Adversarial Machine Learning in Cybersecurity: Challenges and Defenses
Adversarial Machine Learning (AML) plays a crucial role in cybersecurity as security analysts combat continually evolving attack strategies by malicious adversaries. ML models are increasingly utilized to address the complexity of cyber threats, yet they are susceptible to adversarial attacks. Inves
2 views • 46 slides
United Nations Survey on Crime Trends and Operations of Criminal Justice Systems
The United Nations Survey on Crime Trends and Operations of Criminal Justice Systems (UN-CTS) focuses on harmonizing data collection, identifying crime patterns, improving monitoring of the criminal justice system, and enhancing international comparability of crime statistics. It was mandated by the
3 views • 18 slides
Harmonisation of Substantive Criminal Law in the EU
The Treaty of Lisbon serves as a legal foundation for the harmonisation of substantive criminal law within the European Union. It establishes the basis for judicial cooperation, mutual recognition of judgments, and approximation of laws across Member States. The treaty allows for the establishment o
2 views • 60 slides
Understanding Criminal Behavior from a Social Psychological Perspective
This unit delves into the application of social psychology in the legal system, exploring the nature of criminal behavior, responses to criminal acts, the criminal justice system, and rehabilitation. It examines the social ecological perspective of criminal acts and outlines key points related to th
0 views • 50 slides
Understanding Psychological Theories of Criminal Behavior
Psychologically-based criminologists attribute criminal behavior to individual factors such as negative early childhood experiences and inadequate socialization, leading to criminal thinking patterns and incomplete cognitive development. Probation and parole practices are influenced by rehabilitatio
0 views • 30 slides
Exploring Adversarial Machine Learning in Cybersecurity
Adversarial Machine Learning (AML) is a critical aspect of cybersecurity, addressing the complexity of evolving cyber threats. Security analysts and adversaries engage in a perpetual battle, with adversaries constantly innovating to evade defenses. Machine Learning models offer promise in combating
0 views • 43 slides
Understanding Criminal Law and Procedure: Greenvisor's Case
A case study involving embezzlement by Joe Greenvisor, the chief accountant of Nobreath Corporation, sheds light on criminal acts, duties, intent, and societal perspectives on crime. Despite Greenvisor's charitable intentions, his actions constituted a crime under the law. The elements of criminal a
0 views • 47 slides
Understanding Criminal Offences: A Comparative Analysis
Exploring the concept of criminal offences, this article delves into the definitions in common law and continental law systems. It discusses the structural elements, harmful nature, prohibition, punishment, and distinctive aspects of criminal acts. A comparison between common law and continental law
1 views • 33 slides
Understanding the Process of Sealing Criminal Records
Having a criminal record sealed means making it inaccessible to the public while keeping it available to criminal justice agencies. Eligibility for sealing records requires taking action, and not everyone qualifies. This clinic provides guidance on the sealing process and the types of records that c
0 views • 36 slides
Understanding the Roles in Criminal Justice System
The criminal justice system involves three branches of government, each with specific responsibilities, operating at federal, state, and local levels. Law enforcement is primarily a local government function, while legislatures determine criminal laws and punishments. Statutes organized into codes d
0 views • 35 slides
Understanding Substantive Criminal Law in the American Legal System
Substantive criminal law encompasses the definition of criminal acts and penalties, with a core principle being that there can be no crime without a corresponding law. The American legal system follows the Rule of Law, ensuring that all individuals are subject to legal governance. Constitutional lim
0 views • 22 slides
Confiscation in the Criminal Courts: A Guide to Proceeds of Crime Law
Confiscation in the criminal courts involves depriving defendants of benefits gained from criminal conduct within their means. The Proceeds of Crime Law in the Cayman Islands sets guidelines for these proceedings, emphasizing that confiscation is not a form of punishment but aims to recover obtained
3 views • 17 slides
Understanding the Process of Sealing Criminal Records
Sealing criminal records means restricting public access to the records, although they are not destroyed and remain accessible to certain entities. Eligibility requirements vary, and action must be taken to seal records. This presentation covers the process, eligibility criteria, and what to expect
1 views • 36 slides
Criticisms and Defenses of Verification and Falsification Principles
Explore the criticisms and defenses of the Verification and Falsification Principles in religious language. Understand how believers defend the use of religious language and analyze challenges posed to the Verification Principle by notable thinkers like Swinburne, Hare, and Mitchell. Delve into resp
