Introduction to Cryptography, Cryptanalysis, and Cryptology
Cryptography involves protecting information by encrypting and decrypting data, while cryptanalysis focuses on breaking encryption methods to access hidden messages. Cryptology encompasses both cryptography and cryptanalysis. Encryption encodes messages to prevent unauthorized access, while decrypti
8 views • 12 slides
Provable Security Models in Cryptography
Cryptography and cryptology involve secure communication techniques to protect data from third-party adversaries. This article introduces provable security models, cryptographic goals like confidentiality and authenticity, and the approach of security by trial-and-error versus provable security meth
5 views • 48 slides
Public Key Cryptography in Network Security
Explore the concepts of public key cryptography, key distribution challenges, solutions to secret key schemes, and the importance of secure communication in network security. Learn about cryptology, cryptography, cryptanalysis, block ciphers, stream ciphers, and more in this informative content.
2 views • 21 slides
Overview of Public-Key Cryptography and Knapsack Problem in Cryptology
This lecture delves into the realm of public-key cryptography, including the Knapsack one-way function and the Merkle-Hellman Crypto System. It explores historical perspectives, the concepts of OWFs, Elliptic Curve Cryptography, and introduces new algebra using additive groups over Elliptic Curves.
2 views • 16 slides
Introduction to Cryptology in Algebra 2 Classroom
Engage students in a high school Algebra 2 class by exploring cryptology concepts such as coding, hexadecimal systems, substitution ciphers, and the Vigenere cipher. The lesson plan includes activities like solving puzzles, introducing binary systems, converting to hexadecimal, and writing messages
1 views • 16 slides
Cryptology System Design Fundamentals - RSA Public Key System Analysis
The RSA public key system analysis involves determining suitable public and secret keys for users A and B, calculating distinct possible public keys, decrypting cryptograms, generating digital signatures, and discussing data ranges for secure communication. The solution covers the key generation pro
1 views • 16 slides
Cryptology System Design Fundamentals: ARSA Cryptosystem Examination Solutions
The given content discusses the solution to an ARSA cryptosystem final examination design problem, involving the computation of public and secret keys for users A and B, encryption and signing of messages, and considerations for attacker interceptions and computations. The solution guides through th
0 views • 18 slides
Introduction to Cryptology: Exploring Security in Information Networks
This lecture introduces the fundamentals of cryptology, discussing the importance of security in information networks. It covers topics such as the evolution of security technology, the open world of information networks, communication network evolution, and the impacts of globalization on informati
1 views • 27 slides
Coding, Cryptography, and Mathematics at TU/e
Delve into the world of coding, cryptography, and mathematics at TU/e, where you can explore topics such as coding theory, cryptology, discrete mathematics, and more. Discover research programs, experts in the field, and the intersection of mathematics and computer science at this renowned universit
2 views • 25 slides
Prime Numbers in Cryptology: Math Background & Tests
Delve into the significance of prime numbers in cryptology with this lecture covering prime number theory, generation, and methods for finding probable and provable primes using algorithms like Fermat's and Miller's tests. Discover the role of prime numbers in generating finite fields and explore th
3 views • 15 slides
Stream Ciphers
Stream ciphers are cryptographic algorithms used to encrypt individual bits, offering speed and efficiency. Learn about symmetric ciphers, encryption processes, synchronous vs. asynchronous stream ciphers, and key stream generation. Explore the evolution of stream ciphers in the field of cryptology,
0 views • 32 slides
Cryptography
Cryptography is the art of securing communication through the use of codes and ciphers. This overview covers fundamental concepts such as symmetric and asymmetric cryptography, hashes, attacks on cryptography, and best practices. Understand the terminologies in cryptography, the use of keys, and the
2 views • 63 slides
Essence of Data Security and Cryptology Course
Comprehensive "Data Security and Cryptology" course led by Valdo Praust at the Estonian IT College. Delve into contemporary data security and cryptology principles, covering both theoretical foundations and practical applications. Gain insights into securing data assets and leveraging cryptography f
4 views • 41 slides
Public Key Cryptography and Modern Cryptology
Delve into the world of cryptology with a focus on public key cryptography, as pioneered by Whitfield Diffie, Martin Hellman, and James Ellis. Explore the revolutionary concept of using public and private keys for secure communication without the need for a prior key exchange. Uncover the insights a
2 views • 38 slides
Introduction to Cryptology
Public-key cryptography revolutionized secure communication by eliminating the need for exchanging secret keys, as seen through the breakthroughs of Shannon and Diffie-Hellman. This lecture outlines the significance, principles, and challenges within this cryptographic system, paving the way for mod
0 views • 19 slides
Classical Encryption Techniques Overview
Overview of classical encryption techniques including plaintext, ciphertext, enciphering, deciphering, cryptanalysis, and cryptographic systems. Concepts of key sharing, cryptology, and secure encryption schemes explained.
