Automatic Incremental View Maintenance in DBSP: A Comprehensive Overview
Analyzing the automatic incremental view maintenance for rich query languages like DBSP. Discussing concepts such as incremental computation reuse, streaming language, relational computations, streaming operators, and more. Explore the conversion of arbitrary DBSP programs to incremental ones and th
4 views • 24 slides
Understanding Language in Stoicism: Significance and Corporeality
Language in Stoicism plays a crucial role in the process of assenting to impressions by focusing on corporeality, reason, and truth. It distinguishes between the mundane vocal sounds, articulated speech, and significant language to convey meanings effectively. The significance of language lies not i
2 views • 13 slides
Fully Homomorphic Encryption: Foundations and Applications
Fully Homomorphic Encryption (FHE) allows computations on encrypted data without decrypting, enabling secure outsourcing of computations to untrusted servers. FHE involves key generation, encryption, homomorphic evaluation, and decryption processes. It ensures correctness, security, and compactness
0 views • 31 slides
Analysis of "The Man He Killed" by Thomas Hardy and Its Historical Context
Thomas Hardy's poem "The Man He Killed" explores the senseless nature of war through the perspective of a soldier who reflects on killing an enemy soldier whom under different circumstances, they could have shared a drink with. Set during the Second Boer War, the poem highlights the arbitrary nature
0 views • 12 slides
Various Definitions of Language Throughout Linguistic History
Different linguists and scholars have offered various definitions of language over time. Sapir (1921) emphasized language as a method of communicating ideas, emotions, and desires through voluntary symbols. Bloch and Trager (1942) focused on the social aspect of language as a system of vocal symbols
1 views • 12 slides
Rights of Arrested Persons: Ensuring Justice and Fair Treatment
The Constitution of India guarantees fundamental rights to arrested individuals, including the right to information, legal representation, timely production before a magistrate, and protection against prolonged detention without judicial oversight. Additional rights cover the grounds of arrest, safe
2 views • 10 slides
Understanding Differential Equations in Economics Honours
Differential equations, introduced by Newton and Leibniz in the 17th century, play a key role in economics. These equations involve derivatives and represent implicit functional relationships between variables and their differentials, often related to time functions. The order and degree of a differ
1 views • 16 slides
Amendment Process in the Indian Constitution: Overview and Procedure
Amending the Indian Constitution is a crucial process outlined in Article 368. It is designed to maintain the sanctity of the Constitution and prevent arbitrary power. The process involves introducing a Bill, passing it with required majorities in both Houses of Parliament, ratifying by state legisl
2 views • 7 slides
Creating a Culture of Accountability in the Federal Workplace
Explore the importance of ethics and accountability in the Federal workplace, focusing on core values, merit system principles, and standards of ethical conduct for all employees. Emphasizing fairness, integrity, and protection against arbitrary actions and political favoritism, the content advocate
0 views • 22 slides
Evolution and Criticisms of the Rule of Law
The rule of law, originating from classical Greece and emphasized throughout history, ensures equality before the law and limits arbitrary power. A.V. Dicey's three principles summarize this concept, emphasizing accountability for all, including government officials. While criticized for its limitat
0 views • 9 slides
Guidelines for Inmate Searches and Facility Security
Inmate searches in correctional facilities are essential for safety and security. This includes procedures for clothed and unclothed body searches, contraband definition, cell search methods, and facility search reasons. The guidelines emphasize conducting searches respectfully and professionally to
3 views • 47 slides
Understanding and Pursuing Grievances in Union Representation
This informative material covers essential topics related to preparing and pursuing a grievance in the context of union representation, including the duty to fairly represent the entire bargaining unit, defining terms like arbitrary, discriminatory, and bad faith, obligations in filing grievances, g
0 views • 16 slides
Uniqueness of Human Language and Communication Contrasted with Animal Communication
Human language possesses unique properties such as reflexivity, displacement, and arbitrariness, setting it apart from animal communication. These distinctions enable humans to communicate abstract concepts, discuss past and future events, and use arbitrary linguistic forms. The contrast between hum
1 views • 17 slides
Understanding Fauvism: Working with Colors and Color Schemes
