Cryptographic Reductions and Learning in Computational Complexity
This lecture explores the connection between computational complexity and cryptography, focusing on topics like pseudorandom functions, public-key cryptography, and learning from Gaussians. It delves into the implications of cryptographic reductions, lower bounds for learning MLPs, and the existence
0 views • 22 slides
Case Studies on Successful Revenue Technology Implementations in Cargo Services (1)
In the fast-paced world of cargo services, optimizing pricing strategies remains a pivotal challenge for businesses aiming to boost profitability and maintain competitive advantage. Revenue technology, specifically tools that enable dynamic and cargo pricing, has revolutionized how companies approac
2 views • 5 slides
Understanding Cryptographic Data Integrity Algorithms
Cryptographic data integrity algorithms ensure data integrity, verifying data received matches what was sent by authorized entities. Cryptographic hash functions play a crucial role in ensuring data integrity through hash values. Applications include message authentication, digital signatures, and v
1 views • 41 slides
STM32WB BLE SW Application Sequencer Architecture Overview
The STM32WB BLE SW Application Sequencer is a specialized framework that optimizes while loop bare-metal implementations to avoid race conditions, especially in low power modes. It is not intended to compete with standard operating systems but rather with bare-metal implementations. The sequencer al
2 views • 14 slides
Understanding Synthetic Aperture Radar (SAR) Modes and Implementations
Explore the world of Synthetic Aperture Radar (SAR) through various modes and implementations, covering topics such as SAR coordinate systems, pulse compression, range-Doppler algorithms, Born approximation, SAR scene simulation, and more. Dive into the distinctions between unfocused SAR and focused
0 views • 18 slides
Cryptographic Hash Functions in Data Security: Mustansiriyah University Course Overview
Cryptographic hash functions play a crucial role in ensuring data integrity and security. This course at Mustansiriyah University's Faculty of Engineering covers the SHA-512 algorithm and its applications in various fields such as message authentication, digital signatures, and intrusion detection.
0 views • 6 slides
Understanding Security Goals and Cryptographic Algorithms
Introduction to security goals such as privacy, data integrity, authentication, authorization, and availability, along with the usage of cryptographic algorithms like symmetric and asymmetric key algorithms, keyed hashing, and digital signatures for achieving different security objectives in communi
0 views • 13 slides
Understanding Priority Queues and Heap Data Structures
Priority queues play a key role in computer science algorithms by managing data based on priority levels. The use of heap data structures enhances the efficiency of priority queue operations. This tutorial covers the basics of priority queues, their applications, different implementations such as li
0 views • 30 slides
Priority Queues in Java: Implementation and Use Cases
Explore the concept of priority queues in Java, covering implementations using unsorted and sorted linked lists, as well as heaps. Learn about the differences between a queue and a priority queue through reading quizzes and discover various priority queue implementation options. Dive into priority q
1 views • 42 slides
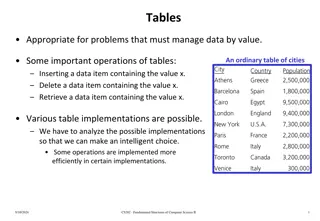
Implementations and Operations of Tables for Managing Data
An analysis of different table implementations for managing data by value, discussing operations like insertion, deletion, and retrieval. The post explores various linear and nonlinear implementations such as sorted arrays, linked lists, and binary search trees, highlighting the importance of select
0 views • 54 slides
Priority Queues: Operations and Implementations
Priority queues are data structures that allow efficient insertion, deletion, and retrieval of elements based on their priority. This information-rich content covers various aspects of priority queues, including ideal times, binomial queues, Dijkstra's algorithm for single-source shortest paths, and
0 views • 11 slides
Understanding Priority Queues and Heaps in CSE 373 Lecture
Today's lecture in CSE 373 covers the Priority Queue Abstract Data Type (ADT), the properties of heaps, and their implementations. Key topics include the completeness property of heaps, different priority queue implementations such as the binary search tree for faster insert and find operations, and
0 views • 21 slides
Enhancing 3DIC Implementations with Mix-and-Match Die Stacking
This study by Kwangsoo Han, Andrew B. Kahng, and Jiajia Li delves into the improved performance of 3DIC implementations through the mix-and-match die stacking technique. By integrating slow and fast tiers, they aim to enhance parametric yield and optimize design-stage processes for a more efficient
0 views • 19 slides
Enhancing Cryptographic Key Generation with High-Quality Randomness