4 views • 31 slides
Cryptography Basics and Contemporary Practices
Explore the evolution of cryptography from pre-computer traditional methods to contemporary practices, including the concepts of encryption, decryption, and the use of keys. Learn about the essential role of cryptography in data security and cryptology.
0 views • 53 slides
Essentials of Cryptography and Cybersecurity: Exploring Key Concepts
Delve into the foundations of cybersecurity cryptography, understanding the science of secrets, essential terminology, fundamental goals of information security, additional modern crypto goals, cryptographic protocols, attacker threat models, and key concepts regarding encryption and decryption. Exp
4 views • 103 slides
Cryptographic Protocols and Secret Sharing in Cryptology
Learn about cryptographic protocols like Shamir 3-Pass Protocol, secret sharing techniques, and threshold security schemes in the field of cryptology. Explore concepts such as no-key security protocols, Shamir's Threshold Scheme, and the use of encryption techniques like Vernam One-Time Pad Lock and
0 views • 22 slides
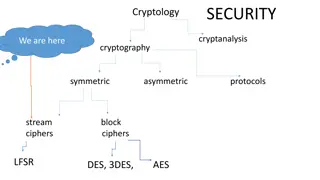
Cryptography and Block Ciphers: Understanding LFSR, DES, 3DES, AES
Explore the world of cryptology, cryptanalysis, symmetric, and asymmetric cryptography. Dive into the concepts of stream and block ciphers, LFSR, DES, 3DES, and AES encryption algorithms. Learn about key lengths, cycle lengths, and the security aspects of cryptographic systems.
3 views • 29 slides
Introduction to Cryptography: Understanding the Science of Cryptology
Discover the fascinating world of cryptography with this comprehensive guide. Learn about the principles of cryptology, including privacy, confidentiality, authentication, integrity, and non-repudiation. Delve into the techniques of cryptography and cryptanalysis to understand how to achieve and pro
2 views • 78 slides
Cryptology Tutorial: Mathematical Background of Groups, Rings, and Finite Fields
Explore the mathematical concepts of groups, rings, and finite fields in cryptology, including Euler's and Carmichael's theorems. Learn about invertible elements, multiplicative orders, and element orders in Z33 with detailed solutions provided.
3 views • 7 slides
Cryptology Mathematical Background: Groups, Rings, Finite Fields Overview
Explore the mathematical concepts of groups, rings, and finite fields in cryptology. Learn about the Euler function, multiplicative orders, and element orders in the ring of integers modulo m. Solve problems related to invertible elements, multiplicative orders, and element orders in Z33.
0 views • 7 slides
Understanding Information Systems Security and Cryptography
Delve into the world of information systems security and cryptography, exploring topics such as cryptology, encryption, hash functions, and encryption types. Learn about symmetric and asymmetric encryption, block ciphers, stream ciphers, and the importance of secure communication in today's digital
1 views • 48 slides
Cryptographic Identification Protocols and Solutions in Cryptology
Explore Fiat-Shamir and Omura proof-of-identity protocols in cryptology, solving challenges involving secret keys, random numbers, units, and verifier responses. Learn about zero-knowledge proof, security considerations, and computation of primitive elements over GF(24).
1 views • 11 slides
Cryptology System Design Fundamentals: ARSA Cryptosystem Examination
Explore ARSA cryptosystem design problems involving prime numbers, public and secret keys, message encryption, signatures, and decryption. Learn how to compute keys, verify signatures, and analyze key possibilities for users A and B.
1 views • 19 slides
Cryptology Tutorial: Understanding Primes and Generating Large Numbers
Learn about primality tests, generating large prime numbers, and using Pocklington's Theorem in cryptology. Explore examples of pseudoprimes and definitely prime numbers with mathematical solutions. Discover how to set up a cryptographic system using known prime numbers and primitive elements.
0 views • 6 slides
Understanding Information Security and Cryptology
Explore the concepts of information security, data processing, knowledge, and cryptology. Learn about the importance of protecting information from unauthorized access and the science of cryptography and cryptanalysis.
1 views • 15 slides
Cryptology Fundamentals: Security Theorems & Cipher Analysis
Explore the fundamentals of cryptology security theorems, including Shannon's security theorem, clear text redundancy, key entropy, and information entropy. Dive into cipher analysis problems, calculation of cryptogram bits, unicity distance, data rate changes, key length computations, and system se
0 views • 7 slides