Introduction to RSA Cryptography and Public Key Encryption
Explore the fundamentals of RSA cryptography and public key encryption, including shift ciphers and affine ciphers. Learn how public key encryption solves the challenges of implementing secure communication on a large scale. Discover the key components of RSA, its development history, and the mathem
7 views • 37 slides
Transposition Cipher Techniques in Modern Block Ciphers
Transposition ciphers, specifically columnar and double columnar transpositions, are explored in the context of data encryption and computer engineering at Mustansiriyah University Engineering College. These techniques involve rearranging message elements without changing their identities, providing
1 views • 4 slides
GPU Rasterization and Graphics Pipeline
Delve into the world of GPU rasterization, from the history of GPUs and software rasterization to the intricacies of the Quake Engine, graphics pipeline, homogeneous coordinates, affine transformations, projection matrices, and lighting calculations. Explore concepts such as backface culling and dif
1 views • 17 slides
Block Ciphers in Cryptography
Explore the principles of block ciphers in modern cryptography, focusing on the Data Encryption Standard (DES) and its design principles. Learn about block cipher encryption, Feistel block cipher structure, n-bit block ciphers, ideal block ciphers, key length considerations, and challenges with idea
1 views • 44 slides
Sequence Alignment and Scoring Matrices
In this content, we dive into the fundamentals of sequence alignment, Opt score computation, reconstructing alignments, local alignments, affine gap costs, space-saving measures, and scoring matrices for DNA and protein sequences. We explore the Smith-Waterman algorithm (SW) for local sequence align
1 views • 26 slides
Symmetric Key Block Ciphers - Overview and Implementation
Delve into the world of symmetric key block ciphers through a detailed exploration of classical ciphers like substitution and transposition, modern cryptography advancements, DES encryption, Simplified DES, key scheduling, expansion functions, S-Box usage, and more. Discover the intricacies of encry
1 views • 40 slides
Encryption Techniques: From Transposition Ciphers to Rail Fence Ciphers
Explore the world of encryption techniques, diving into transposition ciphers and rail fence ciphers. Learn about encryption, decryption, plaintext, ciphertext, keys, and the art of secret writing. Discover how transposition ciphers reorder letters without changing their values and how rail fence ci
0 views • 26 slides
Exact Solutions in Cosmological Models Based on Teleparallel Gravity
Precision in cosmological models based on teleparallel gravity is explored, including fundamental theories, modifications, and applications in the context of General Relativity. The construction principles of GR modifications, characteristic tensors, relation between different metric-affine geometri
0 views • 17 slides
Overview of Modern Cryptography and Data Encryption Standard (DES)
Exploring modern cryptography including symmetric key block ciphers, public key ciphers, stream ciphers, and post-quantum ciphers. Focus on Data Encryption Standard (DES), Simplified DES, Feistel cipher, key schedule, expansion function, S-Box, DES encryption, and decryption processes.
1 views • 37 slides
Public Key Cryptography in Network Security
Explore the concepts of public key cryptography, key distribution challenges, solutions to secret key schemes, and the importance of secure communication in network security. Learn about cryptology, cryptography, cryptanalysis, block ciphers, stream ciphers, and more in this informative content.
0 views • 21 slides
Crack the Code: A Journey into Transposition Ciphers
Mathematicians play a crucial role in industries like telecommunications and internet companies by condensing data and ensuring error detection. Transposition ciphers, like the Scytale used by Romans, offer a challenging way to encrypt messages. Test your skills with code-breaking challenges and exp
1 views • 4 slides
Affine Difference Equations and Long-Term Behavior
Exploring different slopes in affine difference equations and their impact on the behavior of solutions. Discover how iterating with points relative to fixed points reveals attracting or repelling characteristics. Gain insights into the convergence or divergence of sequences in relation to fixed poi
1 views • 8 slides
Lightweight Cryptography: Key-Reduced Variants and Beyond-Birthday-Bound Security
Lightweight cryptography has emerged as a hot research topic in the past two decades, with over 60 ciphers proposed. This includes examples like PRESENT, GIFT, SIMON/SPECK, and more. Authenticated encryption through CAESAR and NIST LWC plays a vital role, with ASCON and ACORN leading the lightweight
1 views • 25 slides
Introduction to Traditional Ciphers: Columnar Transpositions
Traditional ciphers such as Columnar Transpositions involve rearranging plaintext letters based on a fixed number of columns. This technique enhances security by incorporating a keyword for encryption and decryption. Learn about the process and examples of implementing Columnar Transpositions in thi
0 views • 8 slides
Block Ciphers in Cryptography
Explore the world of block ciphers in cryptography through topics such as distinguishing attacks, key-recovery attacks, designing paradigms like Substitution-Permutation Networks (SPNs) and Feistel networks, concrete security considerations, confusion/diffusion principles, attack models, and more.
