costs in various computational tasks, such as secure multi-party computatio
0 views • 22 slides
Understanding Taxonomy and Classification in Biology
Scientists use classification to group organisms logically, making it easier to study life's diversity. Taxonomy assigns universally accepted names to organisms using binomial nomenclature. Carolus Linnaeus developed this system, organizing organisms into species, genus, family, order, class, phylum
0 views • 11 slides
Evolutionary Pioneers: Anning, Darwin, Wallace - Key Figures in Evolutionary Theory
Meet the evolutionary pioneers - Mary Anning, Charles Darwin, and Alfred Russel Wallace, who played crucial roles in the development of evolutionary theory. Learn about their groundbreaking discoveries, challenges faced, and lasting impact on the scientific community.
0 views • 7 slides
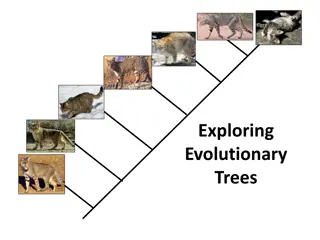
Exploring Evolutionary Trees and Family Lineages
Dive into the world of evolutionary trees and family lineages through captivating visuals and informative illustrations. Explore the relationships between species, understand genetic connections, and discover how traits evolve and spread through generations. From evolutionary history to family trees
0 views • 25 slides
Exploring Secure Computation in the Age of Information
Welcome to Secure Computation Lecture 1 by Arpita Patra. The course covers evaluation policies, projects, and references in the realm of secure computation. The content delves into the significance of information security across various sectors, emphasizing the importance of safeguarding sensitive d
0 views • 36 slides
Secure Two-Party Computation and Basic Secret-Sharing Concepts
In today's lecture of "Foundations of Cryptography," the focus is on secure two-party and multi-party computation, emphasizing semi-honest security where Alice and Bob must compute without revealing more than necessary. Concepts such as real-world vs. ideal-world scenarios, the existence of PPT simu
0 views • 27 slides
Linear Communication in Secure Multiparty Computation for Efficient and Fast Processing
The research focuses on achieving perfectly secure multiparty computation (MPC) with linear communication and constant expected time. It explores efficient approaches using a broadcast-hybrid model and P2P communication, aiming to balance speed and efficiency in MPC. The study highlights the importa
0 views • 23 slides
Evolutionary Computation and Genetic Algorithms Overview
Explore the world of evolutionary computation and genetic algorithms through a presentation outlining the concepts of genetic algorithms, parallel genetic algorithms, genetic programming, evolution strategies, classifier systems, and evolution programming. Delve into scenarios in the forest where gi
0 views • 51 slides
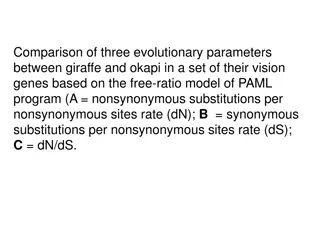
Comparative Analysis of Evolutionary Parameters in Giraffe and Okapi Vision Genes
This presentation compares three evolutionary parameters (dN, dS, dN/dS) between giraffe and okapi in a set of vision genes using the free-ratio model of the PAML program. The images illustrate the differences in nonsynonymous and synonymous substitutions, as well as the ratio of nonsynonymous to sy
0 views • 4 slides
Understanding Aggression: Exploring Its Evolutionary Roots
Delve into the complexities of human aggression, questioning whether it is inherent or a learned behavior. Explore evolutionary theories and biological perspectives on the causes of aggression, examining how factors such as genetics, brain structures, hormones, and environmental pressures may influe
0 views • 11 slides
Understanding Evolutionary Theories and Strategies
Exploring evolutionary theories such as Sexual Selection Theory and Gene Selection Theory sheds light on how characteristics evolve for mating advantage. Insights into intersexual and intrasexual competition offer a deeper understanding of mate selection preferences. Gene selection mechanisms influe
0 views • 20 slides
Exploring Human Origins Through Hominid Fossils and Evolutionary Traits
Delve into the fascinating world of human origins, examining hominid fossils, anatomical traits, and evolutionary evidence. Learn about early species like Ardipithecus ramidus, differentiate African apes from modern humans, and analyze the genetic lineage supporting human evolution. Explore tables,
0 views • 14 slides
Secure Computation Challenges and Solutions in Data Mining
Exploring the intersection of secure computation and data mining, this content uncovers key challenges such as improving algorithms, converting programs for secure computation, and addressing parallelizability issues. It highlights the importance of cryptography in ensuring data privacy and presents
