Buy GBP �50 Bills Online — globcoffs.com
Purchase $50 bills online For Sale from Covert Counterfeiters. Since 2002, this message has been doing the rounds. The notes are issued by either the European Central Bank or the national central banks of the Euro system.The former national currencies were quickly replaced by the euro, which then gr
3 views • 2 slides
Narration and Focalization
Unveil the intricate layers of narration and focalization in storytelling, delving into the impact of the narrator on the story's perception. From the nuances of narration in literature to the complexities of narration in audiovisual content, uncover the diverse facets that shape the fictional world
0 views • 36 slides
Alberta Emergency Management Agency Overview
The Alberta Emergency Management Agency (AEMA) is dedicated to providing strategic leadership in emergency management and business continuity in Alberta. AEMA collaborates with partners and stakeholders to enhance disaster resilience in the region. The agency's structure includes the Managing Direct
3 views • 19 slides
Steganography: Hiding Secrets in Plain Sight
Steganography, the art and science of concealing secret messages in such a way that no one suspects their existence, differs from cryptography in its goal of avoiding suspicion rather than rendering the message unreadable. This method involves hiding messages within seemingly innocuous data, such as
2 views • 76 slides
Understanding Human Behavior: Foundations and Complexity
Human behavior encompasses the actions and interactions of individuals influenced by factors like genetics, culture, and situational contexts. It involves observable overt behaviors as well as hidden covert behaviors, with a dynamic interplay between individuals and their environments. Psychologists
8 views • 20 slides
COMPUTER ORGANISATION Register Transfer Language
Register Transfer Language is a symbolic notation used to describe the micro-operations transferring data among registers in computer organisation. It signifies the availability of hardware logic circuits to perform specified micro-operations and transfer results between registers. Register Transfer
6 views • 7 slides
Unveiling the Effects of Institutionalized Racism on Indigenous Peoples
Delve into the intricate web of institutionalized racism faced by Indigenous communities, exploring key concepts like covert racism versus operant racism, decolonization, and settler benefits. Learn how historical injustices, such as the Indian Act, continue to impact Indigenous autonomy and the fig
9 views • 21 slides
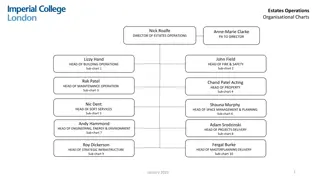
Organisational Structure of Estates Operations Team
The organisational chart depicts the hierarchical structure of the Estates Operations team, led by the Director of Estates Operations. It showcases the various heads and managers responsible for building operations, maintenance, soft services, space management, projects delivery, engineering, energy
0 views • 20 slides
Understanding C++ I/O Operations: Streams, Stream Classes, and Functions
C++ I/O operations involve managing console input and output using streams, stream classes, and functions. Learn about stream types, stream classes for console I/O, unformatted I/O operations, put() and get() functions for character I/O, getline() and write() functions, formatted console I/O operati
0 views • 37 slides
Understanding Fractions: Basic Concepts and Operations
This comprehensive guide covers the fundamentals of fractions, including simplest forms, improper fractions, mixed numbers, and operations like addition and subtraction. Learn how to express fractions in their simplest form, convert improper fractions to mixed numbers, and perform arithmetic operati
0 views • 19 slides
Understanding Organizational Behavior and Characteristics
Organizational behavior explores how individuals behave in various contexts such as child, IPS officer, businessman, etc. An organization is a consciously coordinated unit comprising two or more individuals working towards common goals. Characteristics of an organization include deliberate creation,
2 views • 41 slides
Best Sales Operations Management in the USA
Transform your sales operations with Tjcollinschase.com, the premier provider of Sales Operations Management in the United States. Maximize your profits and simplify your operations today!\n\n\/\/tjcollinschase.com\/services-business\/
3 views • 1 slides
Understanding the Strategic Role of Operations Management
The strategic role of operations management involves cost leadership, good/service differentiation, and interdependence with other key business functions. Operations management coordinates activities to add value by producing outputs valued by consumers. The operations department acquires inputs and
0 views • 23 slides
Effective PC/PB Operations for Successful Committees and Meetings
