Introduction to Cryptography, Cryptanalysis, and Cryptology
Cryptography involves protecting information by encrypting and decrypting data, while cryptanalysis focuses on breaking encryption methods to access hidden messages. Cryptology encompasses both cryptography and cryptanalysis. Encryption encodes messages to prevent unauthorized access, while decrypti
2 views • 12 slides
Introduction to Cryptography: The Science of Secure Communication
Cryptography is the study of methods for sending and receiving secret messages securely. This lecture explores the application of number theory in computer science, focusing on the design of cryptosystems like public key cryptography and the RSA cryptosystem. The goal of cryptography is to ensure th
0 views • 53 slides
Introduction to Cryptography and Its Applications in Computer Science
Cryptography is the study of methods for sending and receiving secret messages. In this lecture, we explore the design and application of cryptosystems, such as the RSA cryptosystem and Turing's Code. The goal is to securely encrypt and decrypt messages using number theory to protect communication f
2 views • 53 slides
Cryptography Concepts and Encryption Methods Overview
Exploring elementary cryptography concepts such as encryption, cryptanalysis, symmetric and asymmetric encryption algorithms like DES, AES, and RSA. Delve into key exchange protocols, digital signatures, cryptographic hash functions, and the process of encryption and decryption in a cryptosystem.
0 views • 23 slides
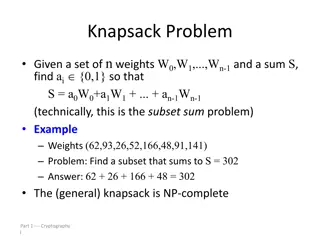
The Knapsack Problem and Cryptography
The knapsack problem involves finding a subset of weights that sums up to a given value. It can be applied in cryptographic systems, where superincreasing knapsacks are easier to solve than general knapsacks. The knapsack cryptosystem utilizes superincreasing knapsacks for encryption and conversion
0 views • 14 slides
Overview of Knapsack Cryptosystems and Related Problems
The Merkle-Hellman knapsack cryptosystem is a cryptographic system that was initially proposed by Merkle, and later iterated versions were both broken by Shamir and Brickell in the early 1980s and 1985, respectively. This system is related to the classical knapsack problem, subset-sum problem, and e
0 views • 18 slides
BIKE Cryptosystem: Failure Analysis and Bit-Flipping Decoder
The BIKE cryptosystem is a code-based KEM in the NIST PQC standardization process, utilizing the Niederreiter variant of the McEliece Construction with a QC-MDPC code. It ensures security against IND-CPA, and efforts are made to further confirm or disconfirm its estimates for IND-CCA security requir
1 views • 14 slides
Cryptology System Design Fundamentals: ARSA Cryptosystem Examination Solutions
The given content discusses the solution to an ARSA cryptosystem final examination design problem, involving the computation of public and secret keys for users A and B, encryption and signing of messages, and considerations for attacker interceptions and computations. The solution guides through th
0 views • 18 slides
Insights into the Rowhammering.BIKE Cryptosystem and Decoding Strategies
Explore the Rowhammering.BIKE cryptosystem, its parameters, and the black-grey flip decoder. Learn about the bitflipping algorithm, prior analysis of DFR in QC-MDPC decoders, and strategies for key recovery and decoding in this innovative system. Discover how understanding the error patterns related
0 views • 7 slides
Leonard Max Adleman
Leonard Adleman, co-inventor of the RSA cryptosystem, has significantly influenced the fields of cryptography and DNA computing. His innovative contributions, such as public-key encryption and DNA computation, have shaped modern technology. Adleman's unique journey from mathematics to molecular biol
0 views • 6 slides
Parameters of Classic McEliece Cryptography
Post-Quantum cryptography is at the forefront of technological advancements, with the Classic McEliece cryptosystem being a notable player in this field. The presentation discusses the adaptation of Classic McEliece parameters for efficient memory usage, presented at the Institute of Cybersecurity i
0 views • 37 slides
Design of Elliptic Curve Cryptosystem with Register Bank Overview
Explore the design aspects of an Elliptic Curve Cryptosystem, focusing on the Register Bank overview featuring Processor, Arithmetic Unit, and Control Unit. Learn about the organization of register banks and the functionality of distributed RAMs in Xilinx FPGAs for efficient data storage and retriev
0 views • 25 slides
Elliptic Curve Cryptosystem Design Overview
Explore the design hierarchy and parameters of an Elliptic Curve Cryptosystem, including details on the field characteristic, random curves, base points, and code structure. Dive into modules like the multiplier and Karatsuba Multiplier, understanding the operation on bit inputs and outputs. Enhance
0 views • 20 slides
FPGA-based Key Generator for Niederreiter Cryptosystem Using Binary Goppa Codes
Learn about an FPGA-based key generator designed for the Niederreiter Cryptosystem using Binary Goppa Codes, developed by Wen Wang, Jakub Szefer, and Ruben Niederhagen from Yale University and Fraunhofer Institute SIT. Explore modules, parameters, coding theory, and the key generator algorithm for t
0 views • 15 slides
Mathematical Model of Disymmetric Bigram Cryptosystem Development
Explore the development of a mathematical model for a disymmetric bigram cryptosystem using parametric solutions of multi-degree Diophantine equations. Learn about the Diophantine equation system, solutions properties, and parameterization method for multi-degree systems. Dive into the proposed cryp
0 views • 9 slides
Introduction to Cryptosystems and RSA Public Key Cryptosystem
Explore the fundamentals of cryptosystems, including encryption, decryption, and the RSA public key cryptosystem. Delve into the concept of secret codes, unforgeable signatures, and coin flipping on the phone. Understand the setup of receivers and the encryption and decryption processes involved in
0 views • 19 slides
Knapsack Cryptosystem and Weakness: A Comprehensive Overview
Explore the concept of the knapsack problem, including the superincreasing knapsack (SIK) and general knapsack (GK). Learn how the knapsack cryptosystem works, its encryption methods, weaknesses, and historical vulnerabilities. Discover the trapdoor in the cryptosystem and the importance of secure e
0 views • 14 slides