Overcoming the UX Challenges Faced by FIDO Credentials in the Faced by FIDO Credentials in the Consumer Space
Many websites are vulnerable to phishing attacks due to traditional authentication methods. To address this, the utilization of cryptographic authentication, such as key pairs, is recommended to enhance security and prevent MITM attacks.
0 views • 17 slides
Cryptographic Reductions and Learning in Computational Complexity
This lecture explores the connection between computational complexity and cryptography, focusing on topics like pseudorandom functions, public-key cryptography, and learning from Gaussians. It delves into the implications of cryptographic reductions, lower bounds for learning MLPs, and the existence
0 views • 22 slides
Overview of Distributed Systems: Characteristics, Classification, Computation, Communication, and Fault Models
Characterizing Distributed Systems: Multiple autonomous computers with CPUs, memory, storage, and I/O paths, interconnected geographically, shared state, global invariants. Classifying Distributed Systems: Based on synchrony, communication medium, fault models like crash and Byzantine failures. Comp
9 views • 126 slides
Understanding Information Systems in Organizational Management
Management in organizations is divided into three levels: operational, tactical, and strategic. Each level requires different information systems to support various activities. Operational systems focus on routine transactions and control processes, while middle-level systems aid in semi-structured
8 views • 39 slides
Understanding E-commerce Data Collection and Legal Frameworks
Explore the implications of collecting data in e-commerce activities, legal status of electronic transactions, and electronic signatures in this informative module. Learn about analyzing data, regulatory environments, and cryptographic codes.
0 views • 8 slides
Challenges in Standard QUIC Protocol Implementation
The content discusses the challenges and shortcomings of the standard QUIC protocol implementation, focusing on the use of TLS 1.3 for cryptographic handshake. It highlights issues such as complexity in implementation and state machine, lack of a full security proof, and the risk of ossification due
0 views • 108 slides
Understanding Cryptographic Data Integrity Algorithms
Cryptographic data integrity algorithms ensure data integrity, verifying data received matches what was sent by authorized entities. Cryptographic hash functions play a crucial role in ensuring data integrity through hash values. Applications include message authentication, digital signatures, and v
1 views • 41 slides
Key Management and Distribution Techniques in Cryptography
In the realm of cryptography, effective key management and distribution are crucial for secure data exchange. This involves methods such as symmetric key distribution using symmetric or asymmetric encryption, as well as the distribution of public keys. The process typically includes establishing uni
1 views • 27 slides
Introduction to Public Key Cryptography
Public key cryptography, exemplified by algorithms like Diffie-Hellman and RSA, revolutionizes secure communication by allowing users to encrypt messages with public keys known to all and decrypt them with private keys known only to the intended recipient. This advanced encryption method ensures sec
1 views • 44 slides
Introduction to Embedded Systems Design
Embedded Systems Design, Chapter 1 provides an insightful overview of embedded systems, distinguishing them from general-purpose computers. The chapter delves into the characteristics of embedded systems, their design considerations, and the various types of embedded computers such as general-purpos
1 views • 7 slides
Expand Advantages with Hamster Tokens on Hamster Trade
Hamster Trade on Message is a progressive decentralized cryptographic money exchanging stage that consolidates the comfort of virtual entertainment with cutting-edge blockchain innovation. Clients benefit from secure, minimal expense exchanges, impro
0 views • 4 slides
Overview of Cryptography Techniques and Algorithms
Exploring the diverse realm of cryptography, this chapter delves into both nonmathematical and mathematical encryption methods. It covers substitution and transposition ciphers, steganography, hybrid systems, hashing, symmetric algorithms like DES and AES, as well as asymmetric algorithms utilizing
7 views • 21 slides
Cryptographic Hash Functions in Data Security: Mustansiriyah University Course Overview
Cryptographic hash functions play a crucial role in ensuring data integrity and security. This course at Mustansiriyah University's Faculty of Engineering covers the SHA-512 algorithm and its applications in various fields such as message authentication, digital signatures, and intrusion detection.