Understanding the importance of operations within PC/PB committees is crucial for fulfilling legislative responsibilities efficiently. This training module covers key objectives such as committee structures, factors to consider in committee structuring, characteristics of successful meetings, managi
0 views • 34 slides
IEEE 802.11-19/1517r0 TDD Beamforming Configuration Overview
IEEE 802.11-19/1517r0 discusses TDD beamforming operations related to Beam Measurement in the standard. Before Draft 4.0, these operations were primarily initiated by SME, causing limitations due to proprietary network controllers. The document reviews gaps and improvements in TDD beamforming, aimin
0 views • 10 slides
Understanding Human Behavior: Foundations and Factors
Human behavior is a multifaceted subject influenced by genetic makeup, culture, and individual values. It encompasses both overt actions and covert thoughts, a product of the individual and environmental factors. Psychologists study behavior from visible (overt) actions like playing football to inne
0 views • 20 slides
Understanding Computer Organization and Design: Chapter 2
This content discusses shift operations, AND operations, OR operations, EOR operations, and conditional operations in computer organization and design. It covers topics such as shifting logical operations, masking bits, including bits, differencing operations, and conditional branching instructions,
0 views • 22 slides
Best Wireless Alarms in Leixlip
Are you looking for the Best Wireless Alarms in Leixlip? Then contact Covert Security. They offer comprehensive residential and commercial security services nationwide. They specialize in providing bespoke intruder wireless alarms and CCTV packages t
0 views • 6 slides
Understanding Side Channels in Software Security
This content delves into the topic of side channels in software security, focusing on the leakage of sensitive information through timing side channels. It discusses the concept of covert channels, reference monitors, limitations of analysis, and prevention strategies to mitigate the risks associate
0 views • 25 slides
Covert Actions and Their Consequences
The chapter discusses foreign covert actions, their limited statutory control, and the President's discretion in carrying them out. It delves into the Bay of Pigs incident, forms of covert actions like propaganda and paramilitary actions, unintended consequences, and the Neutrality Act of 1794. The
1 views • 31 slides
Eisenhower's Cold War Policies and Covert Operations
Eisenhower's Cold War policies focused on Massive Retaliation, Brinkmanship, and Covert Operations. He believed in investing in nuclear weapons and used threats of nuclear capabilities to deter conflicts. The CIA carried out covert operations to overthrow anti-American leaders in different countries
0 views • 10 slides
Covert Visual Search and Effective Oculomotor Range Constraints
The study delves into whether covert visual search is biologically limited by the Effective Oculomotor Range (EOMR), exploring neuropsychological evidence, eye movement studies, and participant measurements. It investigates the impact on visual search tasks, including color, orientation, and conjunc
1 views • 15 slides
Understanding Language Variation and Social Identity
Language and society are intricately connected through accent, dialect, standard English, and non-standard English. The concepts of convergence, divergence, covert prestige, and overt prestige influence how identity is formed. This text delves into regional dialects and accents, highlighting the dif
2 views • 63 slides
Covert Actions and Laws: A Historical Overview
Covert actions, unconstrained by domestic laws, have been historically carried out by various entities in different ways. This overview delves into the Intelligence Authorization Act of 1991, limitations imposed by Congress, utilization of private contractors, challenges in enforcement, and relevant
0 views • 74 slides
Understanding Malware and Computer Security
Exploring the world of malware and computer security, this content delves into different types of malware such as Trojan horses, viruses, worms, and rootkits. It discusses how malware can violate site security policies and the covert actions they can carry out without detection. Examples like the Ge
0 views • 127 slides
Comprehensive Overview of FinSpy Surveillance System
FinSpy is a powerful tool designed for Law Enforcement and Intelligence Agencies to remotely monitor computer systems. It provides access to online communication platforms, internet activities, stored data, surveillance devices, and more. The system components include FinSpy Agent with graphical use
0 views • 190 slides
Security Analysis of Networked Control Systems in Smart Vehicles
This paper explores the security challenges faced by networked control systems in smart vehicles, focusing on adaptive cruise control technology. It discusses the vulnerabilities in cyber-physical systems, such as intrusion detection systems, and highlights the potential risks posed by cyber attacks