Fauvism is an art movement known for its bold and arbitrary use of colors. Fauvist painters carefully selected colors to convey specific moods in their artworks. This guide explores Fauvism, color theory, and different color schemes to help you create your own expressive painting. Learn about comple
0 views • 8 slides
Computing Triplet and Quartet Distances Between Evolutionary Trees
Study on computing triplet and quartet distances in evolutionary trees, comparing rooted vs. unrooted, binary vs. arbitrary degree trees. Discusses algorithms, experimental results, and evolutionary tree construction methods. Includes analysis on cultural phylogenetics and evolutionary tree comparis
0 views • 27 slides
Geometric Routing Concepts and Byzantine Fault Tolerance
Geometric Routing enables routing without overhead, where each node knows its global coordinates and forwards messages based on proximity to the destination. Byzantine Faults pose challenges with arbitrary node behavior, but a Byzantine-Robust Geometric Routing algorithm addresses this in a 3-connec
2 views • 33 slides
Robust Parity Test for Extracting Parallel Vectors in 3D
Fundamental primitives for visualizing 3D data include line features like ridges and valleys of a scalar field, stream lines of a vector field, vortices of a velocity field, and extremal curves of a tensor field. Parallel Vectors (PV) provide a unified representation of 3D line features, forming con
0 views • 27 slides
Observational Constraints on Viable f(R) Gravity Models Analysis
Investigating f(R) gravity models by extending the Einstein-Hilbert action with an arbitrary function f(R). Conditions for viable models include positive gravitational constants, stable cosmological perturbations, asymptotic behavior towards the ΛCDM model, stability of late-time de Sitter point, a
1 views • 12 slides
Programmable Parser and Header Definitions at University of South Carolina
Programmable parsers and custom header definitions play a crucial role in network packet processing. This presentation by Jorge Crichigno at the University of South Carolina covers topics such as parser operation, predefined states, and header formats. The content delves into the capabilities of pro
1 views • 22 slides
Breakdown: Linear-time and Field-agnostic SNARKs for R1CS
Breakdown discusses linear-time and field-agnostic SNARKs for R1CS, focusing on achieving fast prover speeds and supporting circuits over arbitrary finite fields. SNARKs offer efficient proof systems with sub-linear proof sizes and verification costs. The work aims to eliminate the need for FFT-frie
0 views • 28 slides
Understanding Judicial Review in Administrative Law
In this chapter, the concept of judicial review in administrative law is explored, focusing on the scope of review set by Congress, including trial de novo and independent judgment on evidence. Different standards of review, such as clearly erroneous and substantial evidence, are discussed, highligh
0 views • 23 slides
Understanding Substance-Free Phonology and Its Implications
Substance-free phonology, as discussed by Tobias Scheer, explores the distinction between phonologically meaningful and meaningless items, highlighting their production and phonetic correlates. The article emphasizes the non-arbitrary nature of meaningful items and the arbitrary interchangeability o
0 views • 30 slides
Understanding Arbitrary and Capricious Review in Administrative Law
Arbitrary and Capricious Review refers to a highly deferential standard applied to agency decisions, requiring agencies to demonstrate compliance with statutory requirements. The landmark case of Citizens to Preserve Overton Park v. Volpe set the precedent for a thorough judicial review based on the
0 views • 8 slides
Efficient Support for Synchronization Without Invalidations
Addressing complex software issues like data races and inefficiencies in hardware synchronization, the DeNovoSync solution provides efficient support for arbitrary synchronization without writer-initiated invalidations. By introducing disciplined shared memory with structured synchronization and exp
0 views • 40 slides
Exact Correlation Models in Biscalar Fishnet Theory
In the study of biscalar fishnet models, various operators and spectra were explored, leading to findings on exact correlation functions, strong coupling regimes, Regge limits, and more in arbitrary dimensions. The investigation delves into Lagrangian formulations, graph-building operators, conforma
0 views • 15 slides
Basics of Compass Surveying and Magnetic Bearings
Compass surveying involves the use of compasses to determine directions and bearings during surveying activities. This method utilizes tools like prismatic compasses and magnetic needles to establish true and magnetic meridians, as well as arbitrary and grid meridians. Understanding concepts like wh
0 views • 17 slides
Investment Arbitration: Challenges and Solutions
Legal frameworks, international investment agreements, and investor-state arbitration play crucial roles in regulating foreign investments and resolving disputes. Issues such as arbitrary expropriation and the parallel rise in disputes are addressed through mechanisms like ISDS to ensure fairness an