0 views • 30 slides
Covert Computation: Ensuring Undetectable Engagement
Covert computation aims to conceal the fact that computation is occurring and hide engagement in certain tasks like secure computation, authenticated key exchange, and more. By making messages indistinguishable and utilizing steganographic channels, it becomes possible to keep the activities covert
0 views • 16 slides
Overview of Turing Machines: Introduction, Tape, and Computation
Turing Machines are fundamental in the theory of computation, capable of recognizing all computable languages. They consist of a Finite State Machine combined with an infinite tape. The tape is initialized with input on the left end, and a TM's computation can either halt by entering special accept
0 views • 29 slides
Computation for Real Estate Sector in Bangalore Branch of ICAI
Practical overview of GST computation for real estate transactions in Bangalore, with details on old rates with ITC and new rate regime effective from April 1, 2019. The content discusses different transactions, conditions for new rates without ITC, and provides insights on the 80:20 computation met
0 views • 39 slides
Fides: A System for Verifiable Computation Using Smart Contracts
Fides presents a system for verifiable computation using smart contracts, focusing on blockchain basics, Ethereum, smart contracts, and outsourcing computation. It explores key components of blockchain, Ethereum's decentralized computing platform, properties of smart contracts, and the concept of ve
0 views • 25 slides
Insights into Secure Computation with Minimal Interaction
This paper revisits the concept of secure computation with minimal interaction, focusing on the challenges and possibilities of achieving secure multiparty computation in 2 rounds. Specifically exploring scenarios with 3 and 4 parties, the study delves into the reasons for choosing n=3, n=4, and t=1
0 views • 23 slides
Overview of Income Computation and Disclosure Standards (ICDS)
The Income-tax Act, 1961 introduced Income Computation and Disclosure Standards (ICDS) to be followed by certain assesses for computation of income. ICDS applies to taxpayers using the mercantile system of accounting from the Assessment Year 2016-17 onwards. Non-compliance with ICDS can lead to Best
0 views • 49 slides
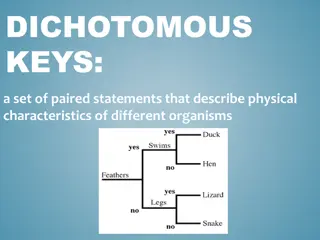
Understanding Dichotomous Keys and Cladograms in Evolutionary Biology
Dichotomous keys are utilized to classify different organisms based on their physical characteristics, while cladograms depict evolutionary relationships. Derived traits play a crucial role in understanding evolutionary history, indicating features present in later organisms but not earlier ones. Pr
0 views • 16 slides
Blackbox Verifiable Computation Scheme Overview
This summarized content discusses the concept of blackbox verifiable computation, focusing on the challenges faced by clients and servers, the role of helper oracles, positive results utilizing homomorphic encryption, and background information on Random Self Reducible (RSR) functions. The protocol
0 views • 20 slides
Parallel Computation for Matrix Multiplication
Matrix multiplication is a fundamental operation with diverse applications across scientific research. Parallel computation for matrix multiplication involves distributing the computational workload over multiple processors, improving efficiency. Different algorithms have been developed for multiply
0 views • 36 slides
Understanding Phylogenomics and Gene Function Prediction in Evolutionary Biology
Explore the significance of phylogenomics in predicting gene functions and establishing evolutionary relationships using genome-scale data. Learn about the challenges of using single genes or a few genes in phylogenetic analysis, the importance of analyzing multilocus data, and the need for multiple
0 views • 24 slides
Advanced Techniques in Multi-Party Computation
Explore cutting-edge methods in Multi-Party Computation (MPC), including leveraging Fully Homomorphic Encryption (FHE) for minimal round complexity, constructing MPC directly via FHE techniques, and simplifying multi-key FHE constructions for efficient decryption. Learn about key concepts such as di
0 views • 17 slides
Evolutionary Computation Explained Through Genetic Algorithms
Explore the world of evolutionary computation with a focus on genetic algorithms. Learn how non-classical search and model evaluation contribute to maximizing objective functions. Delve into the detailed process of generating and evaluating populations, selection techniques, and the key aspects of g
0 views • 22 slides