0 views • 21 slides
Expert Guidelines on Treatment of Small Vessel Disease
Expert recommendations for the management of covert cerebral small vessel disease (ccSVD) emphasize the use of antihypertensive treatment for hypertensive patients to prevent SVD lesion progression. While there is limited evidence supporting intensive blood pressure lowering targets, systematic bloo
0 views • 14 slides
Evolution of Intelligence Services: Past, Present, and Future
The evolution of intelligence services from pre-digital to post-digital eras is explored, highlighting changes in data collection, analysis, and privacy implications. Legal issues, covert operations, and the impact of bulk data collection are discussed along with the challenges of analyzing vast amo
0 views • 68 slides
Understanding Spectre and Meltdown Security Vulnerabilities
Spectre and Meltdown are two critical security vulnerabilities that exploit microarchitectural features to gain unauthorized access to memory. These vulnerabilities enable attackers to read memory that should be inaccessible, targeting branch prediction and exception handling mechanisms. Side channe
0 views • 19 slides
Covert Computation: Ensuring Undetectable Engagement
Covert computation aims to conceal the fact that computation is occurring and hide engagement in certain tasks like secure computation, authenticated key exchange, and more. By making messages indistinguishable and utilizing steganographic channels, it becomes possible to keep the activities covert
0 views • 16 slides
Challenges in Content Moderation and Cognitive Performance
The content discusses the impact of global social information environment and human-centric cyber vulnerabilities on cognitive performance. It emphasizes the erosion of cognitive abilities due to biases, diminished critical thinking, and exposure to covert exploitation. The dynamics are observed in
0 views • 27 slides
Unveiling the Art of Investigative Journalism
Investigative journalism involves uncovering concealed information, whether intentionally hidden by powerful individuals or obscured amid a sea of facts. It requires utilizing a variety of sources, both public and covert. This practice distinguishes itself from conventional journalism by delving dee
0 views • 41 slides
Understanding Political Spin and Propaganda in Media
Explore the tactics of political spin and propaganda as tools used to shape public perception and manipulate information. Learn about the techniques politicians employ to navigate media dynamics and the covert spin tactics employed in the realm of communication and journalism.
0 views • 10 slides
Fingerprinting Smart Devices Through Acoustic Components
Smartphones can be uniquely identified through their embedded acoustic components, allowing for targeted advertising and secondary authentication. This method leverages sensors like microphones to create device fingerprints. The goal is to extract these fingerprints through scenarios involving audio
0 views • 25 slides
Understanding Spectre and Meltdown Security Flaws
Recent security vulnerabilities named Spectre and Meltdown have surfaced in the realm of computer architecture and hardware implementation. These flaws allow attackers to access sensitive data through covert channels utilizing speculative execution mechanisms. The vulnerabilities exploit the perform
0 views • 12 slides
Understanding Covert Timing Channels in Network Security
Covert timing channels are a method of leaking sensitive information across networks by violating security policies. These channels rely on conveying information through packet arrival patterns rather than the contents of the packets. Military applications, detection by USA government agencies, and
0 views • 26 slides
Russian Economic Warfare in Central and Eastern Europe: Challenges and Impacts
Russia employs overt and covert economic warfare tactics in Central and Eastern Europe, including energy blockages and media manipulation. This strategy poses challenges to democratic values and institutions. The study examines the correlation between Russia's economic footprint and democratic stand
0 views • 24 slides
Understanding Side Channels and Information Hiding Techniques in Advanced Information Assurance
This content covers various aspects of advanced information assurance, focusing on side channels and information hiding techniques such as digital watermarking, steganography, and covert channels. It discusses the concept of side-channel attacks, types of system and network channels, fault attacks,
0 views • 24 slides
Understanding the Importance of Anonymous Communication in Digital World
Explore the concept of information hiding, including digital watermarking, steganography, covert channels, and anonymous communication. Learn how anonymity can benefit journalists, whistleblowers, activists, executives, and more, while also providing privacy for everyday individuals. Discover the ch
0 views • 56 slides