This presentation discusses the critical aspect of ensuring high-quality randomness in cryptographic key generation processes. It explores key vulnerabilities and common failure modes, emphasizing the importance of incorporating strong randomness. The content delves into various methods and issues r
0 views • 45 slides
Understanding Queues in Computer Science: Principles and Implementations
Explore the concept of queues in computer science, focusing on ordered collections of data following the FIFO principle. Learn about queue ADTs, implementations in Python, and delve into a simulation of a Printer Queue problem. Discover how to model printing tasks as random events and analyze the im
0 views • 15 slides
Understanding DNS Flag Day and EDNS: A Comprehensive Overview
DNS Flag Day marks a coordinated effort to remove workarounds in DNS implementations, impacting domains in various ccTLDs like .CL, .CZ, .SE, .NU, and .NZ. Enhanced DNS (EDNS) provides a mechanism for supporting new options, but issues arise from poor DNS implementations causing delays and hindering
0 views • 20 slides
Understanding ADT List Operations and Implementations
In this detailed content, you will learn about the specifications and operations involved in working with an ADT list. The structure, domain operations, and user instructions are clearly outlined for efficient implementation. The content also delves into the representation and implementation aspects
0 views • 30 slides
Efficient Snapshot Implementations in Distributed Systems
This content discusses various snapshot implementations in distributed systems, focusing on achieving faster and sub-linear snapshot complexity. It covers topics such as multi-writer registers, tree structures, polylogarithmic snapshots, and the challenges of ensuring consistency across processes. T
0 views • 16 slides
Understanding Cryptographic Hash Functions
Cryptographic hash functions play a crucial role in various aspects of security, including integrity protection, checksum generation, password hashing, digital signatures, and more. They are designed to efficiently convert input data of arbitrary length into fixed-length output, aiding in tasks like
0 views • 32 slides
PacketGuardian: A Tool for Static Detection of Packet Injection Vulnerabilities
This research paper introduces PacketGuardian, an effective static analysis tool designed to evaluate the robustness of protocol implementations against packet injection attacks. This tool supports precise context, flow, field-sensitive taint analysis, implicit flow analysis, and employs a summary-b
0 views • 23 slides
Practical Implementations of Arithmetic Coding
Explore the practical implementations, advantages, and disadvantages of arithmetic coding in this informative guide. Learn about the basic algorithm, dynamic interval expansion, integer arithmetic coding, and methods to improve the speed of arithmetic coding. Dive deep into encoding algorithms, exam
0 views • 78 slides
Enhancing Security for XMSS and SPHINCS+ Using Machine-Checked Methods
Advanced cryptographic techniques such as XMSS and SPHINCS+ are critical for ensuring secure digital signatures in a post-quantum world. This project focuses on improving the security and verification processes of XMSS and SPHINCS+ using machine-checked methods, aiming to enhance trust in these cruc
1 views • 17 slides
Cryptographic Algorithms and Hash Collisions Overview
Explore the world of cryptographic algorithms and hash collisions. Learn about various hashing algorithms like MD5, SHA-1, SHA-256, and more. Dive into the concepts of symmetric and asymmetric key algorithms and understand the risks associated with hash collisions. Discover the implications of post-
0 views • 58 slides
Franco-Japanese Cybersecurity Workshop Highlights and Future Plans
The 5th Franco-Japanese Cybersecurity Workshop concluded with insightful discussions on key areas such as IoT security, AI, hardware security, and supply chain security. The steering committee members shared plans for the 6th workshop in France, emphasizing policy discussions and cross-cutting issue
0 views • 18 slides
Understanding Queues: Operations, Implementations, and Applications
Explore the world of queues, a fundamental data structure with operations like enqueue and dequeue, and implementations using arrays or linked lists. Dive into the applications of queues and their significance in various scenarios. Uncover the basics of queue operations and their practical implicati
0 views • 30 slides
AI-Based Compression and Understanding of Industrial Data (MPAI-CUI) - Company Performance Prediction Use Case
AI-based Compression and Understanding of Industrial Data (MPAI-CUI) is a standard developed by the MPEG standards group. This standard focuses on transforming data into a more suitable format for applications. The presentation will cover the introduction to MPAI, applications, a demo for anonymous
0 views • 25 slides
Understanding Quantum Computing and Its Impact on Cryptography
Quantum computing utilizes the principles of quantum mechanics to process information exponentially faster than classical computers. This advancement poses a significant threat to current cryptographic systems, especially those reliant on factors like RSA and Diffie-Hellman key exchange. If large-sc