0 views • 27 slides
Comprehensive Overview of Encryption Techniques and Algorithms
Explore the world of encryption with insights into symmetric and public key encryption, certificate authorities, secure sockets layer, substitution ciphers, block ciphers, AES, and public key cryptography. Delve into the intricacies of encryption keys and algorithms, including the AES process, Diffi
0 views • 31 slides
Stream Ciphers
Stream ciphers are cryptographic algorithms used to encrypt individual bits, offering speed and efficiency. Learn about symmetric ciphers, encryption processes, synchronous vs. asynchronous stream ciphers, and key stream generation. Explore the evolution of stream ciphers in the field of cryptology,
0 views • 32 slides
Modes of Encryption and CCA Security Overview
An overview of various modes of encryption, including stream ciphers and block ciphers, along with a discussion on Chosen Ciphertext Attacks and CCA Security. The content covers the goals of the day, examples of attacks, and definitions related to CCA-Security. It explains how CPA-Security differs f
0 views • 24 slides
Cryptography
Cryptography is the art of securing communication through the use of codes and ciphers. This overview covers fundamental concepts such as symmetric and asymmetric cryptography, hashes, attacks on cryptography, and best practices. Understand the terminologies in cryptography, the use of keys, and the
0 views • 63 slides
Cryptography: Modern Symmetric Ciphers
Explore the world of modern symmetric ciphers used in network security, from encryption basics to advanced techniques like Block vs. Stream Cipher and Autokeyed Vigenere Cipher. Understand the importance of encryption in providing protection for confidentiality, authentication, integrity, and non-re
0 views • 60 slides
Public-Key (Asymmetric) Ciphers
Principles and significance of public-key cryptography, including its motivation, trapdoor one-way functions, and the issues with symmetric-key ciphers. Learn about asymmetric ciphers, key distribution problems, and the use of prime numbers in encryption.
0 views • 31 slides
Modern Cryptography: Algorithms and Their Applications
Cryptography involves securing and transmitting information through various techniques like encryption, decryption, and cipher text. It encompasses different security types, including communication security and transmission security. The history of cryptography systems is rich, spanning from letter
0 views • 26 slides
Efficient Strategies in Geometric Algorithms
Strategy optimization in geometric algorithms focusing on guessing a hidden card, data querying for quick retrieval, and intersection algorithms for polygons and polytopes in 2D and 3D spaces. Discussion on polygon representation, affine transformations, and convexity invariance.
0 views • 14 slides
Affine Transformers Abstraction Framework
This content introduces a new abstraction framework for affine transformers, exploring abstract domains and semantics to analyze program invariants. It discusses the motivations behind proving program assertions sound with respect to bitvectors and presents new abstract domains for disjunctions over
0 views • 36 slides
Modern CPU Core Architecture Implications on Software Performance
Delve into the intricacies of modern CPU core architecture, including superscalar design, branch prediction, out-of-order execution, memory hierarchy, and their impact on software performance. Explore concepts like data dependence, loop optimizations, affine expressions, and affine loops.
0 views • 18 slides
Modern CPU Core Architecture: Superscalar, Branch Prediction, Out-of-Order Execution
This review delves into the advanced features of modern CPU cores including superscalar pipelines, branch prediction, out-of-order execution, and sophisticated memory hierarchies. Explore the implications of these architectural elements on software performance, focusing on concepts like temporal and
1 views • 16 slides
Understanding Block Ciphers in Cryptography
Delve into the realm of block ciphers, essential cryptographic tools used for securing data. Explore the history of DES, Feistel networks, key expansion, round functions, performance comparisons between stream and block ciphers, and the core concepts behind block ciphers like DES and AES.