0 views • 15 slides
Understanding Cryptographic Hash Functions
Cryptographic hash functions play a crucial role in various aspects of security, including integrity protection, checksum generation, password hashing, digital signatures, and more. They are designed to efficiently convert input data of arbitrary length into fixed-length output, aiding in tasks like
0 views • 32 slides
Program Verification Using Templates Over Predicate Abstraction
This research explores a technique that allows for inferring invariants with arbitrary quantification and boolean structure, improving the state-of-the-art in program verification. It can infer weakest preconditions, helping with debugging and analysis by discovering worst-case inputs and missing pr
0 views • 32 slides
Mill on Liberty and State Interference: Principles and Limits
John Stuart Mill's work delves into the principles of civil and social liberty, addressing the limits of state interference on individual freedoms and the influence of societal pressures. He emphasizes the necessity of protecting against tyranny, including the tyranny of the majority, and the import
0 views • 23 slides
Effective Email Management and Records Retention Guidelines
This document provides guidelines for effective email management and records retention, emphasizing the importance of classification, storage, and disposition in accordance with business, legal, historical, and financial requirements. It highlights the need for users to apply retention policies/tags
0 views • 22 slides
Understanding a Human Rights-Based Approach to Law and Policy Making
This informative content discusses the importance of a human rights-based approach in law and policy making, particularly focusing on the protection and assistance of Internally Displaced Persons (IDPs). It explores international legal standards, the Guiding Principles, the Kampala Convention, and t
0 views • 14 slides
Understanding Stack Protection and Exploitation Techniques
Delve into the world of stack protection and exploitation, covering topics like exploiting arbitrary write, issues with stack canaries, and shadow stack usage. Explore defense mechanisms like Stack Cookie and learn about the power of exploiting vulnerabilities to write arbitrary memory. Discover met
0 views • 23 slides
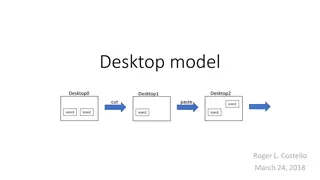
Modeling Desktops and Software Operations
Explore the process of modeling desktops and software operations, including adding, removing, cutting, and pasting icons. Learn about creating versions of models with hardcoded icons or arbitrary sets. Dive into the ordering of desktops and the utilization of icons A and B in the model.
0 views • 18 slides
Understanding Principal Stresses and Strains in Mechanics of Materials
Introduction to principal stresses and strains in Mechanics of Materials, covering transformations of stress and strain, combined stress analysis, and methods to determine stress states on arbitrary planes in loaded bodies. Details stress elements, stress analysis on inclined sections, and stress di
0 views • 24 slides
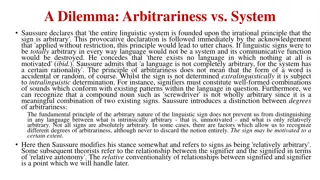
The Principle of Arbitrariness in Linguistic Signs: Saussure's Insight
Saussure's declaration on the arbitrariness of linguistic signs is thought-provoking, emphasizing that while signs are arbitrary, complete arbitrariness would lead to chaos. He distinguishes between degrees of arbitrariness and acknowledges that signs are not entirely arbitrary, being subject to lin
0 views • 9 slides
Piezotronic Effect Modelling of ZnO Nanowires Under Arbitrary Loading
Explore the multi-physics modelling of the piezotronic effect in ZnO nanowires under arbitrary loading. The research team led by Dr. M. El Hachemi presents innovative designs of micro-strain sensors and piezotronic cantilever sensors, with applications in fields like robotic manipulation and spectro
0 views • 11 slides
Overview of KBase and HTCondor Integration for Systems Biology Predictions
KBase is an open software platform for systems biology, offering predictive and design capabilities for biological functions. It integrates data and analytical tools for genomics research of microbes, plants, and their communities. HTCondor is chosen for fair queueing and resource limit settings due
0 views • 12 slides
Overview of Asynchronous MPC with Linear Communication and Optimal Resilience
Explore the concepts of Asynchronous Multiparty Computation (MPC) with Linear Communication and Optimal Resilience, discussing the model, motivation, and differences between synchronous and asynchronous protocols. The goal is to ensure correctness and privacy in a setting where parties may be corrup
0 views • 72 slides
A Human Rights-Based Approach to Law and Policy Making for Internally Displaced Persons
This comprehensive presentation covers the international legal standards, frameworks, and rights pertaining to the protection and assistance of internally displaced persons (IDPs). It emphasizes a human rights-based approach as the foundation for developing laws and policies, highlighting the import
0 views • 13 slides