0 views • 25 slides
Exploring the Role of Blockchain as a Trusted Third Party in Decentralized Systems
Blockchain technology serves as a decentralized and cryptographic Trusted Third Party (TTP) by enhancing trust, immutability, and censorship resistance in transactions. By distributing trust and utilizing cryptographic protocols, blockchain mitigates the need for a centralized authority, offering a
0 views • 30 slides
Cryptographic Center in Novosibirsk: Advancements in Cryptography and Research
The Cryptographic Center in Novosibirsk, established in 2011, focuses on advancing cryptography through research, education, and international collaborations. With a team of researchers and students, the center explores various aspects of cryptography, including cryptographic Boolean functions, ciph
0 views • 33 slides
Faster Implementation of Modular Exponentiation in JavaScript
Development of a cryptographic authentication toolkit for web application developers. Discusses modular exponentiation, digital signatures, elliptic curve cryptography, and the importance of DSA in providing secure authentication. Aims to offer both classical and elliptic curve cryptographic solutio
0 views • 22 slides
Understanding ADTs: Lists, Stacks, and Queues - Implementation and Operations
Explore the world of Abstract Data Types (ADTs) - Lists, Stacks, and Queues, focusing on their operations like adding, removing, and accessing elements. Learn the differences between array and linked list implementations, along with insights on how to manipulate data structure implementations. Dive
0 views • 18 slides
Understanding the Importance of Cryptographic Safety Valves in Legislation
Legislation regarding cryptographic safety valves is impending, with potential implications on privacy and security. Matt Tait discusses the need to analyze risks and consequences, emphasizing the importance of transparent and secure safety valves. The debate surrounds decryption requirements for da
0 views • 17 slides
High Performance User-Level Sockets over Gigabit Ethernet
Presentation overview of the design challenges, performance enhancement techniques, and results related to implementing high-performance user-level sockets over Gigabit Ethernet networks. The background and motivation discuss the limitations of traditional kernel-based implementations and the need f
1 views • 34 slides
Zeroizing Attacks on Cryptographic Multilinear Maps: Overview and Applications
Cryptographic multilinear maps (MMAPs) enable computations on encoded secret data, offering similarities to fully homomorphic encryption (FHE) while providing distinct features. MMAPs find applications in identity-based encryption, non-interactive zero-knowledge proofs, and more. The evolution of MM
0 views • 45 slides
Overview of HERDOS TES and SNiPER TES
HERDOS TES and SNiPER TES are discussed in detail, outlining their implementations and distinctive features. The discussion includes insights on TES requirements, concrete implementations, DataBuffer usage, HERD TES reliance on podio, and the migration plan to podio
0 views • 10 slides
Understanding Cryptographic Protocols and Key Exchange
This content delves into the world of cryptographic protocols, discussing the importance of security measures such as symmetric cryptography, hash functions, and public-key cryptography. It explores the field's various studies, goals, Diffie-Hellman key exchange, and the significance of key size in
0 views • 28 slides
Exploring Web Services at IRIS: Implementations and Coordination
Discover the world of web services at IRIS through a detailed exploration of implementations, international coordination efforts, and the team behind these endeavors. Learn about the definition of web services, practical examples, and the various data and processing services offered by IRIS to suppo
0 views • 24 slides
Understanding Noise*: A Verified Secure Channel Protocol Library
Explore Noise*, a library of high-performance secure channel protocol implementations that have been verified for correctness. The Noise protocol examples, such as IKpsk2, showcase key exchange patterns used in applications like WhatsApp and Wireguard VPN. Discover the importance of verified impleme
0 views • 18 slides
New Assumptions for Achieving Chosen Ciphertext Security in Cryptography
This research work focuses on presenting new assumptions for achieving chosen ciphertext security in public key encryption. The study aims to clarify the necessary and sufficient assumptions to realize general cryptographic primitives, particularly focusing on CCA secure PKE and KEM. The ultimate go
0 views • 27 slides
Scalable Cryptographic Authentication for High Performance Computing
This work discusses the scalable cryptographic authentication approach developed by Andrew Prout and team for high-performance computing. The LLGrid system architecture, challenges with interactive supercomputing, and utilization of LLGrid for various computing tasks are explored, highlighting the i
0 views • 34 slides