2 views • 15 slides
Understanding Civil and Criminal Complaints in Legal Cases
Explore the distinctions between civil and criminal complaints in legal scenarios. Learn how a civil case seeks monetary damages while a criminal case pursues punishment for wrongful actions. Understand the roles of plaintiffs and prosecutors, burden of proof, and outcomes in both civil and criminal
0 views • 34 slides
Briefing on the Criminal Procedure Amendment Bill [B12-2021] to the Portfolio Committee on Justice and Correctional Services
The Criminal Procedure Amendment Bill aims to address the constitutional invalidity of section 154(3) of the Criminal Procedure Act by enhancing protection for child victims, accused, and witnesses in criminal proceedings. The Bill proposes prohibiting the publication of information revealing their
0 views • 12 slides
Location Privacy Protection Strategies: A Comprehensive Overview
This study delves into optimal strategies to safeguard location privacy against localization attacks in the realm of location-based services. Discussing the shortcomings of anonymization and obfuscation as standalone defenses, it explores the challenges and pitfalls in designing effective protection
0 views • 26 slides
Understanding Criminal Behaviour Orders: An Overview and Legal Requirements
Criminal Behaviour Orders (CBOs) are issued following conviction for criminal offences to tackle serious and persistent anti-social behavior. This talk provides an overview of CBOs, legal requirements, when they are appropriate, and practical tips for implementation. The orders can prohibit or requi
0 views • 12 slides
Buffer Overflow: Understanding, Defenses, and Detection
Dive into the world of buffer overflow attacks with insights on understanding the concept, implementing defenses, and detecting stack smashing using techniques like canary values. Discover how to protect against vulnerabilities and grasp the significance of elements such as EIP, ASLR, DEP, and NX bi
0 views • 10 slides
Understanding Control Hijacking Attacks and Defenses
Control hijacking attacks pose a significant threat by allowing malicious actors to manipulate data and control flow within a system. This article explores common attack methods like stack smashing and heap spraying, along with defenses such as fixing bugs, implementing platform defenses, and markin
1 views • 36 slides
Understanding Voluntary Manslaughter and Diminished Responsibility in Criminal Law
Voluntary manslaughter is a legal concept where certain special defenses can reduce a murder charge to manslaughter, giving judges discretion in sentencing. Diminished responsibility, introduced by the Homicide Act, allows individuals suffering from abnormal mental functioning during a killing to ha
0 views • 23 slides
Land Tort Elements: Liability and Defenses
Key elements of tort law related to bringing onto land, foreseeability of mischief, requirement of escape, non-natural use, defenses like statutory authority and consent, as well as exemptions such as acts of God are explored through case law examples like Giles v. Walker and Rylands v. Fletcher.
0 views • 9 slides
Understanding Criminal Defenses and Legal Concepts
Explore the intricate realm of criminal defenses, from Mens Rea to Actus Reus, and delve into various defense strategies such as alibi, excuse defense, defense of self, property, and others. Uncover the nuances of legal concepts like infancy and not criminally responsible excuses in the context of c
3 views • 19 slides
Understanding the Health Effects of Silica Exposure
Silica exposure poses serious health risks as respirable crystalline silica particles can penetrate the body's natural defenses, leading to conditions like silicosis, tuberculosis, lung cancer, and chronic bronchitis. The silica particles that bypass initial defenses can cause inflammation and fibro
0 views • 17 slides
Asset Recovery Practices in England and Wales: Criminal vs. Civil Proceedings
Asset recovery in England and Wales involves a combination of criminal and civil proceedings to secure justice and return funds to victims of crime. The CPS's Proceeds of Crime Division plays a crucial role in obtaining Restraint Orders and Confiscation Orders. Civil recovery, focusing on illicit fi
0 views • 11 slides
Security Issues in Parallel and Distributed Computing - Side Channel Attacks and Defenses
Explore various security threats in parallel and distributed computing, focusing on side channel attacks and defenses. Learn about microarchitecture, cache hierarchy, popular attacks, defense mechanisms, and more. Discover how hardware vulnerabilities can lead to the compromise of sensitive data and
1 views • 30 slides
Understanding the Immune System: Defenses Against Pathogens
Delve into the intricate workings of the immune system as it fights off pathogens to protect the body. Explore how external defenses like tears, saliva, and skin, along with internal defenses like inflammation and white blood cells, work together to maintain homeostasis and safeguard against sicknes
0 views • 21 slides
Exploring the Factors Behind Criminal Behavior