0 views • 57 slides
Cryptography Evolution and Historical Cipher Systems
Explore the evolution of cryptography from Julius Caesar's Caesar Cipher to complex cryptographic systems used during the American Civil War. Understand the basics of symmetric key algorithms and the vulnerabilities of early ciphers. Dive into the significance of historical milestones in cryptograph
0 views • 58 slides
Cryptography Techniques: Caesar, Shift, and Affine Ciphers Explained
Explore classical cryptography methods including the Caesar cipher, shift cipher, and affine ciphers. Learn how these encryption techniques work and how to encrypt and decrypt messages using them.
0 views • 19 slides
Efficient Masked Ciphers Cryptanalysis 2020 Insights
Explore cutting-edge research on efficient masked ciphers cryptanalysis, including second-order secure threshold implementations, probing adversaries, and advancements in achieving second-order secure round functions. Discover innovative techniques such as non-completeness over stages, pairing maske
0 views • 16 slides
CS255 Winter 2025 Recap: Block Ciphers and AES Encryption
Explore the fundamentals of block ciphers and AES encryption in CS255 Winter 2025 with Dan Boneh from Stanford University. Learn about key concepts such as key expansion, iteration, and the AES-NI hardware instructions for efficient encryption and decryption. Dive into how block ciphers are built by
0 views • 54 slides
Cryptanalysis Techniques for Block Ciphers
Explore the various cryptanalysis techniques used for breaking block ciphers, including statistical analysis, differential cryptanalysis, linear cryptanalysis, and more. Learn about attack scenarios, key schedule cryptanalysis, and side-channel cryptanalysis methods to understand how encryption sche
0 views • 8 slides
Cryptography and Network Security with Block Ciphers and Stream Ciphers
Explore the fundamentals of cryptography and network security as outlined in "Cryptography and Network Security Sixth Edition" by William Stallings. Learn about block ciphers, data encryption standards, stream ciphers, and the importance of encryption in secure communication protocols.
0 views • 24 slides
Game Theory Applications in Computer Networks: Efficiency and Equilibrium Analysis
Explore the intriguing concepts of equilibrium and efficiency in computer networks through game theory, examining scenarios with affine cost functions, potential-based social cost bounds, and the impacts on loss of efficiency. Discover insights into Price of Anarchy, Price of Stability, and Loss of
0 views • 57 slides
Understanding Transformations in Mathematics
Explore the world of transformations with topics like rotations, reflections, rigid body motions, orthogonal matrices, parameterizing rotations in 3D, and more. Learn about affine transformations and their definitions, and delve into the application of matrix exponential in solving differential equa
0 views • 23 slides
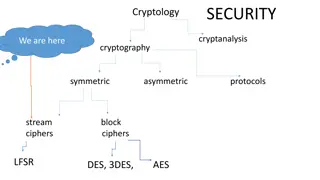
Cryptography and Block Ciphers: Understanding LFSR, DES, 3DES, AES
Explore the world of cryptology, cryptanalysis, symmetric, and asymmetric cryptography. Dive into the concepts of stream and block ciphers, LFSR, DES, 3DES, and AES encryption algorithms. Learn about key lengths, cycle lengths, and the security aspects of cryptographic systems.
0 views • 29 slides
Diversity in Scoring Matrices and Protein Function Analysis
Explore the impact of affine gap penalties and substitution errors in scoring matrices, with a focus on DNA structure and scoring. Understand the nuances of nucleotide substitutions and the importance of penalizing transversions over transitions. Delve into the intricacies of scoring proteins and th
0 views • 24 slides
Optimizing Loop Structures in Affine Loops: An Overview
Learn about dependence analysis in affine loops and various transformations like reordering, scalar replacement, normalization, and more to optimize loop structures for improved program efficiency and locality in dependence. Explore unimodular transformations for legal loop changes.
0 views • 25 slides
IEEE 802.15-15-0577-00-0008 Security Protocol Overview
Explore the security aspects of PAC devices as discussed in the IEEE 802.15-15-0577-00-0008 document submitted by Marco Hernandez, Huan-Bang Li, Igor Dotli, and Ryu Miura from NICT. Delve into key elements like key establishment, authentication, encryption, integrity, and the choice between block ci
0 views • 15 slides
Stream Ciphers, Random Numbers, and RNG in Cryptography
Explore the importance of random numbers in cryptography, the use of stream ciphers, and the generation of true random and pseudorandom numbers. Learn about natural random noise sources, published sources, and the challenges of creating secure pseudorandom number generators.
0 views • 20 slides