0 views • 6 slides
Understanding Diffie-Hellman Problems in Cryptography
Exploring Diffie-Hellman assumptions and problems including Computational Diffie-Hellman (CDH) and Decisional Diffie-Hellman (DDH). Discusses the difficulty of solving the DDH problem compared to CDH and discrete logarithm assumptions. Covers examples and implications of these cryptographic challeng
0 views • 6 slides
Understanding Security Goals and Cryptographic Algorithms
Introduction to security goals such as privacy, data integrity, authentication, authorization, and availability, along with the usage of cryptographic algorithms like symmetric and asymmetric key algorithms, keyed hashing, and digital signatures for achieving different security objectives in communi
0 views • 13 slides
Rainbow Signatures Overview and New Attacks
Rainbow signatures, introduced in 2005, offer good performance with small signatures but raise concerns due to large key sizes. This article explores the history of Rainbow, its vulnerabilities, new attacks, and the challenges posed by multivariate trapdoors. The overview delves into practical impli
0 views • 20 slides
Post-Quantum Cryptography in IEEE 802.11 - Current State and Future Concerns
Submission discusses the potential impact of post-quantum algorithms on IEEE 802.11 networks, highlighting the necessity to prepare for a post-quantum future. It explores the risks posed by quantum computing to existing cryptographic systems and emphasizes the importance of adopting post-quantum sol
0 views • 19 slides
Enhancing Cryptographic Key Generation with High-Quality Randomness
This presentation discusses the critical aspect of ensuring high-quality randomness in cryptographic key generation processes. It explores key vulnerabilities and common failure modes, emphasizing the importance of incorporating strong randomness. The content delves into various methods and issues r
0 views • 45 slides
Conflict Resolution in Distributed Systems: OT, Crypto, and Untrusted Cloud Services
Explore the complexities of conflict resolution in distributed systems, focusing on Operational Transformation (OT), cryptographic techniques, and handling data in untrusted cloud environments. Learn about concurrent writes, encoding operations as incremental updates, and consider shared word proces
0 views • 53 slides
Information Systems in Organizations: Overview and Implementation
Information systems play a crucial role in organizations, encompassing transaction processing systems, functional area information systems, and enterprise resource planning systems. This content delves into the purpose of transaction processing systems, the support provided by information systems ac
0 views • 30 slides
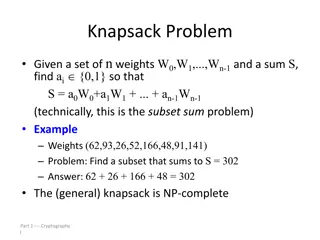
Understanding the Knapsack Problem and Cryptography
The knapsack problem involves finding a subset of weights that sums up to a given value. It can be applied in cryptographic systems, where superincreasing knapsacks are easier to solve than general knapsacks. The knapsack cryptosystem utilizes superincreasing knapsacks for encryption and conversion
0 views • 14 slides
Understanding Cryptographic Hash Functions
Cryptographic hash functions play a crucial role in various aspects of security, including integrity protection, checksum generation, password hashing, digital signatures, and more. They are designed to efficiently convert input data of arbitrary length into fixed-length output, aiding in tasks like
0 views • 32 slides
Enhancing Security for XMSS and SPHINCS+ Using Machine-Checked Methods
Advanced cryptographic techniques such as XMSS and SPHINCS+ are critical for ensuring secure digital signatures in a post-quantum world. This project focuses on improving the security and verification processes of XMSS and SPHINCS+ using machine-checked methods, aiming to enhance trust in these cruc
1 views • 17 slides
Cryptographic Algorithms and Hash Collisions Overview
Explore the world of cryptographic algorithms and hash collisions. Learn about various hashing algorithms like MD5, SHA-1, SHA-256, and more. Dive into the concepts of symmetric and asymmetric key algorithms and understand the risks associated with hash collisions. Discover the implications of post-
0 views • 58 slides
Franco-Japanese Cybersecurity Workshop Highlights and Future Plans
The 5th Franco-Japanese Cybersecurity Workshop concluded with insightful discussions on key areas such as IoT security, AI, hardware security, and supply chain security. The steering committee members shared plans for the 6th workshop in France, emphasizing policy discussions and cross-cutting issue
0 views • 18 slides
Understanding Quantum Computing and Its Impact on Cryptography
Quantum computing utilizes the principles of quantum mechanics to process information exponentially faster than classical computers. This advancement poses a significant threat to current cryptographic systems, especially those reliant on factors like RSA and Diffie-Hellman key exchange. If large-sc
0 views • 25 slides
Exploring the Role of Blockchain as a Trusted Third Party in Decentralized Systems