Understanding who commits crime and why certain individuals are more likely to engage in criminal activities involves exploring a range of social and biological factors. While biology suggests a genetic predisposition to criminal behavior, sociology emphasizes the influence of social factors like fa
0 views • 9 slides
Eviction Mediation Training Updates and AB486 Overview
Explore the latest updates on eviction mediation training featuring AB486 and AB141. AB486 covers designated eviction proceedings, provides new affirmative defenses for tenants, and allows defenses to be raised at any time during the process. Learn about the impact of these changes on eviction cases
0 views • 25 slides
Illinois Accident Defenses and McAllister Decision Overview
Illinois accident defenses encompass fraud, occurring in the course of employment, and arising out of employment. Fraudulent claims often exhibit signs like delayed reporting and inconsistencies. Claims must be examined for their alignment with the context of employment. Illinois law requires a demo
0 views • 26 slides
Understanding Plant-Nematode Interaction: Defense Mechanisms and Parasitism
In the intricate relationship between plants and parasitic nematodes, plant defenses play a crucial role in combating biotrophic pathogens. The nematodes exploit various strategies to suppress these defenses and establish successful parasitism. The defense mechanisms of plants involve pre-existing b
0 views • 13 slides
Targeted Deanonymization via the Cache Side Channel: Attacks and Defenses
This presentation by Abdusamatov Somon explores targeted deanonymization through cache side-channel attacks, focusing on leaky resource attacks and cache-based side-channel attacks. It discusses the motivation behind these attacks, methods employed, potential defenses, and the evaluation of such att
0 views • 16 slides
Understanding the Interaction Between Criminal Investigations and Civil Tax Audits in Sweden
The relationship between criminal investigations and civil tax audits in Sweden is explored, highlighting how tax audits and criminal proceedings run concurrently. The mens rea requirement for criminal sanctions and tax surcharge, as well as the integration between criminal sanctions and tax surchar
0 views • 13 slides
Evaluating Adaptive Attacks on Adversarial Example Defenses
This content discusses the challenges in properly evaluating defenses against adversarial examples, highlighting the importance of adaptive evaluation methods. While consensus on strong evaluation standards is noted, many defenses are still found to be vulnerable. The work presents 13 case studies o
0 views • 9 slides
Analysis of CSRF Defenses in Web Frameworks
This study delves into CSRF attacks, a long-standing web vulnerability, and evaluates the effectiveness of CSRF defenses in popular web frameworks. It addresses the lack of knowledge about the security of CSRF defense implementations and their susceptibility to misuse, aiming to enhance understandin
0 views • 37 slides
Immune Responses in Plants and Animals: A Comprehensive Overview
Plants and animals have evolved a variety of chemical defenses to combat infections and maintain homeostasis. Innate immunity provides immediate protection through barrier and internal defenses, while acquired immunity offers specific responses involving humoral and cell-mediated mechanisms. Plants
0 views • 26 slides
Fundamentals of Criminal Law and Procedure
Explore the key aspects of criminal law and procedure, including definitions of crime, the role of criminal procedure, sources of law, phases of the criminal process, participants involved, and rules of evidence in legal proceedings. Gain insight into how criminal law is distinct from civil law and
0 views • 24 slides
Housing Court Advice Clinic Volunteer Training Highlights
Explore an insightful housing court advice clinic volunteer training program covering legal aspects of eviction laws, scenarios, court procedures, and defenses. Delve into topics like housing court basics, eviction reasons, defenses, important laws, rules, and grounds for eviction. Gain valuable adv
0 views • 36 slides
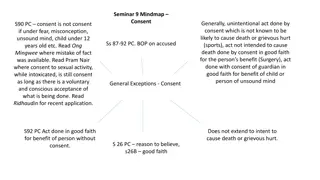
Legal Principles of Consent and Mistake in Criminal Law
In criminal law, consent plays a crucial role in determining liability for acts done with or without intention. The seminar mind map explores the concepts of consent, accidents, mistakes, and necessity in legal contexts, outlining the key principles, exceptions, and application in different scenario
0 views • 4 slides
Formal Security Evaluation for Microarchitectural Modeling
This content discusses the challenges and defenses in evaluating formal security for microarchitectural modeling. It covers topics such as constant-time programs, speculative machines, post-quantum cryptography, side-channel attacks, and defense proposals against vulnerabilities like Spectre and Gho
0 views • 20 slides















![Briefing on the Criminal Procedure Amendment Bill [B12-2021] to the Portfolio Committee on Justice and Correctional Services](/thumb/157093/briefing-on-the-criminal-procedure-amendment-bill-b12-2021-to-the-portfolio-committee-on-justice-and-correctional-services.jpg)