Blockchain technology serves as a decentralized and cryptographic Trusted Third Party (TTP) by enhancing trust, immutability, and censorship resistance in transactions. By distributing trust and utilizing cryptographic protocols, blockchain mitigates the need for a centralized authority, offering a
0 views • 30 slides
Cryptographic Center in Novosibirsk: Advancements in Cryptography and Research
The Cryptographic Center in Novosibirsk, established in 2011, focuses on advancing cryptography through research, education, and international collaborations. With a team of researchers and students, the center explores various aspects of cryptography, including cryptographic Boolean functions, ciph
0 views • 33 slides
Approaches to Secure Identification in Communication Networks
This content discusses various methods and protocols for secure identification and authentication in communication networks. It covers topics such as using passwords, biometrics, cryptographic protocols, and one-time password systems. Different approaches, their reliability, security levels, and cos
0 views • 11 slides
Evolution of TLS Security Profiles and Best Practices
TLS security profiles have evolved with the introduction of new profiles, retirement of old ones, and emphasis on non-downgrading best practices. Motivated by changes in security threats and cryptographic methods, the IETF has issued recommendations to ensure secure connections using TLS 1.2. The ne
0 views • 5 slides
Faster Implementation of Modular Exponentiation in JavaScript
Development of a cryptographic authentication toolkit for web application developers. Discusses modular exponentiation, digital signatures, elliptic curve cryptography, and the importance of DSA in providing secure authentication. Aims to offer both classical and elliptic curve cryptographic solutio
0 views • 22 slides
Foundations of Cryptography: Digital Signatures and Collision-Resistant Hash Functions
Foundations of Cryptography explores the construction of digital signature schemes and collision-resistant hash function families using one-way functions and safe primes. The content delves into the concept of collision-resistant hash functions and their construction from the discrete logarithm prob
0 views • 31 slides
Introduction to Cryptology in Algebra 2 Classroom
Engage students in a high school Algebra 2 class by exploring cryptology concepts such as coding, hexadecimal systems, substitution ciphers, and the Vigenere cipher. The lesson plan includes activities like solving puzzles, introducing binary systems, converting to hexadecimal, and writing messages
0 views • 16 slides
Understanding the Importance of Cryptographic Safety Valves in Legislation
Legislation regarding cryptographic safety valves is impending, with potential implications on privacy and security. Matt Tait discusses the need to analyze risks and consequences, emphasizing the importance of transparent and secure safety valves. The debate surrounds decryption requirements for da
0 views • 17 slides
Zeroizing Attacks on Cryptographic Multilinear Maps: Overview and Applications
Cryptographic multilinear maps (MMAPs) enable computations on encoded secret data, offering similarities to fully homomorphic encryption (FHE) while providing distinct features. MMAPs find applications in identity-based encryption, non-interactive zero-knowledge proofs, and more. The evolution of MM
0 views • 45 slides
CPA-Security and Multiple Message Security in Cryptography
Today's goal is to build a CPA-secure encryption scheme focusing on multiple message security. The concept of indistinguishable multiple encryptions against eavesdropping attackers is explored, highlighting the importance of secure encryption schemes in the presence of an eavesdropper. The experimen
0 views • 22 slides
Understanding Embedded Systems and Cyber-Physical Systems
Embedded systems are specialized computer systems embedded within larger systems, such as control systems and car controllers. This lecture covers real-time aspects, applications of Cyber-Physical Systems (CPS), and examples like the Boeing 777/Airbus A380 cockpit. It discusses the design process of
0 views • 22 slides
Understanding Cryptographic Protocols and Key Exchange
This content delves into the world of cryptographic protocols, discussing the importance of security measures such as symmetric cryptography, hash functions, and public-key cryptography. It explores the field's various studies, goals, Diffie-Hellman key exchange, and the significance of key size in
0 views • 28 slides
Fundamentals of Cryptography and Network Security
Explore the basics of cryptography, including classical encryption techniques, terminology definitions, types of encryption operations, cryptanalysis objectives and attacks, and the concept of cipher strength. Uncover the principles and methods behind encryption and decryption, key distinctions betw
0 views • 52 slides
Understanding Side Channels and Information Hiding Techniques in Advanced Information Assurance
This content covers various aspects of advanced information assurance, focusing on side channels and information hiding techniques such as digital watermarking, steganography, and covert channels. It discusses the concept of side-channel attacks, types of system and network channels, fault attacks,
0 views • 24 slides